What is SBOM?
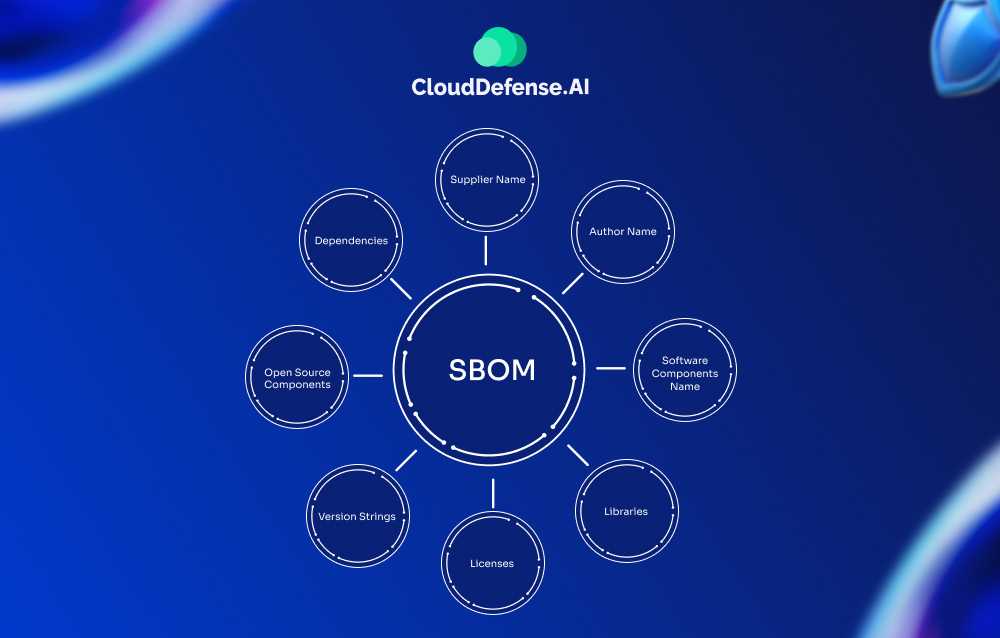
SBOM is basically a detailed inventory of all the components and dependencies that make up a piece of software. Think of it like the ingredients list on a food product.
An SBOM lists out:
- All the open-source components included
- Any third-party components that were part of the build
- And, for each component, it provides the supplier name, version number, hash values to validate it, and details on known vulnerabilities or security advisories.
It’s kind of like getting an X-ray of the software’s DNA—you can see every single ingredient that went into it, where each one came from, and if any of them have had security issues flagged previously. This transparency is crucial in today’s world of complex software supply chains.
The components outlined typically include:
- Developer tools and frameworks
- Code libraries
- Packages
- Executable binaries
Having this comprehensive “family tree” lets you trace any piece back to its source if a vulnerability is later discovered. It makes it much easier to assess risk exposure and take action quickly when needed.
SBOMs essentially allow you to manage and maintain visibility into what’s under the hood throughout the entire software lifecycle. That visibility is the key to bolstering supply chain security and integrity.
Why Do Organizations Need a Software Bill of Materials?
Considering our interconnected digital world, software supply chains have become vastly complex. Most applications today are built using a wide range of third-party and open source components from various sources. While this allows for faster development, it also introduces potential risks.
A single vulnerable component can open the door to cyberattacks that compromise the entire application. And with so many moving parts, it’s extremely difficult to track and manage all those risks manually.
An SBOM acts as a roadmap to understanding and managing that risk. It illuminates all the third-party and open-source elements incorporated into your software. With an SBOM, you can:
✔ Gain visibility into your software supply chain to identify potential vulnerabilities
✔ Quickly pinpoint the source of a vulnerability and remediate it
✔ Facilitate more effective license analysis and compliance
✔ Make well-informed risk decisions about the components you’re using
Without an SBOM, it’s like navigating software security blindfolded. You have no idea what vulnerabilities may be hiding in the depths of your code dependencies. An SBOM rips off that blindfold.
As supply chain attacks increase, SBOMs are becoming critical for protecting organizations against crippling incidents like the SolarWinds breach. They provide the transparency needed to effectively manage cyber supply chain risks in our interconnected world.
Software Bill of Materials (SBOM) Lifecycle
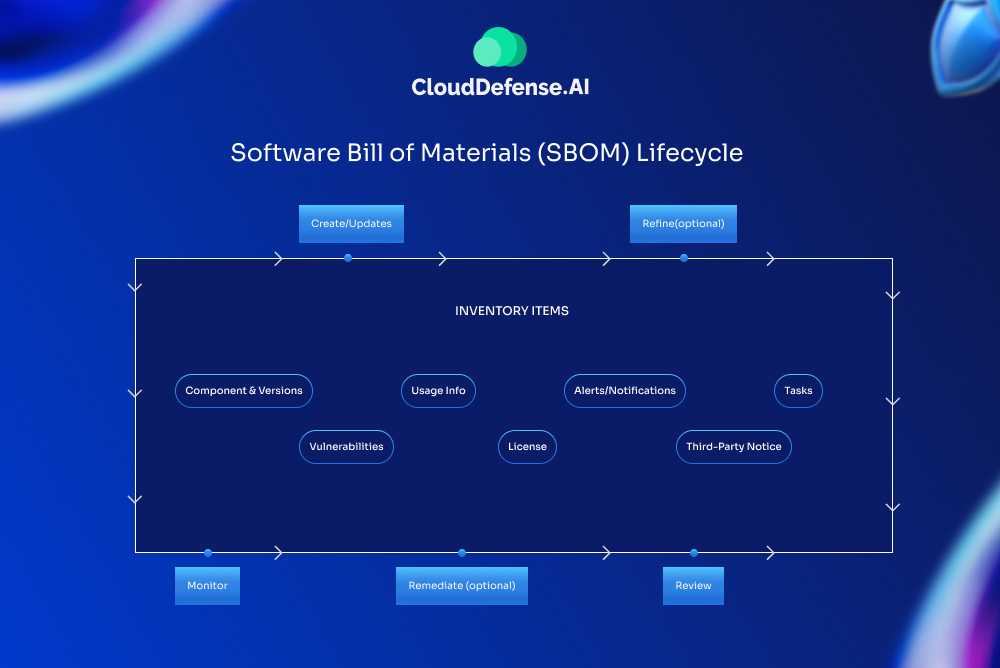
The SBOM Lifecycle is a structured process designed to ensure transparency, security, and compliance throughout the software supply chain. This lifecycle revolves around creating, managing, and improving the SBOM as organizations work to safeguard their applications and dependencies.
1. Start with Creation or Updates:
The process begins with creating or updating the SBOM. This step involves cataloging all the software components, their versions, and related information to establish a reliable inventory. Regular updates ensure the SBOM stays accurate as software evolves.
2. Core Inventory Items:
At the heart of this lifecycle are the inventory items, which provide crucial insights into your software ecosystem:
- Components & Versions: Track all software components and their specific versions to maintain clarity.
- Usage Info: Understand where and how each component is used.
- Alerts/Notifications: Stay informed about emerging risks, updates, or compliance requirements.
- Tasks: Assign and track action items for efficient SBOM management.
- Vulnerabilities: Identify potential security flaws in your software stack.
- Licenses: Ensure license compliance for open-source and proprietary components.
- Third-party Notices: Manage terms and conditions tied to third-party dependencies.
3. Refinement:
After establishing the inventory, refinement ensures the SBOM is accurate and comprehensive. This step is optional but valuable for improving clarity and utility.
4. Review:
Regular reviews of the SBOM help ensure compliance with industry standards, identify gaps, and validate that everything is up to date. This is a critical checkpoint for maintaining trust and security.
5. Monitor Continuously:
Monitoring is an ongoing activity to keep an eye on new vulnerabilities, updates, or changes within the software components. This step ensures early detection of risks and swift action when needed.
6. Remediation:
When vulnerabilities or compliance issues are identified, remediation steps—such as patching or updating components—are taken to minimize risks and maintain security.
SBOM Formats and Standards
While the concept of an SBOM is straightforward, there are multiple data format standards that have emerged:
SPDX: One of the earliest and most widely adopted standards is the Software Package Data Exchange (SPDX). It represents SBOMs in tag:value format or XML/RDF format. SPDX has been embraced by major tech companies and is an approved ISO/IEC standard.
SWID: Another format is Software Identification (SWID) tags based on XML. It was developed by the ISO and is commonly used for installed software tracking and inventorying.
CycloneDX: This XML/JSON format was created specifically for SBOMs by the OWASP CycloneDX project. It is designed to be easily created and consumed by software tools.
SPDX and CycloneDX are seeing the most traction currently, with a push for greater standardization around minimum data components that should be included in any SBOM format.
The key data points an SBOM aims to capture include:
- Component names and unique identifiers
- Version info and patch details
- Author/supplier mapping
- Dependency relationships
- Known security advisories or vulnerabilities
Having standardized, machine-readable SBOM data allows it to be easily consumed, analyzed, and shared across different systems and tools in the software supply chain. As SBOM adoption grows, standards alignment will be crucial for facilitating SBOM automation, improving interoperability, and streamlining vulnerability management.
Cloud-native and the SBOM Challenge: A Symbiotic Relationship
As organizations embrace cloud-native development and containerized workloads, it introduces new complexities for SBOMs. These modern applications have more dynamic and ephemeral environments compared to traditional monolithic software.
With cloud-native apps, the components can include:
- Container images
- Orchestration tools like Kubernetes
- Service meshes
- Serverless functions
- Microservices
- API gateways
- And, more infra-as-code elements
The more distributed nature of these apps means the software supply chain is continuously reassembling itself through automated builds, deployments, and scalable infrastructure provisioning.
Traditional static SBOMs quickly become outdated. Cloud-native SBOMs need to be generated as part of the CI/CD pipeline and continuously updated in real-time to reflect the current lived state of all components.
Tools are emerging to help automatically generate, maintain, and share SBOMs natively as part of cloud deployment workflows using formats like SPDX and CycloneDX.
Effectively managing SBOMs for cloud-native applicatons requires:
- Automated SBOM generation
- Continuous real-time updates
- Integration with DevSecOps toolchains
- Mapping to cloud service provider components
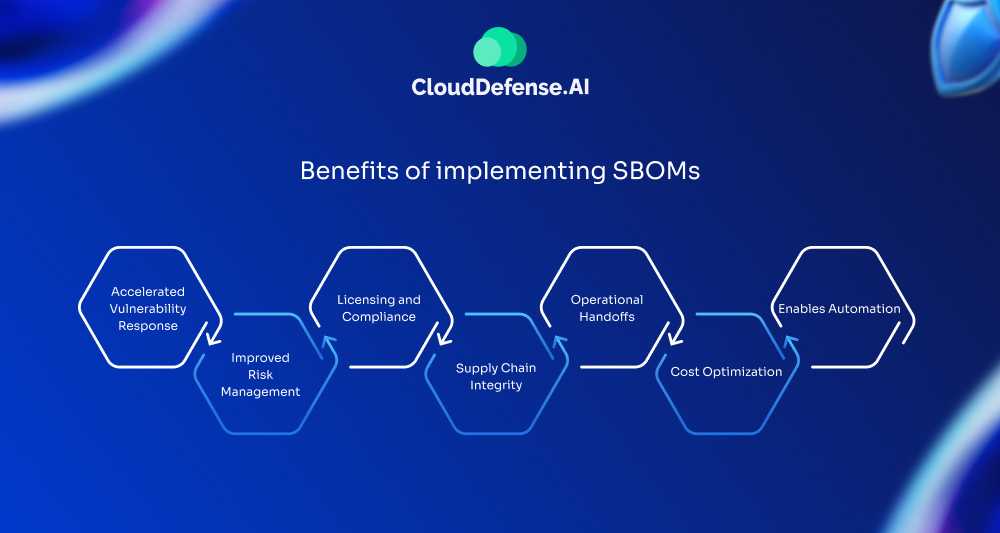
Benefits of implementing SBOMs
As cloud complexity increases, having accurate just-in-time SBOMs will be critical for maintaining supply chain integrity. While adopting SBOMs requires an upfront investment, the potential benefits make it a security best practice that organizations can’t afford to ignore:
Accelerated Vulnerability Response
With a comprehensive SBOM, you can quickly identify whether your software is exposed to a newly disclosed vulnerability and precisely which components need updating or patching.
Improved Risk Management
SBOMs provide visibility into your risk exposure from open source and third-party components. This data enables better-informed risk decisions.
Licensing and Compliance
In addition to security, SBOMs can be used to analyze and comply with software licenses across your code supply chain.
Supply Chain Integrity
End-to-end SBOMs help verify the integrity of software releases by enabling verification of components against authoritative sources.
Operational Handoffs
As software traverses the SDLC, SBOMs ensure full transparency for stakeholders like suppliers, operations, and even customers.
Cost Optimization
By inventorying all your software materials, you can optimize component use, reduce redundancies, and cut costs.
Enables Automation
Machine-readable SBOMs allow security tasks like vulnerability monitoring to be automated within DevSecOps toolchains.
Challenges in Adopting SBOMs

While the benefits of SBOMs are clear, there are some significant hurdles that have slowed enterprise-wide adoption:
Legacy Software Concerns: Creating comprehensive SBOMs for legacy monolithic applications and codebases can be extremely difficult and time-consuming without automated tooling.
Limited SBOM Maturity: SBOM standards, formats, and tooling are still relatively immature compared to other security practices. This makes SBOM implementation more challenging.
Visibility Gaps: For commercial off-the-shelf software and cloud services, getting SBOMs from vendors with sufficient depth can be problematic.
Cloud Complexity: As mentioned, cloud-native apps with ephemeral, dynamically-assembled components require sophisticated SBOM automation capabilities.
Supply Chain Disconnect: Ensuring SBOM handoffs across the software supply chain requires coordination between multiple teams and toolchains.
Vulnerability Overload: SBOMs make it easier to discover vulnerabilities, but teams may get overwhelmed by the volume without prioritization.
Staffing and Skills: Implementing and operationalizing SBOMs requires specialized skills that are currently in high demand.
Overcoming SBOM Adoption Hurdles
While adopting SBOMs poses challenges like compatibility with legacy apps, lack of standards, skills gaps, and managing vulnerability overload, there are ways to ease the growing pains:
- Leverage automation tools for generating, maintaining, and analyzing SBOMs
- Push for standards alignment around formats like SPDX and CycloneDX
- Integrate SBOM generation into CI/CD pipelines and DevSecOps toolchains
- Implement controls to manage SBOM depth and alert volume
- Enable secure SBOM sharing across teams and the supply chain
- Invest in upskilling staff on SBOM practices
- Establish SBOM governance policies and responsibilities
As SBOM tooling matures and expertise increases, SBOMs will become standard operating practice for securing the software supply chain. Addressing the obstacles now pays dividends later.
SBOMs in the Cloud: A Perfect Fit for Modern Infrastructure
As more workloads shift to the cloud, having accurate SBOMs that map to cloud-native components is becoming critical. Here’s how SBOMs integrate with cloud infrastructure:
CI/CD Pipelines: SBOM generation should be an automated step in the CI/CD pipeline. Each build produces a new SBOM reflecting all components.
Container/Artifact Repositories: SBOMs can be stored and scanned alongside container images in private registries. Cloud providers offer SBOM support.
Infrastructure as Code: Infrastructure provisioning tools like Terraform can automatically include SBOMs for cloud resources being deployed.
Cloud Services: For cloud platforms/services that don’t provide SBOM data, software composition analysis tools can generate SBOMs.
Live Inventory: Real-time cloud inventory and monitoring tools ingest SBOMs to provide a continuously updated view of deployed resources.
Security Scanning: Cloud security solutions use SBOMs to scan workloads for vulnerabilities and misconfigurations during builds and runtime.
Compliance Reporting: SBOMs enable automated reports proving compliance with cybersecurity and license requirements.
The key is treating SBOMs as first-class cloud artifacts that get generated, stored, updated and shared through integrated toolchains aligned to CI/CD processes. This closed-loop automated approach is vital for maintaining SBOM accuracy at the cloud scale.
Final Words
The software supply chain is fundamentally vulnerable, and the risks are growing exponentially. Hostile nation-states and cybercriminals are actively exploiting the lack of transparency and code integrity to launch devastating supply chain attacks. Major incidents like SolarWinds and Kaseya were mere wake-up calls – the cyber pandemic has already begun.
Without adopting robust SBOM practices, organizations are left flying blind, unaware of the ticking bombs laced throughout their code. SBOMs are no longer a nice-to-have, but an urgently required immunization protecting the digital arteries that modern society depends on. Implement SBOMs now, or be rendered defenseless against the next crippling cyber onslaught.







