Definition – What Is SSL Inspection?
SSL inspection is the process of examining the content of encrypted internet traffic. With almost everything online secured using protocols like SSL (Secure Sockets Layer) and its successor, TLS (Transport Layer Security) these days, a question arises: how do we ensure our online journeys remain safe if even security measures are encrypted?
With almost 95% of websites on Google using HTTPS and browsing time heavily skewed towards secure connections (90% on Chrome, 95% on Android, and 97% on Windows), traditional security measures can be rendered blind. This is where SSL inspection comes into play.
The Security Challenge of Encrypted Traffic
Basically, when you try to visit a website over HTTPS (the little padlock icon in your browser), your traffic is encrypted from start to finish so no one can snoop on it in transit. However, this encryption also creates a blind spot for security measures – they can’t see what’s hidden inside the encrypted data.
Well, SSL/TLS inspection is kind of like the network admin saying, “Yeah, that’s good, but I’m gonna take a peek anyway.” SSL inspection essentially acts as a decoder. It intercepts the encrypted traffic and uses special tools to decrypt it, revealing the underlying content. This way, security systems can scan for malicious activity hidden within the data, such as malware, viruses, or phishing attempts.
For websites the appliance doesn’t control, it generates its own SSL/TLS certificate and tricks client devices into trusting this certificate through pre-installed root certificates.
Now why is SSL Inspection so important? A few key reasons:
- It lets organizations regain visibility into those encryption blindspots to hunt for threats.
- Zero encryption = zero chance of catching malware or hackers piggybacking on those encrypted pipes.
- For places like companies and schools, it ensures encrypted traffic follows all IT policies and doesn’t leak sensitive data.
- Allows comprehensive security monitoring without blind spots
- Builds trust and confidence in online transactions and communications.
- Allows enforcement of organizational security policies and content filtering.
- Ensures compliance with industry regulations and data protection laws.
Sure, the whole man-in-the-middle decryption thing has privacy debates. But from a security viewpoint, SSL inspection is quickly becoming a must-have to balance encryption’s amazing privacy benefits with the need to protect networks from sneaky cyber badness.
Methods of SSL Inspection: Different Approaches to Decryption

There are two primary methods for conducting SSL inspection, each with its own advantages and drawbacks:
Inline Inspection
Function: This method operates in real-time, acting like a security checkpoint on a highway for data. As encrypted traffic flows through the network, an SSL inspection tool (like a firewall) intercepts it. The tool then uses its decryption capabilities to unveil the content for security analysis. Once deemed safe, the content is re-encrypted and sent on its final journey.
Benefits:
- Faster response times: Threats are identified and neutralized as they occur.
- Ideal for real-time protection: Well-suited for scenarios where immediate threat detection is critical.
Drawbacks:
- Resource-intensive: Decryption and re-encryption require significant processing power, potentially impacting network performance.
- Increased latency: Delays may be introduced, especially with complex inspections.
Offline Inspection:
Function: This method takes a more deliberate approach. Encrypted traffic is captured and stored for later analysis. Security personnel can then decrypt the captured data at their convenience and meticulously examine it for malicious content. After a clean bill of health, the content is re-encrypted and delivered to its destination.
Benefits:
- Lower resource consumption: Network performance remains unaffected as decryption doesn’t happen in real-time.
- Thorough analysis: Allows for in-depth inspection with more sophisticated tools.
Drawbacks:
- Delayed threat detection: Potential threats might go unnoticed until the captured data is analyzed.
- Storage requirements: Significant storage space might be needed to hold captured encrypted traffic.
Implementation Techniques for SSL Inspection:
The two primary methods we discussed earlier (Inline and Offline) can be implemented using various techniques. Here’s how:
Next-Generation Firewalls (NGFWs)
These advanced firewalls often have built-in SSL inspection capabilities. They can function in inline mode, acting as the intermediary device that decrypts, inspects, and re-encrypts traffic in real-time.
Proxies
Organizations can leverage dedicated proxy servers for SSL inspection. These proxies act as a middleman between the client and server, establishing separate connections with each. The proxy can then decrypt the traffic flowing through these connections for security analysis before forwarding it onward. This approach often falls under the umbrella of inline inspection.
TAP Mode
This technique involves copying the encrypted traffic stream as it flows through the network. This copied data can then be analyzed offline using dedicated security tools. This essentially leverages the offline inspection method but with a specific way of capturing the traffic data.
How SSL Inspection Works: A Behind-the-Scenes Look
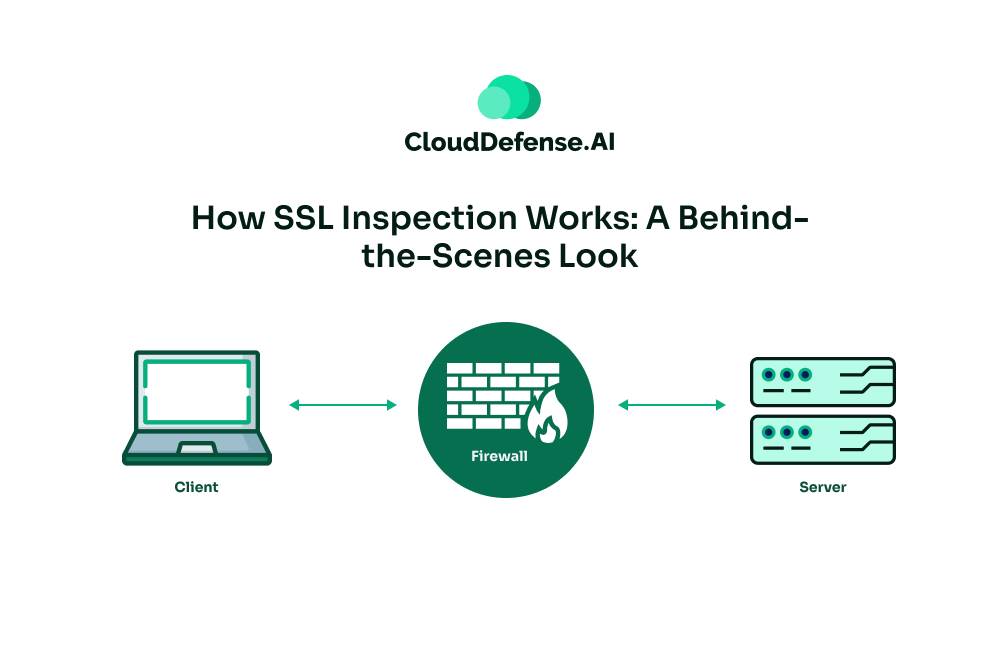
Traffic Interception
Imagine you’re online, casually browsing your favorite shopping website over that secure HTTPS connection. Behind the scenes, all that encrypted data passing between your browser and the website has to go through a certain checkpoint – let’s call it the network’s security firewall. This firewall acts like a strict bouncer, pulling aside every single encrypted packet for inspection before allowing it to proceed.
Decryption
Now, normally that encrypted data is totally scrambled and unreadable. But the firewall has a nifty trick up its sleeve – it holds the master key that can decrypt any of those encrypted communications. It’s like having a super password that unlocks every sealed internet package. With this key, the firewall can easily unscramble and peek at the actual contents inside the encrypted traffic.
Security Scan
So with the data now decrypted and out in the open, the firewall gives it a thorough scan and pat-down. It runs fancy security checks, looking for anything suspicious or dangerous trying to sneak through. This could be malware hiding in downloadable files, phishing attempts disguised as legit links, or any other digital contraband that violates network policies.
Re-encryption and Delivery
If the decrypted contents get the all-clear from security, the firewall re-encrypts and reseals that data back up using those master decryption keys we talked about earlier. So from the outside, it still looks like an ordinary encrypted data package. Only then is the re-encrypted traffic allowed to continue its journey to the intended website’s server.
Potential Drawbacks of SSL Inspection
While SSL inspection offers a powerful shield against online threats, it’s not without its downsides. Here are some potential drawbacks to consider:
Performance Impact: The decryption and re-encryption process inherent in SSL inspection can add an extra layer of complexity to data transfer. This can lead to slight delays in your browsing experience, especially with resource-intensive inspections. Imagine a security checkpoint with long lines – it slows things down.
Security Concerns: The introduction of an intermediary device (like a firewall) for decryption raises security questions. If this device is compromised, the decryption keys could fall into the wrong hands, potentially exposing the very data it’s meant to protect. Think of trusting someone to hold your house keys – a risk if not done right.
Privacy Issues: SSL inspection essentially involves peeking into the supposedly private conversations happening online. While the goal is security, some users might find it intrusive, especially for sensitive communications. Imagine someone reading your sealed letters – a privacy violation if not necessary.
Legal and Regulatory Considerations: Depending on the location and industry, there might be legal or regulatory restrictions on implementing SSL inspection. Imagine crossing borders with certain items – some might be prohibited.
Final words
We hope this article has shed light on SSL inspection. As you can see, it’s a double-edged sword. While it empowers us to peer behind the encrypted curtain and identify hidden threats, it also raises privacy concerns and introduces potential performance impacts.
It’s important to weigh the benefits and drawbacks of SSL inspection before deploying it. For some, the enhanced security outweighs the potential downsides. However, for others, a privacy-focused approach with alternative security measures might be a better fit.







