Welcome back to our Zero Trust security series! In our previous installments, we’ve explored the fundamental concepts of Zero Trust architecture and its implementation within AWS environments. Please check them out as well if you haven’t yet.
We’re thrilled to dive deeper into the best practices for AWS Zero Trust implementation you need to know to strengthen your cloud infrastructure’s security posture. Whether you’re already familiar with Zero Trust or just beginning to explore its potential, this edition promises valuable insights to enhance your AWS security strategy.
Join us as we delve into the 10 best practices for implementing AWS Zero Trust in your AWS environment and discover how AWSZeroTrustPolicy can revolutionize your security approach. Let’s embark on this journey to protect your cloud assets in a modern way.
Understanding the Importance of Cloud Security
Cloud security is vital as organizations increasingly adopt cloud computing. According to the latest forecast from Gartner, Inc., global end-user spending on public cloud services is projected to surge by 20.4% in 2024, reaching a total of $678.8 billion, up from $563.6 billion in 2023. This trend makes it clear that cloud usage is rising. However, IT professionals express worries about security, governance, and compliance issues linked to cloud storage.
They fear accidental leaks or cyber threats compromising sensitive business information. Protecting data and business content is crucial for maintaining customer trust and protecting competitive advantage. Yet, the landscape is filled with risks; Ermetic and IDC report that 80% of CISOs have faced cloud data breaches in the past 18 months, with nearly half experiencing 10 or more breaches.
Cloud security is not just about protecting data—it’s about ensuring the safety of the entire organization, its staff, and its customers. Understanding these risks and implementing strong security measures are essential for any company moving to the cloud.
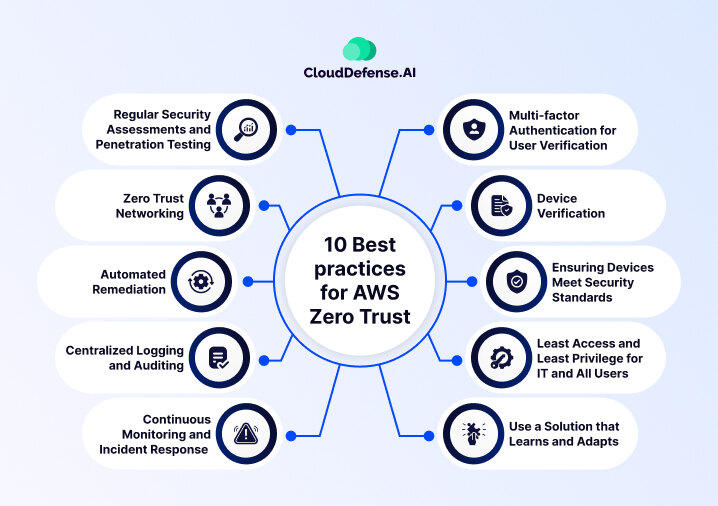
10 Best Practices for AWS Zero Trust
Organizations must rethink their security approach to protect important assets in the company. This is where AWSZeroTrustPolicy can help build a culture of strong access controls, allowing users to access only what they need to work with. AWSZeroTrustPolicy is an open-source AWS Policy Generator API developed by CloudDefense.AI that harnesses AWS CloudTrail logs to craft IAM policies with the principle of least privilege.
AWSZeroTrustPolicy is tailored to actual user activities within a specified timeframe, effectively shrinking the attack surface, minimizing risks, and enhancing overall security. The policies help companies to work with a Zero Trust security model, building a culture of security awareness on AWS cloud environments and protecting the sensitive data of their clients.
Let’s take a look into the best practices for implementing AWS Zero Trust Security while incorporating AWSZeroTrustPolicy wherever applicable
1. Multi-factor Authentication for User Verification
Enhance user authentication by implementing MFA across all user types, including end-users, privileged users, and partners.
How can AWSZeroTrustPolicy Help?
AWSZeroTrustPolicy simplifies MFA implementation by generating IAM policies that are tailored to MFA requirements.
2. Device Verification
Extend identity-centric controls to endpoints by verifying and enrolling devices accessing AWS resources.
How can AWSZeroTrustPolicy Help?
Utilize AWSZeroTrustPolicy to automate device verification processes, ensuring only trusted devices access corporate resources.
3. Ensuring Devices Meet Security Standards
Enforce security standards on devices accessing AWS resources, including disk encryption and up-to-date patches.
How can AWSZeroTrustPolicyHelp?
AWSZeroTrustPolicy enables automated enforcement of device compliance policies, ensuring adherence to security standards.
4. Least Access and Least Privilege for IT and All Users
Limit access privileges based on the principle of least privilege for all users, including privileged users.
How can AWSZeroTrustPolicyHelp?
Use AWSZeroTrustPolicy to generate IAM policies that enforce least privilege access controls, minimizing the risk of unauthorized access.
5. Use a Solution that Learns and Adapts
Implement a solution that utilizes machine learning to dynamically adapt security controls based on user behavior and contextual information.
How can AWSZeroTrustPolicyHelp?
AWSZeroTrustPolicy leverages AWS CloudTrail logs to generate IAM policies tailored to actual user activities, enhancing security through adaptive access controls.
6. Continuous Monitoring and Incident Response
Implement continuous monitoring of AWS resources to detect and respond to security incidents in real-time. Utilize AWS security services such as AWS Security Hub and AWS CloudWatch to monitor for security threats and automate incident response with AWS Lambda.
How can AWSZeroTrustPolicyHelp?
AWSZeroTrustPolicy can help create policies that integrate with these services to enforce dynamic access controls based on real-time security alerts.
7. Centralized Logging and Auditing:
Maintain centralized logs of all user activities and access attempts within the AWS environment. Utilize AWS CloudTrail to capture API activity and AWS Config for resource configuration history.
How can AWSZeroTrustPolicyHelp?
AWSZeroTrustPolicy can use these logs to generate IAM policies that align with compliance requirements and audit trails.
8. Automated Remediation
Implement automated remediation workflows to address security vulnerabilities and policy violations proactively. Utilize AWS Systems Manager Automation to automate remediation actions such as patching, configuration changes, and user privilege adjustments.
How can AWSZeroTrustPolicyHelp?
AWSZeroTrustPolicy can integrate with automation workflows to enforce security controls automatically based on predefined policies.
9. Zero Trust Networking
Implement AWS Zero Trust principles at the network level by segmenting and isolating AWS workloads based on user roles, application dependencies, and data sensitivity. Utilize AWS Virtual Private Cloud to create network security boundaries and enforce strict access controls using AWS Security Groups and Network Access Control Lists.
How can AWSZeroTrustPolicyHelp?
AWSZeroTrustPolicy can generate IAM policies that complement network security controls to enforce least privilege access at both the network and application layers.
10. Regular Security Assessments and Penetration Testing
Conduct regular security assessments and penetration testing of AWS infrastructure to identify and remediate security vulnerabilities. Utilize AWS Inspector and third-party penetration testing tools to assess the security posture of AWS resources and applications.
How can AWSZeroTrustPolicyHelp?
AWSZeroTrustPolicy can adapt access controls based on the results of security assessments to ensure continuous compliance with security standards and regulations.
Conclusion
Having best practices for implementing AWS Zero Trust security can be a game changer for organizations. Best practices help ensure that the security measures being implemented are not only efficient but also effective in protecting valuable assets and sensitive data. By following established best practices, organizations can minimize security risks, maintain compliance with regulatory requirements, and build a stronger security posture in their AWS environment.
As you work on strengthening security in your AWS environment, consider using AWSZeroTrustPolicy to bring your efforts to fruition. It simplifies the setup by creating IAM policies based on real user actions, reducing risks and protecting sensitive data. With AWSZeroTrustPolicy, implementing Zero Trust security becomes easier, preparing your AWS infrastructure to face potential threats.







