Holistic Infrastructure as Code
Experience Holistic Infrastructure as Code (IaC) Security
Dive into proactive, holistic infrastructure as code security with CloudDefense.AI’s IaC scanning. Discover, remediate, and seamlessly collaborate for fortified protection in the cloud-native landscape.
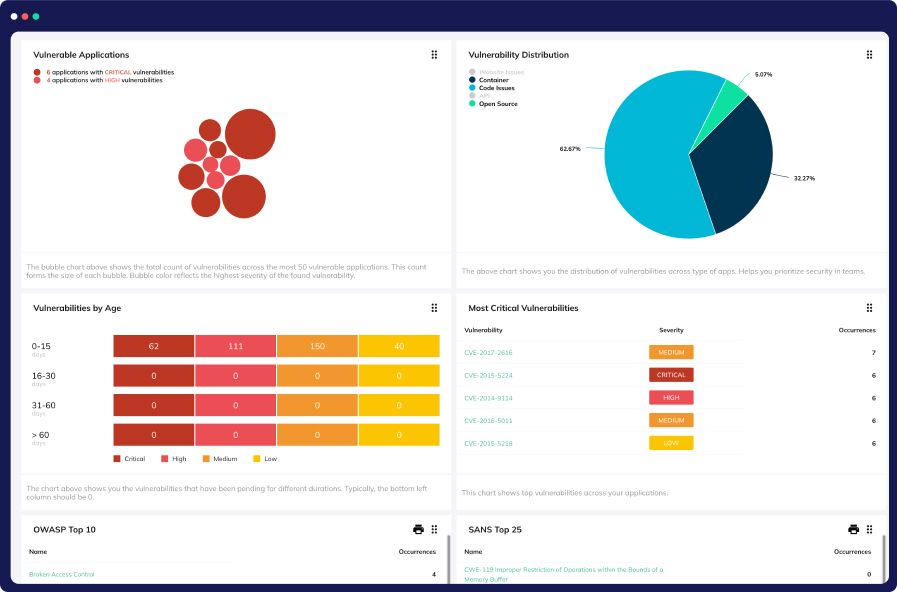
Cloud Security Risk Assessment
Find out which misconfigurations are lurking in your cloud
Infrastructure as Code
Streamline IaC Security: Spot, Solve, and Stay Secure!
Empower your CI/CD pipeline with our top-notch IaC Scanning feature. Identify and fortify IaC security seamlessly, so you can focus on building without worrying about vulnerabilities
Security-First Workflow
Effortlessly automate security scans across your Kubernetes clusters. KSPM takes the complexity out of monitoring, ensuring your clusters remain secure without manual intervention.
Real-Time Code Insights
Our comprehensive analysis of your live cloud environment identifies the top risks, empowering security teams to prioritize policy enforcement during the pipeline. Learn from real-time data, then shift your focus leftward.
Unified Policy Integration
Implement our integrated policies and compliance frameworks across your cloud setups and Infrastructure as Code (IaC). Plus, craft your own bespoke policies and frameworks for added protection.
Our Comprehensive Approach to IaC Scanning
Eliminate silos, enhance security. CloudDefense.AI unifies IaC scanning with one policy, bridging the gap between developers and security teams from source code to live environments.
Effortless IaC Security Assurance
Optimize your app development with CloudDefense.AI’s cutting-edge Automated Infrastructure as Code (IaC) security. Safeguard your projects by effortlessly identifying misconfigurations and secrets, ensuring continuous governance and effortless issue resolution within your DevOps workflows.
IaC Security Automation
CloudDefense.AI offers automated Infrastructure as Code (IaC) security scanning, preventing misconfigurations and exposed secrets throughout development.
Integrated Development Lifecycle
Our solution embeds security seamlessly across integrated development environments, CI/CD tools, repositories, and runtime environments.
Continuous Governance
CloudDefense.AI facilitates continuous governance, allowing you to consistently enforce security policies in your codebase.
Automated Misconfiguration Fixes
We provide automated misconfiguration fixes through pull requests, streamlining the resolution of security issues.
Seamless Pipeline Integration
Effortlessly integrate our platform into your pipeline, providing developers with real-time feedback, code review comments, and centralized visibility of security issues, all while streamlining remediation in your DevOps workflows.
Integrated Pipeline Enhancement
CloudDefense.AI seamlessly integrates with your DevOps pipeline, empowering developers with real-time feedback and security insights in their familiar IDEs, CI tools, and VCS.
Effortless Feedback Loop
Enable fast issue resolution through native VCS integrations that auto-generate code review comments for identified security issues, ensuring swift remediation.
Centralized Security Hub
Gain a unified view of all infrastructure-as-code (IaC) security concerns across repositories, with intuitive filtering and searching capabilities to locate and address vulnerabilities swiftly.
DevOps Workflow Integration
Drive collaboration and swift remediation by seamlessly connecting CloudDefense.AI with collaboration and ticketing tools, enabling automatic ticket generation and alerts for your DevOps teams.
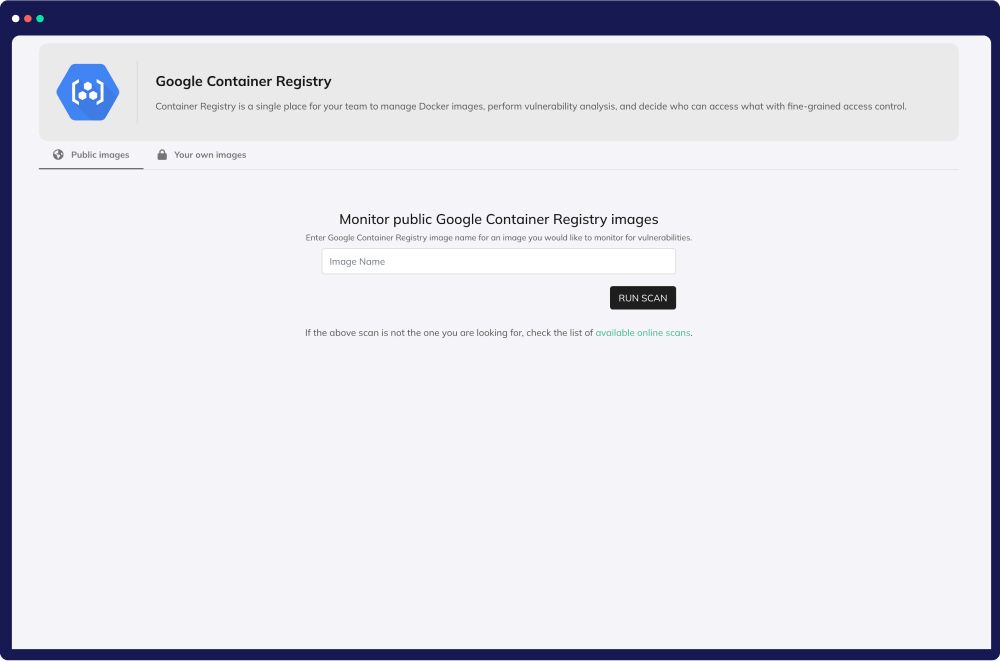
Find and fix IaC Misconfigurations
Discover and resolve IaC misconfigurations effortlessly with CloudDefense.AI’s cutting-edge IaC security scanning. Our automated tool identifies hundreds of issues, from exposed storage buckets to weak passwords, empowering your team to enhance security swiftly.
Comprehensive IaC Scanning
Our tool conducts in-depth scans, pinpointing vulnerabilities like publicly accessible storage buckets, unencrypted critical data, and more.
Automated Alerts
Receive instant notifications about misconfigurations, enabling proactive remediation and enhancing security posture.
Password Policy Enforcement
Identify and rectify weak password policies, strengthening your infrastructure's defenses against unauthorized access.
Encryption Key Rotation
Ensure encryption key rotation compliance, safeguarding sensitive data from potential breaches.
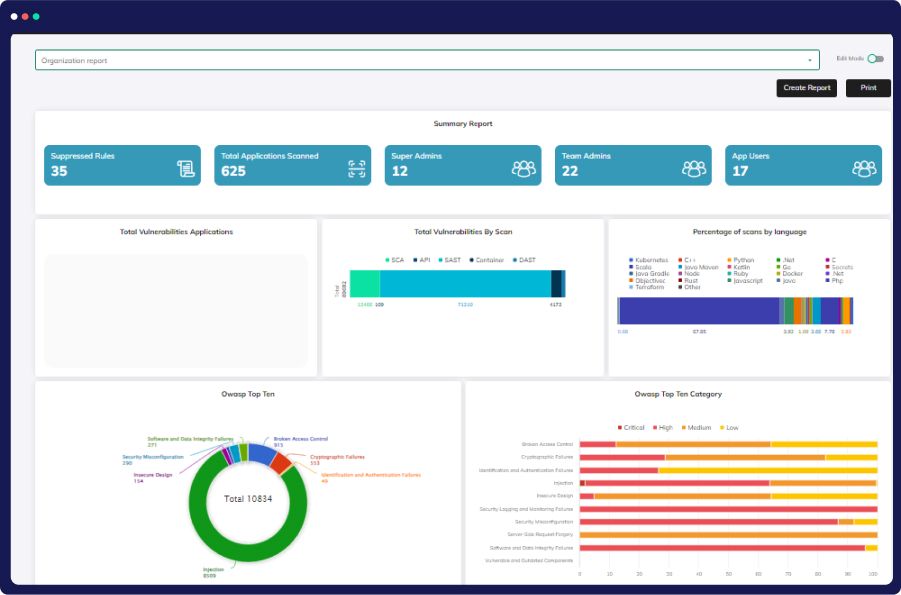
Context-Driven Actionable Feedback and Insights
Experience seamless policy enforcement and faster issue resolution with CloudDefense.AI’s feature-rich solution. Gain context-aware insights, actionable guidance, and effortless tracing from cloud to code for efficient compliance and security management.
Context-Aware Policy Enforcement
CloudDefense.AI empowers developers with contextual policy violations, ensuring efficient resolution by providing detailed guidelines and automatic remediations for misconfigurations.
Context-Driven Visibility
Prioritize security with context-based policies, highlighting higher severity violations, and dependencies to streamline decision-making and resource allocation.
Actionable Guidance
Receive clear, actionable guidance for each policy violation, facilitating quick and effective remediation of misconfigurations in your cloud infrastructure.
Cloud-to-Code Tracing
Trace cloud resources back to Infrastructure-as-Code (IaC) templates, identifying code owners for rapid issue resolution and seamless collaboration within your team.