What is the MITRE ATT&CK Framework?
The MITRE ATT&CK Framework (Adversarial Tactics, Techniques, and Common Knowledge) is a comprehensive database that categorizes and describes the tactics and techniques used by cybercriminals and state-sponsored hackers to infiltrate systems and networks. It serves as a detailed playbook for understanding the strategies threat actors use in real-world attacks.
Origins of the Framework
- Development: The MITRE ATT&CK Framework was developed by MITRE Corporation, a nonprofit organization that works closely with the U.S. government on cybersecurity and other technological challenges.
- Purpose: It originated in 2013 as a way to study and categorize cyberattacks based on real-world observations. MITRE analysts reviewed forensic data, threat reports, and cyberattack case studies to understand how attackers operate step-by-step.
- Launch: The framework was first released in 2015, focusing solely on tactics targeting Windows systems.
Growth and Evolution
Since its release, the MITRE ATT&CK Framework has significantly expanded to cover a variety of platforms and environments, including:
- Operating Systems: Windows, Linux, and macOS.
- Cloud Systems: Public, private, and hybrid cloud environments.
- Mobile Devices: Tactics and techniques specific to Android and iOS.
- Industrial Control Systems (ICS): Used in critical infrastructure like power plants and manufacturing facilities.
Real-World Insights
One of the key strengths of ATT&CK is its foundation in real-world data. The framework is built by analyzing actual cyberattacks carried out by known threat groups such as:
- APT28 (Fancy Bear): A Russian state-sponsored hacking group.
- Lazarus Group: A North Korean cybercrime organization.
- FIN7: A financially motivated hacking group.
MITRE collaborated with private companies, government agencies, and cybersecurity firms to reverse-engineer these attacks, documenting tactics such as:
- Reconnaissance
- Initial Access
- Privilege Escalation
- Data Exfiltration
What are Tactics and Techniques in MITRE ATT&CK?
The MITRE ATT&CK Framework dissects cyberattacks into two key components: Tactics and Techniques. Understanding these distinctions is crucial for effective defense.
Tactics: The “Why” Behind the Attack

Think of Tactics as the goals or objectives an attacker wants to achieve during their intrusion. The framework outlines 14 core tactics, each representing a desired outcome in the attack lifecycle.
For example, some key Tactics defined are:
- Initial Access – How the attacker first gains a foothold in the targeted environment
- Execution – Running malicious code on victim systems
- Persistence – Maintaining access after the initial compromise
- Privilege Escalation – Obtaining higher levels of system permissions
- Defense Evasion – Avoiding or disabling security controls
- Credential Access – Stealing account login details
Techniques: The “How” of the Attack
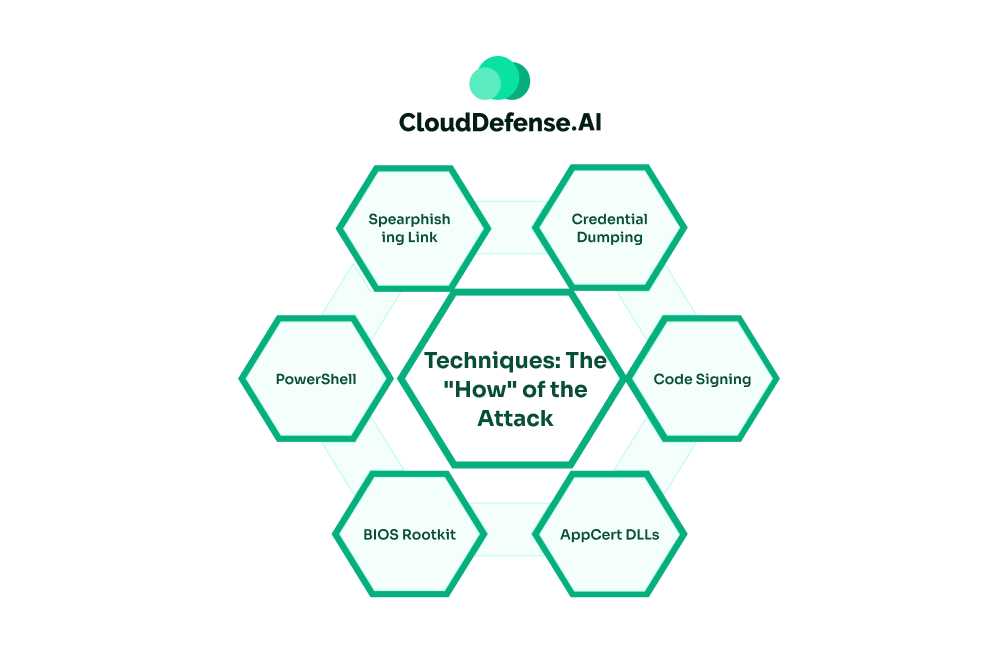
Techniques, on the other hand, delve deeper into the specific methods attackers use to achieve their tactical goals. Each tactic within the framework has numerous associated techniques, detailing how attackers might exploit vulnerabilities, steal credentials, or establish persistence on a compromised system.
Some examples of Techniques include:
- Spearphishing Link (Initial Access tactic)
- PowerShell (Execution tactic)
- BIOS Rootkit (Persistence tactic)
- AppCert DLLs (Privilege Escalation tactic)
- Code Signing (Defense Evasion tactic)
- Credential Dumping (Credential Access tactic)
Common Knowledge: Attacker assumptions about defender awareness
While not a core component, CKC plays a supporting role. It refers to the baseline knowledge attackers assume defenders possess. Understanding CKC helps defenders anticipate how attackers might exploit these known factors during an attack. This includes things like:
- Descriptions of operating system components
- Explanations of protocol functionality
- Typical network configurations
- Overviews of common utilities and tools
- High-level definitions of malware characteristics
Benefits of using the MITRE ATT&CK Framework
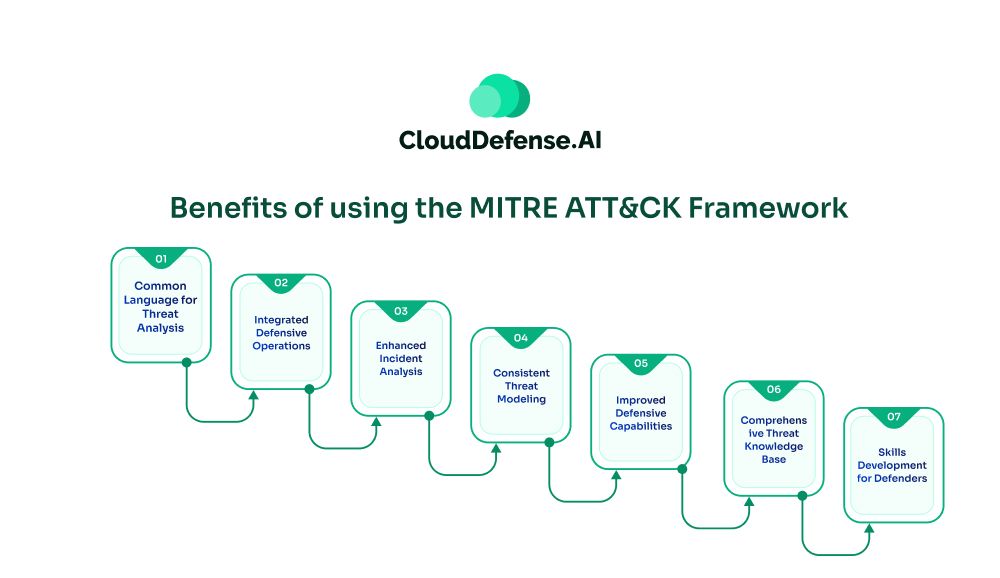
Common Language for Threat Analysis
ATT&CK provides a standardized vocabulary and structure for describing cyber threats. This enables more effective communication and knowledge sharing across teams and organizations.
Comprehensive Threat Knowledge Base
The framework catalogs an extensive range of real-world adversary tactics and techniques backed by in-depth research. It serves as a centralized repository of threat intelligence.
Improved Defensive Capabilities
Understanding the specific methods used by attackers allows defenders to better prioritize security controls, configurations, and mitigations based on the relevant threats.
Consistent Threat Modeling
ATT&CK offers a systematic approach to model and anticipate enemy behaviors, facilitating more effective defensive planning and cyber threat hunting.
Enhanced Incident Analysis
Security teams can leverage ATT&CK to methodically analyze and dissect ongoing intrusions, accurately mapping evidence to adversary tradecraft.
Integrated Defensive Operations
The matrix enables integration of ATT&CK data into defensive tools like SIEMs, IDS/IPS, EDR solutions to automate analytics and detections.
Skills Development for Defenders
The framework provides a knowledge base for training new cybersecurity personnel on adversary behaviors and effective mitigations.
Data Sources of the MITRE ATT&CK Framework
You might be wondering – how did MITRE get all this juicy insider info on what the bad guys are up to? Well, they’ve got some seriously dedicated researchers over there. The MITRE ATT&CK Framework stands strong as a result of its rich and diverse data sources. Here’s a breakdown of the key contributors:
- Publicly Available Threat Intelligence: Open-source threat intelligence feeds and research from cybersecurity experts provide valuable insights into attacker tactics.
- Incident Reporting: Real-world incident reports from organizations encountering cyberattacks offer crucial firsthand knowledge of attacker behaviors.
- Security Researcher Contributions: The cybersecurity community plays a vital role. Security analysts and threat hunters contribute their research on new and emerging attack techniques.
The Three Iterations of MITRE ATT&CK
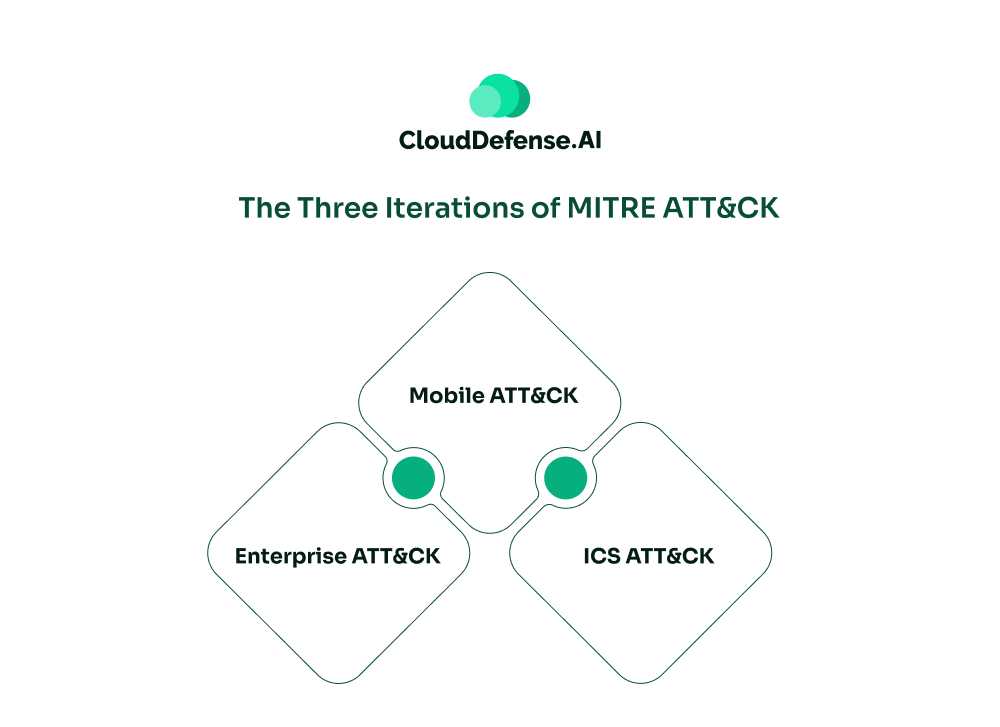
The MITRE ATT&CK Framework isn’t a one-size-fits-all solution. It recognizes the diverse landscapes defenders navigate. Here’s a quick breakdown of its three main iterations:
1. Enterprise ATT&CK: This is the most widely used version, focusing on attacks targeting enterprise networks. It covers the tactics and techniques employed against common operating systems like Windows, macOS, and Linux, along with cloud environments.
2. Mobile ATT&CK: As mobile devices become more integrated into our lives, so do mobile threats. This iteration concentrates on attack vectors specifically designed for Android and iOS platforms.
3. ICS ATT&CK: Industrial Control Systems (ICS) manage critical infrastructure. This specialized version tackles tactics targeting ICS environments, helping defenders secure these vital systems.
What is MITRE ATT&CK Matrix
The MITRE ATT&CK Framework is often visualized as a matrix, offering a comprehensive view of attacker tactics and techniques. This matrix is essentially the master database cataloging all those shady adversary behaviors and tactics. It’s laid out in a big grid, with the tactical objectives like initial access and persistence running across the top, and all the specific techniques mapped out underneath.
So for example, under the “Initial Access” tactic column, you’ll find a list of entry vectors like drive-by compromises, exploits, valid account abuse, and hardware additions. Each technique has its own entry describing exactly how attackers use that method.
The matrix also cross-references each technique against the pieces of software, protocols, and system utilities from the “Common Knowledge” base that adversaries are known to abuse or misuse while carrying out those tactics.
But it gets even more comprehensive. The ATT&CK team doesn’t just document the dry technical details. They actually provide a ton of context around each technique:
- Which specific threat groups are known to use it
- The remote access tools or malware families involved
- Mitigations and detections to look out for
- Real-world examples and case studies of that technique in action
It’s like having the ultimate encyclopedia or field manual for defending against cyber attacks. The level of detail is crazy! The official MITRE ATT&CK website provides a searchable matrix. You can filter by tactics, techniques, platforms, and data sources.
How to Leverage the MITRE ATT&CK Framework for Stronger Defenses
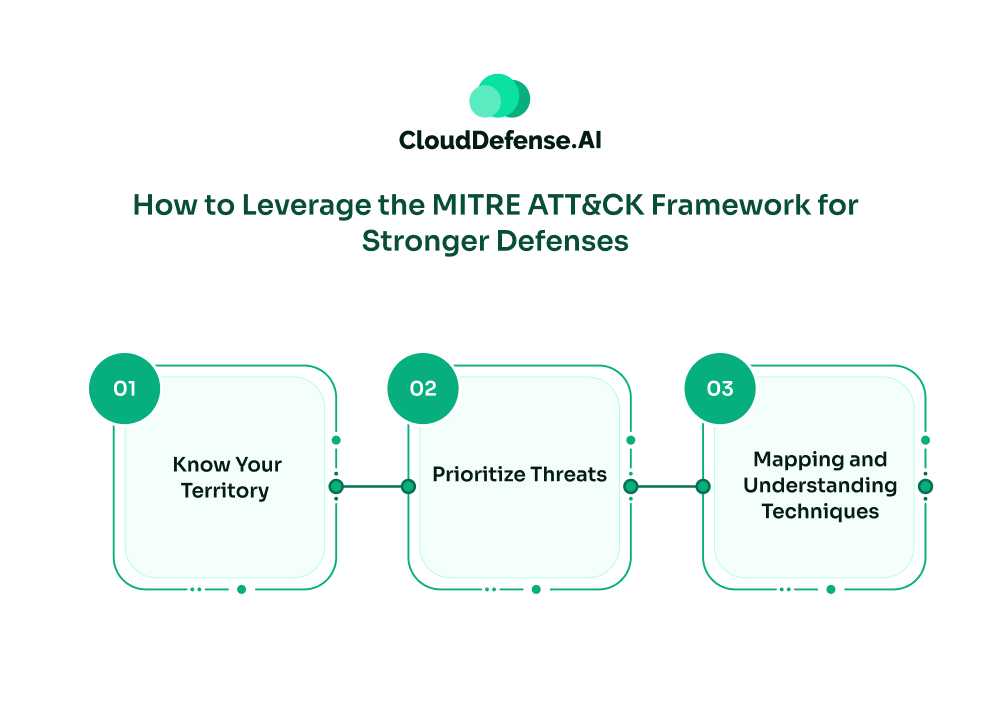
The MITRE ATT&CK Matrix can be a goldmine of information, but translating that information into actionable steps requires some planning and effort. Here’s a breakdown of how you can leverage this powerful tool:
Step 1: Know Your Territory
Before diving into the ATT&CK Matrix, it’s crucial to understand your own environment. Here’s what you need to do:
- Identify Your Assets: Take stock of everything you need to protect. This includes servers, workstations, mobile devices, and cloud environments. Having a clear picture of your attack surface is essential.
- Security Posture Check-Up: Evaluate your existing security measures. Do you have firewalls, intrusion detection systems (IDS), and endpoint protection software in place? Are they properly configured? Identifying any gaps in your defenses will help you prioritize which tactics and techniques to focus on.
Step 2: Prioritize Threats
The ATT&CK Matrix is vast, so it’s important to focus on the most relevant threats to your environment. Here’s how to narrow it down:
- Consider Industry Trends: What types of attacks are commonly seen in your industry? Are there any specific tactics that attackers favor? Understanding the threat landscape in your sector can help you prioritize effectively.
- Analyze Your Data: If you’ve experienced security incidents in the past, what tactics and techniques were used? This can be a valuable starting point for identifying areas where you might be more vulnerable.
- High-Value Assets: Focus on the tactics and techniques that pose the biggest risk to your most critical systems and data. Not all attacks are created equal, so prioritize accordingly.
Step 3: Mapping and Understanding Techniques
Once you’ve identified the tactics most relevant to your environment, it’s time to delve into the specific techniques listed in the ATT&CK Matrix for each tactic. Here’s what to explore for each technique:
- Description: Get a clear understanding of what the technique entails and how attackers use it. The more you know about how an attack works, the better equipped you are to defend against it.
- Platform Agnostic? See if the technique applies to the operating systems and environments you use. Not all techniques are relevant to all platforms, so focus on those that could potentially exploit vulnerabilities in your systems.
- How to Spot Trouble: Look for potential detection methods listed in the ATT&CK Matrix. This might involve reviewing logs, deploying specific security tools, or implementing user behavior monitoring. The goal is to identify red flags that could indicate an attacker is using a particular technique.
- Building Your Defenses: Explore mitigation strategies suggested in the ATT&CK Matrix. This could involve patching vulnerabilities, implementing stronger access controls, or user awareness training. By understanding how to mitigate these techniques, you can significantly improve your overall security posture.
Remember, It’s a Continuous Process
The MITRE ATT&CK Framework is constantly evolving as new tactics and techniques emerge. Here are some additional tips to keep in mind:
- Focus on High-Risk Techniques: Don’t try to map every single technique. Prioritize those that pose the biggest threat to your environment. There will always be new threats, so focus on what matters most.
- Regular Review and Updates: Just like fire drills, your security measures need to be tested and updated regularly. Review your mappings periodically to ensure they reflect the latest threats.
- The Power of Community: There are many online courses, tutorials, and communities dedicated to the ATT&CK Framework. Leverage these resources to deepen your understanding and stay ahead of the curve.
Bottom Line
Following these steps outlined in the article and making good use of the MITRE ATT&CK Matrix, you can gain a deeper understanding of potential attack vectors and implement targeted defenses to keep your systems secure. It’s an ongoing process, but with dedication and the right tools, you can significantly improve your cybersecurity stance.







