What is a SOC?
A Security Operations Center (SOC) is the nerve center of an organization’s cybersecurity. It’s where security analysts, incident responders, and threat hunters work round the clock to detect, analyze, and respond to cyber threats in real-time.
Picture the role of a SOC as mission control for cybersecurity—it continuously monitors an organization’s digital environment, ensuring that no threat goes unnoticed.
Core Functions of a SOC:
- Continuous Monitoring: Tracks network traffic, logs, and user activity 24/7.
- Threat Detection & Analysis: Uses SIEM (Security Information and Event Management) and threat intelligence feeds to spot anomalies.
- Incident Response: Investigates and mitigates security incidents before they escalate.
- Forensics & Reporting: Collects evidence and generates reports for compliance and post-incident analysis.
- Threat Hunting: Proactively searches for undetected threats lurking in the system.
Traditional SOCs rely heavily on manual processes—analysts sifting through alerts, triaging incidents, and manually investigating threats. But here’s the problem:
- Alert Fatigue: Security teams face an overwhelming number of alerts daily.
- Slow Response Times: Manual investigations delay threat containment.
- Human Error: Analysts can miss critical threats due to volume overload.
This is where SOC Automation changes the game. Let’s dive into that next.
What is SOC Automation?
Traditional SOCs struggle with alert fatigue, slow response times, and manual inefficiencies. SOC automation eliminates these bottlenecks by leveraging AI, machine learning, and orchestration tools to automate threat detection, investigation, and response.
In other words, SOC Automation is the process of using AI, machine learning, and orchestration tools to automate threat detection, analysis, and response within a Security Operations Center (SOC). Instead of relying solely on human analysts to manually investigate alerts, SOC automation enables security teams to detect, prioritize, and respond to threats faster and more accurately.
At its core, SOC automation:
- Eliminates manual inefficiencies in security operations.
- Reduces response times from hours to minutes.
- Minimizes human error by automating repetitive tasks.
Why is SOC Automation Necessary?
Traditional SOCs are overwhelmed. Analysts face an unmanageable volume of security alerts daily, most of which are false positives. Manual investigation is too slow, leading to delayed threat response and increased risk of breaches.
Here’s why SOC automation is no longer optional—it’s a necessity:
1. The Overload of Security Alerts
- A modern enterprise SOC receives thousands of alerts every day.
- 80%+ of these alerts are false positives, wasting valuable analyst time.
- Manually triaging these alerts is impossible at scale.
Without automation: Analysts spend hours investigating alerts that turn out to be harmless.
With automation: AI filters out false positives and escalates only real threats.
2. Faster Attack Timelines = Slower Manual Response
- Cyberattacks unfold in minutes—ransomware can encrypt files within seconds.
- A manual investigation takes hours or even days, giving attackers a head start.
Without automation: By the time analysts respond, the damage is already done.
With automation: Threats are detected and contained in real time before they escalate.
3. Cybersecurity Skill Shortage
- There’s a global shortage of skilled cybersecurity professionals.
- Manual SOC operations require large teams—but hiring is a challenge.
Without automation: Security teams remain understaffed and overwhelmed.
With automation: AI and machine learning bridge the skill gap by handling repetitive tasks.
4. Reducing Human Error
- Security analysts deal with alert fatigue, leading to missed threats.
- Manual processes increase the risk of misconfiguration, leaving security gaps.
Without automation: Mistakes happen, and critical threats may slip through.
With automation: AI ensures consistent and accurate threat detection and response.
How Does SOC Automation Work?
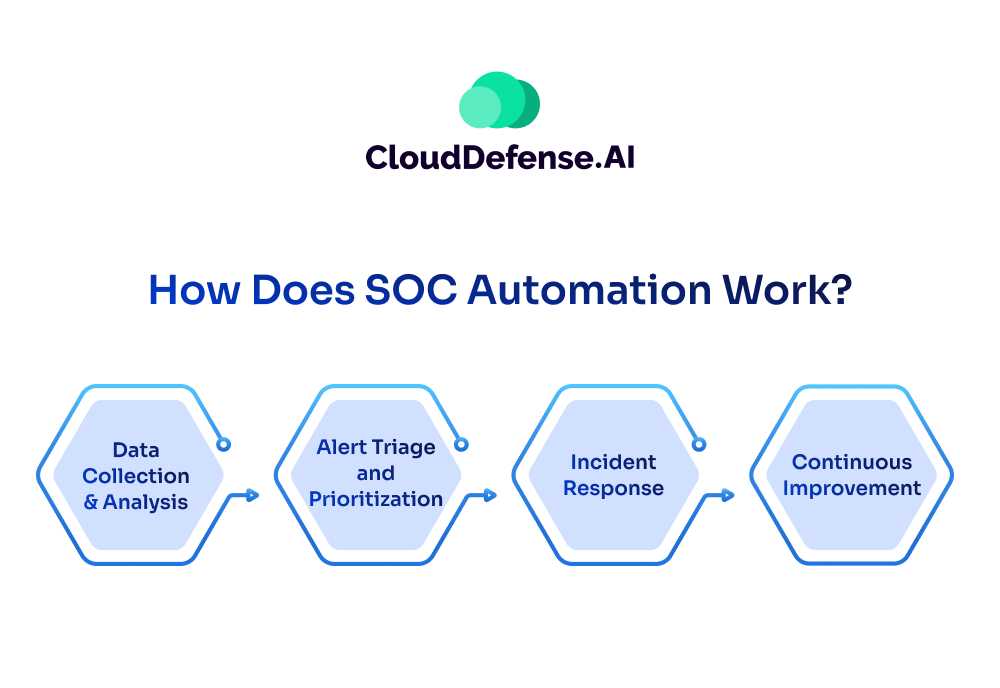
SOC automation streamlines and accelerates security operations by integrating AI, machine learning, and orchestration tools into the existing SOC framework. It replaces manual, repetitive tasks with automated workflows, ensuring faster threat detection, analysis, and response.
Here’s how it works:
1. Automated Threat Detection
- AI-powered security tools continuously monitor logs, network traffic, and endpoints to identify suspicious activity in real time.
- Machine learning models analyze historical attack patterns to detect anomalies and zero-day threats before they escalate.
Example: AI detects an unusual login attempt from an unauthorized IP address and flags it for investigation instantly—before an analyst even sees it.
2. Intelligent Alert Prioritization
- SOCs receive thousands of alerts daily, many of which are false positives.
- SOC automation filters out noise and categorizes alerts based on risk level, ensuring analysts focus only on high-priority threats.
Example: Instead of overwhelming analysts with 10,000 low-risk alerts, automation escalates only the critical ones that require human intervention.
3. Automated Incident Response
Security Orchestration, Automation, and Response (SOAR) tools execute predefined playbooks to take immediate action on threats.
Responses can include:
- Isolating a compromised endpoint to prevent lateral movement.
- Blocking malicious IPs or domains automatically.
- Triggering an automated forensic investigation to gather evidence.
Example: If a phishing email is detected, automation quarantines it, scans affected devices, and resets compromised credentials without waiting for human input.
4. Self-Healing Systems & Automated Remediation
Advanced SOCs leverage self-healing mechanisms that can patch vulnerabilities, restore compromised files, and roll back system changes without human intervention.
Example: If malware infects a system, automation removes the malicious file, restores the system from a clean backup, and updates security policies to prevent a future attack.
5. AI-Driven Forensics & Reporting
- SOC automation gathers, analyzes, and compiles incident data into actionable reports within seconds—ensuring faster compliance and audits.
- Threat intelligence platforms enrich reports with contextual data, helping analysts make data-driven security decisions.
Example: After a cyberattack, automation generates a detailed forensic report outlining the attack vector, affected assets, and recommended countermeasures—saving analysts hours of manual work.
SOC automation doesn’t just accelerate threat response—it transforms security operations by:
- Eliminating manual bottlenecks
- Reducing human error
- Enhancing detection accuracy
- Ensuring real-time, automated defense
Without automation, SOCs are slow, reactive, and overwhelmed. With automation, they become proactive, efficient, and resilient.
Key Technologies Powering SOC Automation
SOC automation isn’t just about reducing manual work—it’s about making security operations faster, smarter, and more efficient. This is made possible by a combination of advanced technologies that work together to detect, analyze, and respond to threats in real time.
1. Security Information and Event Management (SIEM)
- SIEM systems collect, aggregate, and analyze security logs from multiple sources like firewalls, endpoint security, and cloud environments.
- They use correlation rules and AI-driven analytics to identify suspicious activity.
- SIEMs integrate with automation tools to trigger real-time responses.
Example: If a SIEM detects an unusual login attempt from multiple locations, it can automatically block access and alert security teams.
2. Security Orchestration, Automation, and Response (SOAR)
- SOAR platforms connect various security tools to automate workflows.
- They execute predefined playbooks for incident response, reducing the need for manual intervention.
- SOAR solutions enable automated threat containment, investigation, and reporting.
Example: If malware is detected on a device, SOAR can isolate the system, remove the malicious file, and generate an incident report—all without human involvement.
3. Artificial Intelligence & Machine Learning
- AI and ML power behavioral analytics to detect anomalies that traditional rule-based systems might miss.
- These technologies continuously learn from new attack patterns, improving threat detection accuracy.
- AI also automates triage, reducing false positives and prioritizing real threats.
Example: A machine learning model detects an insider threat by recognizing unusual file access behavior, even if no known attack signature exists.
4. Endpoint Detection and Response (EDR) & Extended Detection and Response (XDR)
- EDR solutions monitor endpoint activity to detect and mitigate threats in real time.
- XDR extends this capability across multiple security layers, including network, cloud, and email security.
- These tools provide automated threat hunting and remediation.
Example: If an endpoint starts executing suspicious PowerShell commands, EDR can terminate the process and isolate the device instantly.
5. Threat Intelligence Platforms (TIPs)
- TIPs aggregate real-time threat intelligence from multiple sources, including open-source feeds, government agencies, and private vendors.
- They enhance SOC automation by enriching alerts with contextual information, reducing investigation time.
Example: If an IP address is flagged as part of a botnet, a TIP can provide historical data and automate its blocking across firewalls.
6. Robotic Process Automation (RPA) for Security
- RPA automates repetitive security tasks such as log analysis, patch management, and access reviews.
- It enhances efficiency by reducing human workload on routine SOC operations.
Example: RPA bots can automatically collect security logs, generate compliance reports, and escalate anomalies for further review.
7. Cloud Security Automation Tools
- Cloud-native security tools integrate with SOC automation to secure cloud workloads, containers, and SaaS applications.
- They enable automated misconfiguration detection, compliance enforcement, and threat response.
Example: If a cloud storage bucket is left publicly accessible, automation can immediately revoke access and alert the security team.
What Is the Role of AI in SOC Automation?
Artificial Intelligence (AI) is the backbone of modern SOC automation, transforming security operations from reactive to proactive. By leveraging AI-driven analytics, machine learning models, and automation, SOCs can detect, analyze, and respond to threats faster and with greater accuracy than traditional methods.
1. AI-Powered Threat Detection
Traditional security systems rely on static rules and signature-based detection, which struggle against new or evolving threats. AI changes this by:
- Using behavioral analytics to detect anomalies that don’t match known attack signatures.
- Continuously learning from historical attack data to identify emerging threats.
- Reducing false positives by distinguishing between normal and suspicious activity.
AI detects an insider threat by recognizing that a user is suddenly accessing sensitive files at odd hours—something a rule-based system might miss.
2. AI-Driven Alert Prioritization
SOC teams are overwhelmed with thousands of security alerts daily—many of which are false positives. AI optimizes this by:
- Sorting and filtering alerts based on severity and likelihood of an actual attack.
- Automatically correlating multiple alerts to identify real threats faster.
- Reducing analyst fatigue by ensuring only high-priority alerts require manual investigation.
Instead of bombarding analysts with 10,000 firewall alerts, AI clusters them, identifies 20 actual threats, and prioritizes the most critical ones.
3. AI-Powered Automated Incident Response
When a security breach is detected, every second counts. AI helps by:
- Automating playbook execution in SOAR platforms to contain and remediate threats instantly.
- Triggering predefined responses such as isolating an infected endpoint or blocking malicious IPs.
- Learning from past incidents to improve response efficiency over time.
AI detects ransomware activity and immediately quarantines affected devices, preventing further encryption—without waiting for a human response.
4. AI-Enhanced Threat Hunting
AI enables proactive threat hunting by:
- Identifying patterns in massive datasets that human analysts might overlook.
- Predicting potential attack vectors before they are exploited.
- Correlating data across multiple sources (network logs, endpoint activity, and user behavior) to reveal hidden threats.
AI notices that a seemingly harmless login attempt is linked to an IP address used in previous cyberattacks, triggering an investigation before damage occurs.
5. AI for Predictive Security Analytics
Instead of just reacting to incidents, AI helps SOCs become predictive by:
- Forecasting which systems are most likely to be attacked based on historical patterns.
- Identifying weak security configurations that adversaries could exploit.
- Suggesting proactive security measures to reduce risk.
AI predicts that an unpatched server will be targeted based on rising exploit attempts against similar servers worldwide, prompting an automated patching action.
6. AI in Automated Forensics & Reporting
After a security incident, AI accelerates investigation and compliance reporting by:
- Compiling and analyzing logs from multiple sources instantly.
- Generating detailed post-incident reports with attack timelines, affected assets, and response actions.
- Reducing manual effort in compliance audits by automating data collection.
AI generates a full forensic report within seconds, outlining how a phishing attack infiltrated the network and recommending future preventive measures.
By integrating AI-driven detection, response, threat hunting, and predictive analytics, SOCs can:
- React faster to security incidents
- Reduce analyst workload by eliminating noise
- Enhance detection accuracy beyond human capability
- Prevent attacks before they happen
Without AI, SOCs are slow and reactive. With AI, they become intelligent, proactive, and nearly autonomous.
Considerations for Automating SOC Workflows
Automating SOC workflows can significantly enhance threat detection, response speed, and overall security efficiency. However, implementing automation without a strategic approach can introduce new challenges. Before deploying SOC automation, organizations must consider key factors to ensure seamless integration and optimal security outcomes.
1. Data Quality and Integration
- Automation is only as good as the data it processes. Inconsistent, incomplete, or noisy data can lead to inaccurate threat detection and response.
- Security tools must be integrated to provide a unified data stream, ensuring that automation can analyze and act on accurate information.
- Log correlation across multiple sources (SIEM, EDR, firewalls, cloud security tools) is critical for effective automation.
If an automated system pulls in unfiltered logs with excessive false positives, it may trigger unnecessary alerts and actions, overwhelming SOC analysts.
2. Defining Clear Use Cases for Automation
- Not all SOC tasks should be automated. Organizations must define which processes benefit from automation without sacrificing security oversight.
- Best candidates for automation include:
- Repetitive tasks: Log analysis, alert triage, and correlation.
- Incident response: Automatic containment of threats, such as isolating compromised endpoints.
- Threat intelligence enrichment: Aggregating threat feeds and correlating them with internal logs.
Automating phishing email analysis can drastically reduce manual effort, but complete automation without human validation may lead to false positives affecting legitimate emails.
3. Balancing Automation with Human Oversight
- Full automation without human intervention can create risks, especially for complex security incidents requiring contextual analysis.
- A human-in-the-loop model ensures that automation handles routine tasks while SOC analysts focus on high-risk threats.
- Automating alert prioritization allows human analysts to address the most critical threats instead of being overwhelmed by minor alerts.
Automated malware sandboxing can detonate and analyze suspicious files, but a SOC analyst should review findings before executing response actions.
4. Ensuring Security and Compliance
- Automated workflows must align with compliance requirements such as GDPR, HIPAA, & SOC 2.
- Access control and logging should be enforced to prevent automation abuse, such as unauthorized script execution.
- Audit trails should be maintained for all automated actions to support forensic investigations and regulatory compliance.
If an automated system blocks an IP suspected of malicious activity, audit logs should capture why the action was taken and who approved it.
5. Orchestration Across Multiple Security Tools
- SOC automation should integrate SIEM, SOAR, endpoint security, and cloud security platforms for a cohesive security strategy.
- A well-orchestrated system allows automation to:
- Collect logs from multiple security sources.
- Correlate data to identify attack patterns.
- Trigger appropriate response actions across different security layers.
If a SOAR platform detects a ransomware attack, it should automatically block the affected host in the firewall and revoke user access in IAM systems.
6. Handling False Positives and Tuning Automation
- Poorly configured automation can generate excessive false positives, leading to alert fatigue and unnecessary disruptions.
- Regular tuning and optimization of automation rules is necessary to improve accuracy.
- AI and machine learning models should be trained on real-world attack scenarios to improve detection precision over time.
If an automated threat detection system flags every login from a new device as suspicious, it could disrupt legitimate users and require constant manual intervention.
7. Incident Response Playbook Automation
- Automating incident response requires well-defined playbooks that outline step-by-step actions SOC automation should take.
- Playbooks should include:
- Initial investigation steps
- Automated containment actions
- Escalation procedures for human review
- Automated responses should be tested in sandbox environments before deployment.
A phishing attack playbook could:
- Automatically analyze email headers and attachments.
- Compare sender reputation with threat intelligence feeds.
- Quarantine suspicious emails and notify the SOC team for review.
8. Measuring the Effectiveness of SOC Automation
Key performance indicators (KPIs) should be defined to measure automation success, including:
- Mean Time to Detect (MTTD) – How quickly threats are identified.
- Mean Time to Respond (MTTR) – How fast incidents are mitigated.
- Reduction in manual workload – The percentage of tasks handled by automation instead of analysts.
If SOC automation reduces MTTD from hours to minutes while improving accuracy, it validates the effectiveness of automated workflows.
SOC Automation with CloudDefense.AI
CloudDefense.AI offers you a powerful CNAPP that can not only detect threats to your infrastructure but also prevent them from causing any harm. By using the next-gen AI-powered all-in-one security platform, you empower your SOC team to face cyber adversaries without having to worry about them affecting your business. Powerful tools such as Hacker’s View™ and Noise Reduction help your SOC team to think like a hacker and counter threats with minimum false positives. Focus on your growth, leave the security to us. Book a free demo now to witness the power of CloudDefense.AI!







