What is SecOps?
Do you know how sometimes the security squad and the operations crew can feel like they’re on different planets? Well, SecOps, short for Security Operations, is all about getting those two teams to stop operating in their own little silos and actually work together instead. It’s bridging that divide for some serious security gains.
Traditionally, these two groups have kind of been at odds. The security team wants to lock everything down tighter than a safe, which can mess with system performance. Meanwhile, the operations squad’s top priority is keeping everything running smoothly. See the conflict?
But SecOps changes the game by promoting a much-needed collaboration:
- It gets both teams huddling up to set security policies, implement tools, and respond to threats as a unified front.
- The security pros share their threat know-how, while ops provides the insider intel on how systems actually work. A literal mind meld of expertise.
- Processes are streamlined through automation and integrated tools, increasing efficiency and reducing human error.
The end goal? Helping organizations be proactive and agile when it comes to security:
- Shut down threats quickly: With teams sharing real-time intel, they can rapidly detect and contain any incidents.
- Reduce security risks: That unified approach helps identify vulnerabilities before the bad guys can exploit them.
- Tighten up security overall: Instead of separate plans, teams build ONE comprehensive security strategy together.
The Core Functions of a SecOps Team:
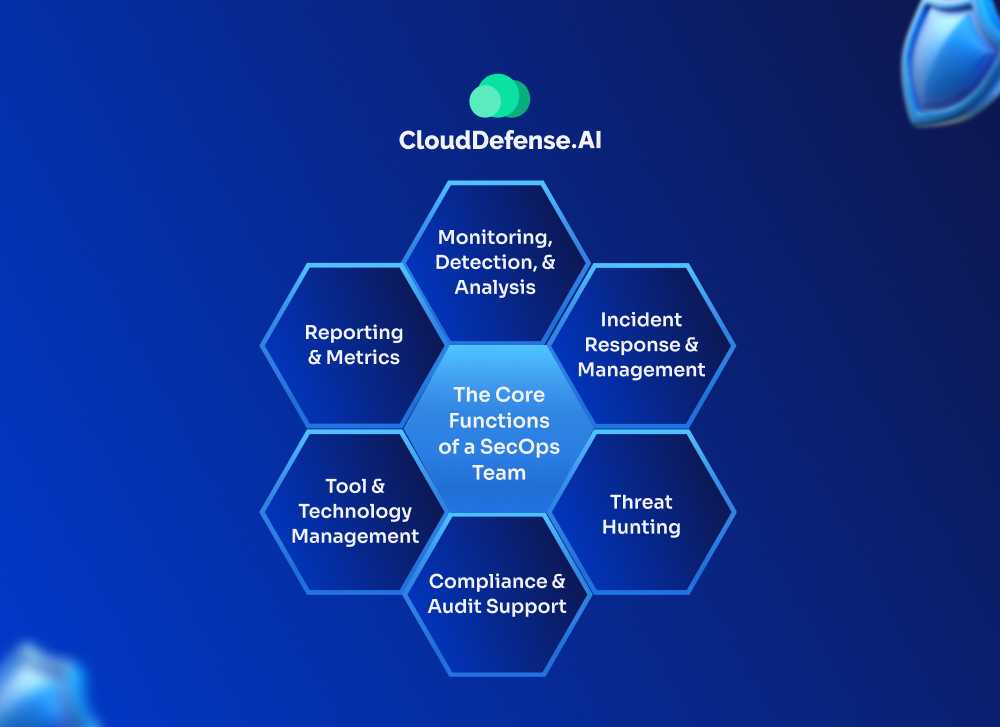
So what exactly do these SecOps crews do all day? Well, they’re the security multi-taskers, handling all sorts of vital functions:
Monitoring, Detection, & Analysis: The SecOps team should constantly keep watch over the company’s systems and network traffic using advanced security tools. If any sketchy activity is detected, they jump in to thoroughly investigate and analyze the potential threat.
Incident Response & Management: When something bad happens – a security breach or major incident – SecOps professionals spring into action as the organization’s dedicated cyber firefighters. With practiced discipline, they work to quickly contain the threat, minimize the fallout, and expertly coordinate the incident response across teams.
Threat Hunting: The team uses threat intelligence and hunts for any indications of upcoming attacks or vulnerabilities that need patching before havoc ensues.
Compliance & Audit Support: Regulations, compliance, audits – SecOps has got you covered. They team up with compliance peeps to ensure the company follows all the relevant security rules and standards.
Tool & Technology Management: With security tools like SIEMs, SOAR, EDR and more, SecOps are basically the managers and streamliners of the security terrain. They manage, optimize and get the most out of all those powerful security technologies.
Reporting & Metrics: Data drives their decisions. SecOps tracks all the key security metrics like it’s their job (because it is). Then they package it up into clear reports to share performance insights and recommendations.
SecOps vs DevSecOps: Key Differences
| Feature | SecOps | DevSecOps |
| Focus | Security in ongoing operations and maintenance | Integrating security throughout the software development lifecycle (SDLC) |
| Who’s Involved | Security & IT operations teams | Developers, security specialists, operations teams (collaboration is key) |
| Stage | Existing systems and infrastructure | Software development process (from design to deployment) |
| Main Goal | Improve overall security posture & operational efficiency | Build secure software & reduce security vulnerabilities before deployment |
| Tools | SIEM, SOAR, EDR, vulnerability management tools | Code scanning tools (SAST & DAST), secure coding practices, security libraries, containerization technologies |
| Culture | Collaboration & communication between security and operations | Shared responsibility for security across development, security, and operations teams |
| Reactive vs. Proactive | Primarily reactive, responding to security incidents after they occur | Proactive & preventative, aiming to identify and address security risks early in the development process |
| Example | Identifying & patching vulnerabilities in production systems, responding to security incidents | Implementing secure coding practices, integrating security testing throughout the development pipeline |
The Essential Building Blocks of SecOps

So we know SecOps is all about getting the security crew and ops squad to work together instead of butting heads. But what exactly goes into making that teamwork magic happen? Let’s break down the core building blocks:
1. The Right People On Board
- The Security Team: You need cyber warriors who live and breathe identifying threats, analyzing vulnerabilities, and shutting down incidents on your team. These are the folks who deeply understand the “whys” behind security measures.
- The Operations Team: But you also need the IT ops professionals who know the org’s systems and infrastructure like the back of their hand. They bring the vital “how” knowledge for actually implementing security controls effectively.
- The Leadership Team: Having leadership that champions and fully buys into this collaborative SecOps approach is absolutely critical. They need to provide the resources and top-down support to make it work.
2. Standardized Processes
- Security Policy & Framework: You gotta have a clear, unified security policy and framework that outlines the organization’s security posture and establishes the rules of the road everyone follows.
- Incident Response Plan: There better be a detailed, well-rehearsed incident response plan too. When the cyber alarms go off, this plan coordinates the rapid response across teams to contain the threat.
- Vulnerability Management Process: Having standardized vulnerability management processes is key for continuously identifying, prioritizing, and patching any holes in systems and apps before hackers can exploit them.
3. The Right Security Tech Stack
- SIEM: Powerful SIEM tools that gather and analyze all the security data from across the environment. This provides full visibility into potential threats.
- SOAR: SOAR platforms are a must for automating repetitive security tasks and processes. They reduce human error and free teams for complex work.
- EDR: EDR solutions lock down, monitor, and respond to threats on individual devices like laptops and servers across the network.
4. Seamless Communication Flowing
- Clear Communication Channels: Clear, open communication channels between security teams and ops teams allow for seamless info-sharing and collaboration. No more siloed obstructions.
- Shared Threat Intelligence: Sharing the latest up-to-the-minute threat intelligence allows teams to rapidly detect and contain security incidents before they escalate.
5. An Embedded Security Culture
- Security Awareness & Training: It can’t just be the dedicated teams, though. All employees need to receive regular security awareness and training to empower them to recognize and report potential threats.
- Shared Responsibility: From the intern to the CEO, everyone needs to embrace their role and responsibility for contributing to the organization’s overall security posture. It’s truly a team effort.
SecOps Tools: Your Security Arsenal for a Digital Age

SecOps teams are like warriors – but instead of swords and shields, they wield powerful tools to combat cyber threats. In this ever-evolving digital landscape, having the right SecOps tools in your arsenal is crucial for proactive defense and efficient response. Here’s a breakdown of some key SecOps tools and their functionalities:
1. Security Information and Event Management (SIEM):
Imagine a central nervous system for your security posture. SIEM tools collect data from various security sources like firewalls, intrusion detection systems (IDS), and antivirus software, aggregating it into a single platform. This allows SecOps teams to:
- Correlate events: Analyze seemingly unconnected events to identify potential security incidents.
- Detect threats: Spot suspicious activity and potential breaches in real-time.
- Investigate incidents: Quickly gather and analyze relevant data for faster resolution.
2. Security Orchestration, Automation, and Response (SOAR):
Security is a constant battle, and repetitive tasks can drain valuable time. SOAR platforms come to the rescue by automating routine tasks in the security workflow. Think of it as a smart assistant that can:
- Automate incident response: Streamline workflows for tasks like containment, eradication, and recovery.
- Enforce security policies: Automatically trigger responses based on predefined security rules.
- Reduce human error: Minimize the risk of mistakes associated with manual tasks.
3. Endpoint Detection and Response (EDR):
The frontlines of your network are your individual devices. EDR tools provide advanced protection for endpoints like laptops, desktops, and servers. They can:
- Detect malware: Identify and isolate malicious software attempting to gain access.
- Investigate suspicious activity: Deeply analyze endpoint behavior to uncover potential threats.
- Respond to incidents: Enable rapid isolation and remediation of compromised devices.
4. Vulnerability Management Tools:
Think of vulnerabilities as cracks in your digital armor. Vulnerability management tools help you identify and patch these weaknesses before attackers exploit them. These tools can:
- Scan systems for vulnerabilities: Regularly assess devices and applications for known security flaws.
- Prioritize risks: Rank vulnerabilities based on severity and potential impact.
- Streamline patching: Automate patch deployment processes for faster remediation.
5. Security Analytics Tools:
The digital world generates a massive amount of data. Security analytics tools help you make sense of it all by providing advanced data analysis capabilities. These tools can:
- Identify trends and patterns: Uncover hidden threats and anomalies in security data.
- Predict security risks: Utilize machine learning to anticipate potential attacks.
- Improve decision-making: Provide data-driven insights to support informed security strategies.
Choosing the Right Tools:
Selecting the ideal SecOps tools depends on your organization’s specific needs, budget, and security posture. Here are some key factors to consider:
- The size and complexity of your IT infrastructure
- Your security priorities and threat landscape
- The skillset and expertise of your security team
- Integration capabilities with existing security tools
Challenges of SecOps
Building a strong SecOps program is essential, however, navigating the world of SecOps isn’t without its challenges. Understanding these roadblocks is crucial for building a resilient security posture. Here are some of the key hurdles SecOps teams encounter:
- Cybersecurity Talent Gap
- Alert Overload and False Positive Management
- Securing Legacy Infrastructure and Systems
- Cloud Security Complexities
- Insider Threat Detection and Mitigation
- Lack of Process Automation
- Siloed Communication and Collaboration Barriers
Don’t despair! These challenges can be overcome. In the next section of this article, we’ll explore best practices to address these hurdles and provide a roadmap for getting started with your SecOps journey
Best Practices for Implementing SecOps
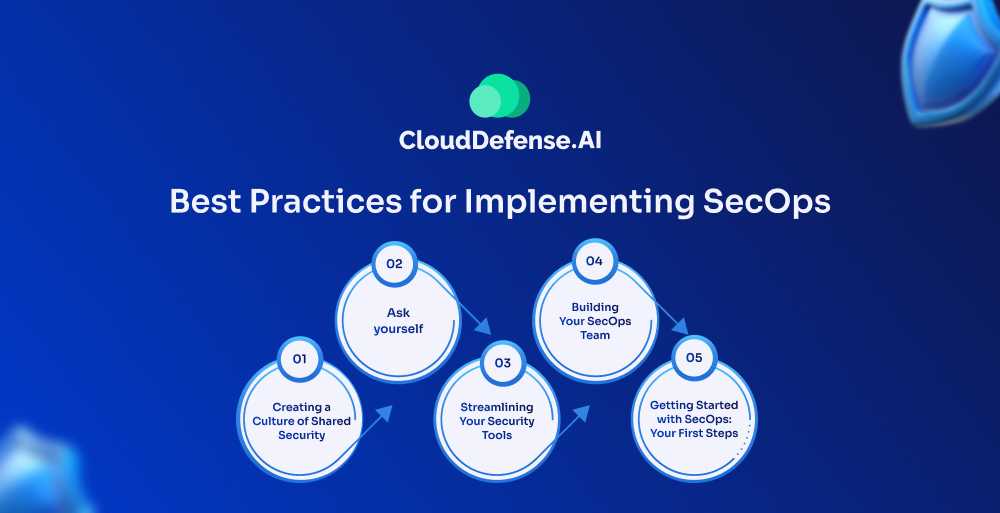
You’ve learned about SecOps, the dynamic duo of security and operations working together to fight cybercrime. Now, it’s time to put theory into action! But before we delve into the “how,” let’s assess your organization’s readiness.
Ask yourself:
- Do your security and operations teams speak the same language (figuratively, of course)? Collaboration is key, so open communication channels are essential.
- Are you drowning in a sea of security alerts? Prioritization is crucial. Can you distinguish real threats from background noise?
- Is your IT infrastructure has outdated systems? Legacy infrastructure can be a security nightmare. Are you prepared to modernize?
- Imagine a security breach. How quickly would your team detect and respond? A slow response is a recipe for disaster. SecOps aims for lightning-fast reflexes.
If you answered “yes” to any of these questions, fret not! The next steps will equip you with the tools and strategies to build a formidable SecOps defense.
Building Your SecOps Team:
- Bridging the Knowledge Gap: Do your security and operations teams understand each other’s challenges? Consider joint training sessions to foster empathy and collaboration.
- Invest in Your People: Skilled cybersecurity professionals are worth their weight in gold. Explore training programs or consider partnering with a Managed Security Service Provider (MSSP) to fill talent gaps.
Streamlining Your Security Tools:
- Prevent Alert Fatique: Implement SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) tools to filter and prioritize alerts. Let technology handle the noise, freeing your team for strategic analysis.
- Embrace Automation: Automate repetitive tasks like patching and user provisioning. This frees up your security analysts to focus on complex threats and incident response.
Creating a Culture of Shared Security:
- Break Down the Silos: Open communication is crucial. Foster a collaborative environment where security and operations teams share information and work together proactively.
- Educate Your Employees: Educate everyone about cybersecurity best practices. Phishing emails and social engineering attacks are a constant threat, so a security-aware workforce is your first line of defense.
Getting Started with SecOps: Your First Steps
Ready to take the plunge? Here’s a roadmap to get your SecOps journey underway:
- Define Your Goals: What are your security priorities? Are you aiming for faster incident response, improved regulatory compliance, or a combination of both? Having clear goals will help you tailor your SecOps strategy.
- Assess Your Landscape: Take stock of your current security posture. What are your strengths and weaknesses? Where are the biggest vulnerabilities?
- Build Your Team: Do you have the necessary skills and expertise in-house, or will you need to outsource some aspects of your SecOps program?
- Prioritize Processes: Identify the most critical security processes and streamline them wherever possible. Consider which tasks can be automated using SOAR tools.
- Select the Right Tools: There’s a whole arsenal of SecOps tools out there – SIEM, SOAR, EDR, the list goes on! Do your research and select tools that address your specific needs and budget.
Final Words
Don’t let your organization become the next headline! Cyber threats are relentless, evolving at a terrifying pace. Legacy systems, talent shortages, and communication breakdowns leave organizations vulnerable, and exposed to ever-increasing risks. SecOps offers a lifeline, but time is of the essence. The longer you wait, the deeper you sink into the maze.
The choice is yours: implement SecOps ASAP and conquer the security maze, or remain lost in a landscape where a single wrong turn can be devastating. Act now, before it’s too late!







