What Is Privileged Access Management (PAM)?
Privileged Access Management, or PAM, is a critical identity security solution designed to protect organizations from cyber threats by tightly controlling and monitoring access to sensitive resources.
PAM operates through a combination of people, processes, and technology, providing organizations with comprehensive oversight of who is accessing privileged accounts and what actions they are performing while logged in.
By limiting the number of users with administrative privileges and adding multiple layers of protection, PAM significantly enhances system security and reduces the risk of data breaches caused by unauthorized users.
At its core, PAM involves a set of cybersecurity strategies and technologies aimed at controlling elevated access and permissions within an organization’s IT environment. This includes managing identities, user accounts, systems, and processes that have access to critical resources.
By implementing strict controls over who can access these resources, PAM helps organizations reduce their attack surface, making it more difficult for external attackers and insider threats to exploit privileged accounts.
What Are Privileged Accounts?
Privileged accounts are special types of user accounts within an organization’s IT infrastructure that have elevated access rights and permissions. Unlike standard user accounts, privileged accounts possess the authority to access highly sensitive information, make critical administrative changes, and perform tasks that are essential to the maintenance and security of systems, applications, and networks.
These accounts are integral to the functioning of an organization’s IT environment, allowing for actions such as installing hardware, updating infrastructure, and resetting passwords. The elevated access that privileged accounts provide makes them a prime target for cybercriminals.
With the credentials of a privileged account, attackers can gain control over an organization’s most sensitive systems, potentially leading to severe data breaches, unauthorized changes to critical infrastructure, and other damaging consequences. Because of the level of access they grant, privileged accounts represent a significant security risk if not properly managed and protected.
How does Privileged Access Management Work?
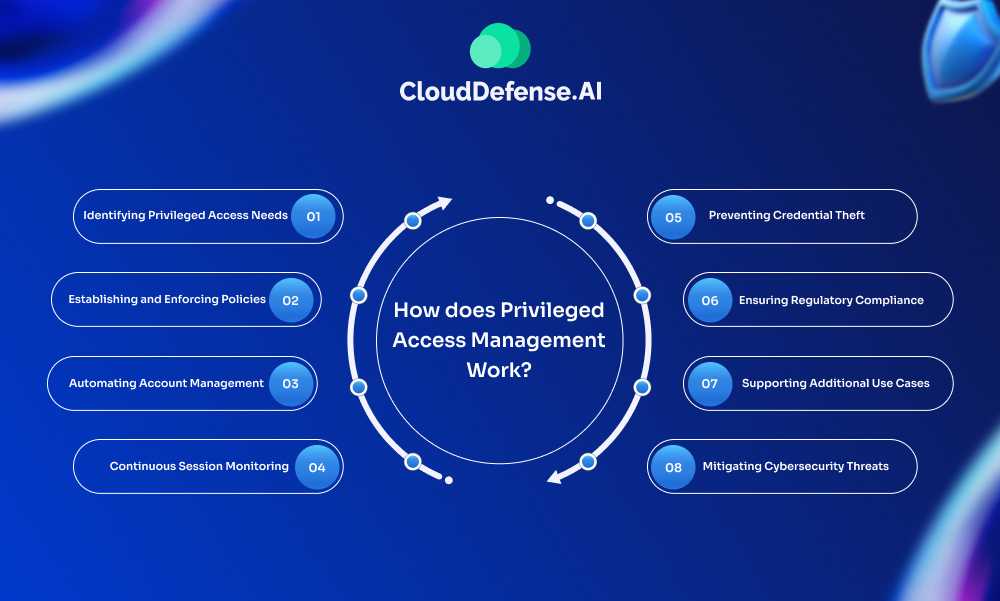
PAM is essential for controlling and monitoring elevated access to protect critical systems and sensitive data.
Identifying Privileged Access Needs
PAM begins by identifying the people, processes, and technologies within an organization that require elevated access. This step is crucial in pinpointing where the highest security risks are located.
Establishing and Enforcing Policies
Once the necessary privileged accounts are identified, PAM solutions establish policies to govern access. These policies may include automated password management, MFA, and just-in-time access, which ensures privileges are granted only when necessary and for limited durations.
Automating Account Management
PAM solutions automate the creation, amendment, and deletion of privileged accounts. This automation reduces the potential for human error and ensures that access is always aligned with up-to-date security policies.
Continuous Session Monitoring
PAM continuously monitors user sessions, tracking all activities performed by privileged accounts. This allows organizations to generate detailed reports that help identify and investigate any anomalies or suspicious behavior.
Preventing Credential Theft
PAM plays a critical role in preventing credential theft, a common threat where attackers steal login credentials to gain unauthorized access. By enforcing just enough access and MFA, PAM makes it significantly harder for attackers to misuse stolen credentials.
Ensuring Regulatory Compliance
Many regulatory standards require the implementation of least-privilege policies. PAM helps organizations meet these requirements by enforcing strict access controls and providing detailed logs of privileged account activities to demonstrate compliance during audits.
Supporting Additional Use Cases
PAM solutions extend beyond basic access control, supporting various use cases like automating the user lifecycle, securing remote and third-party access, and managing privileged access in cloud environments, IoT devices, and DevOps projects.
Mitigating Cybersecurity Threats
Overall, PAM offers effective features to mitigate the risks associated with privileged account misuse, ensuring that organizations stay ahead of potential cybersecurity threats.
Types of Privileged Accounts
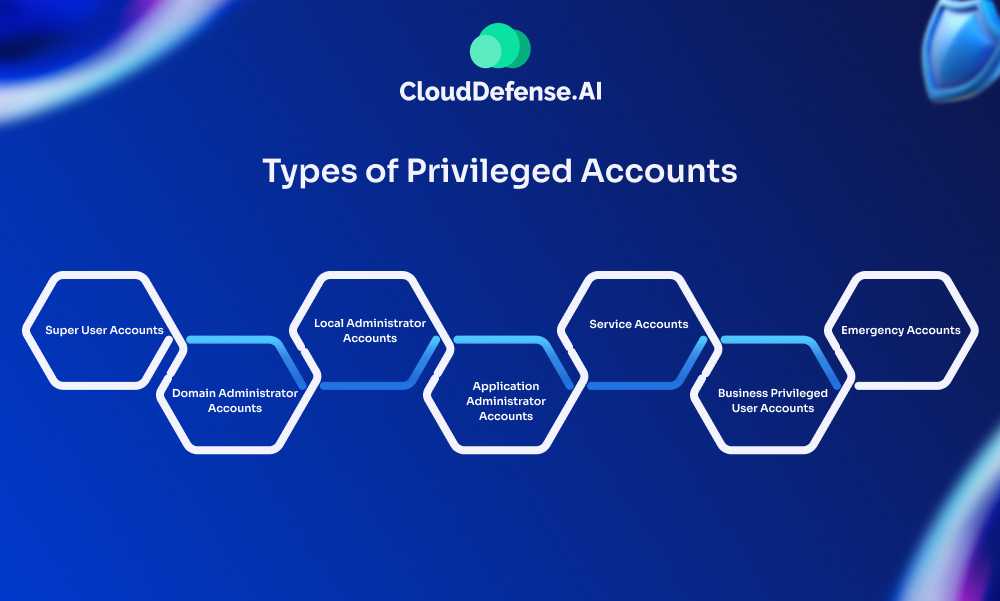
Privileged accounts are specialized user accounts that grant elevated access to systems, applications, and resources within an organization. These accounts have greater permissions than standard user accounts and play a critical role in maintaining and securing IT infrastructure. Here are the key types of privileged accounts:
Super User Accounts
Super user accounts are the most powerful privileged accounts, typically used by system administrators. These accounts have unrestricted access to all files, directories, and resources within a system. Super users can install software, change configurations, manage settings, and delete users and data, making them essential for system management but also high-risk if compromised.
Domain Administrator Accounts
Domain administrator accounts hold the highest level of control within a networked environment. These accounts have access to all workstations and servers across a domain, allowing administrators to control system configurations, manage other admin accounts, and oversee group memberships. Due to their extensive reach, domain administrator accounts are critical to the overall security and operation of an organization’s IT infrastructure.
Local Administrator Accounts
Local administrator accounts provide admin-level control over specific servers or workstations. These accounts are usually created for maintenance tasks on individual machines, such as installing updates or troubleshooting issues. While their access is more limited than domain admin accounts, local administrator accounts still pose a significant security risk if not properly managed.
Application Administrator Accounts
Application administrator accounts have full access to specific applications and the data within them. These accounts are responsible for managing application settings, user access, and data integrity. Because they can directly interact with sensitive data, application administrator accounts are a prime target for attackers.
Service Accounts
Service accounts are used to facilitate secure communication between applications and the operating system. These accounts are typically non-interactive, meaning they do not require human login, but they have the necessary permissions to execute automated tasks and processes. Proper management of service accounts is crucial to prevent unauthorized access to system resources.
Business Privileged User Accounts
Business-privileged user accounts are assigned to users who need elevated access due to their job responsibilities. These accounts may have access to sensitive business information or specific systems required for their role. The level of access granted is typically tailored to the needs of the user, balancing operational efficiency with security.
Emergency Accounts
Emergency accounts, also known as break-glass accounts, are created to provide non-privileged users with temporary admin access in case of an emergency, such as a system failure or disaster recovery situation. These accounts are intended for short-term use and are tightly controlled to minimize security risks.
Benefits of Privileged Access Management
PAM provides significant advantages for organizations by enhancing security and reducing the risk of data breaches. One of the primary benefits is the ability to enforce the principle of least privilege, ensuring that users only have the access necessary to perform their jobs. This minimizes the attack surface and limits the potential damage from compromised accounts.
PAM also enables organizations to monitor and audit privileged account activities, providing visibility into who accessed what, when, and why. This helps in detecting suspicious behavior early and responding quickly to potential threats.
Additionally, PAM solutions streamline the management of privileged accounts, automating processes such as password rotation and access provisioning, which reduces administrative overhead and human error.
How to Implement PAM Security?
By following a structured approach, you can effectively manage and protect privileged accounts, reducing the risk of unauthorized access and ensuring compliance. Here are the key steps to successfully implement PAM security.
- Identify All Privileged Accounts: Begin by identifying all privileged accounts within your organization, including those linked to administrators, applications, and service accounts.
- Establish and Enforce Access Policies: Create and enforce strict access policies based on the principle of least privilege. This may involve setting up automated password management, multifactor authentication, and just-in-time access controls.
- Monitor and Audit Privileged Activities: Continuously monitor and audit activities associated with privileged accounts to detect and respond to anomalies or unauthorized access.
- Use Automation Tools: Utilize automation tools within your PAM solution to efficiently manage tasks such as password rotation, access provisioning, and activity logging.
- Regularly Review and Update Policies: Regularly review and update your PAM policies and practices to stay aligned with evolving security threats and compliance requirements.
- Ensure Seamless Integration: Ensure that your PAM solution integrates seamlessly with your existing IT infrastructure and security tools to provide comprehensive protection.
Final Words
Privileged Access Management is a cornerstone of effective cybersecurity strategies, offering powerful tools to control, monitor, and secure privileged accounts. By implementing PAM, organizations can significantly reduce their risk of data breaches, ensure compliance with regulatory standards, and maintain the integrity of their IT environments.
The key to successful PAM implementation lies in thorough planning, continuous monitoring, and regular updates to policies and procedures. In an era where cyber threats are increasingly sophisticated, PAM provides the essential oversight and control needed to defend critical systems and sensitive data.







