When it comes to cybersecurity, understanding the difference between malware and viruses can make a huge difference in how you protect yourself online. A lot of people use these terms interchangeably — but they’re not the same thing.
The easiest way to think about it is — malware is the big, all-encompassing category for all kinds of malicious software, and a virus is just one type of malware — kind of like how every square is a rectangle, but not every rectangle is a square.
In this guide, we’ll break down what makes each one tick, share some real examples you might’ve encountered, and most importantly – help you protect your devices from both.
What is Malware?
Malware, short for malicious software, refers to any program or code designed to disrupt, damage, or gain unauthorized access to a computer system. It’s a digital threat created by cybercriminals to achieve various goals, such as:
- Stealing sensitive data
- Encrypting files and demanding ransom (ransomware)
- Monitoring user activity (spyware)
- Turning devices into botnets for further attacks
The numbers are alarming—over 450,000 new malware threats are detected daily, costing businesses billions annually. Malware often spreads through unsafe downloads or suspicious links. Staying vigilant and adopting strong cybersecurity practices are your best defenses against these threats.
Types of Malware
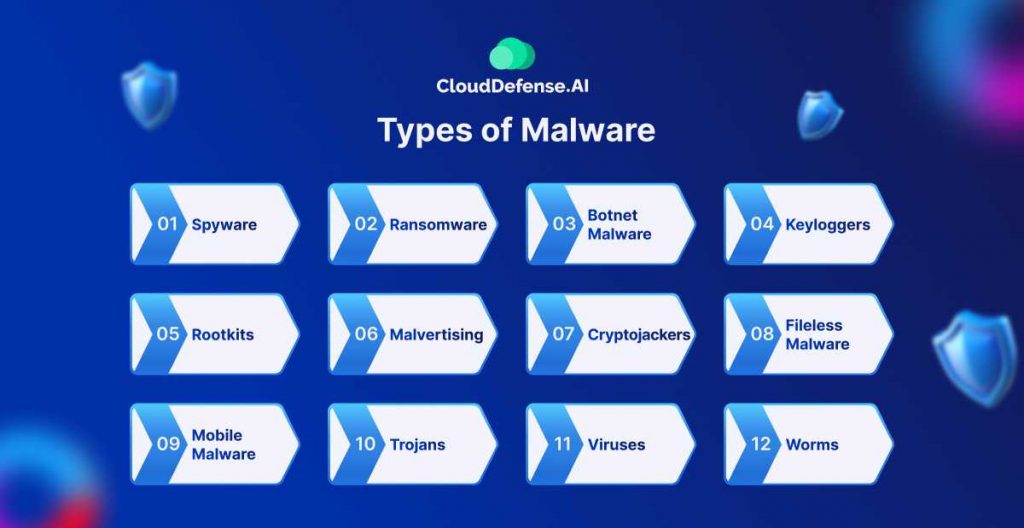
Let’s break this down simply. Malware comes in different forms, each designed to cause harm in its own way. Here are the key types:
Common Types of Malware (Including Viruses)
Malware isn’t just one thing — it comes in all shapes and sizes, each with its own sneaky tactics. Viruses are just one type, but there’s a whole lineup of threats out there. Here’s a quick rundown of the most common ones you should know:
- Spyware: This one quietly collects information about you — your browsing habits, passwords, even payment details — and sends it all back to the attacker.
- Ransomware: One of the nastiest types of malware, ransomware locks up your files or steals your data, then demands a ransom to get it back. Pay or lose it all.
- Botnet Malware: Once your device is infected, it becomes part of a larger botnet — a network of hijacked devices used for attacks like spamming, DDoS, or spreading more malware.
- Keyloggers: As the name suggests, keyloggers record every keystroke you type, making it easy for attackers to steal passwords, credit card numbers, or anything else you type.
- Rootkits: These are designed to hide deep inside your system, making it extremely hard to detect and remove the malware they protect.
- Malvertising: Ever clicked a suspicious-looking ad? Malvertising hides malware inside online ads, even on legit sites — click the wrong one and you’re infected.
- Cryptojackers: This sneaky malware uses your computer’s processing power to secretly mine cryptocurrency for the attacker, slowing down your system while they profit.
- Fileless Malware: Unlike traditional malware, this one doesn’t install files onto your system. Instead, it hijacks legitimate programs or processes, making it even harder to detect.
- Mobile Malware: Mobile devices aren’t immune. Malicious apps can steal data, spy on you, or even lock your phone until you pay up.
- Trojans: These pretend to be legitimate software — maybe even something useful — but once installed, they open the door for all kinds of malware to enter your system.
- Viruses: Old-school but still dangerous, viruses attach themselves to files or programs. They spread when you open infected files, and they can do anything from corrupting files to crashing your whole system.
- Worms: Worms don’t even need you to do anything — they spread all on their own by exploiting security flaws or sending themselves to your contacts.
Each type poses serious risks, and understanding them is your first step in staying secure.
Malware Examples
- Emotet: It started as a banking trojan but quickly became a top threat. Emotet spreads through phishing emails, steals data, and installs more malware.
- Cryptojacking: This is malware that secretly uses your computer to mine cryptocurrency. You don’t see Cryptojacking, but it slows everything down.
- Ransomware (like WannaCry): This locks your files and demands payment to release them. WannaCry hit a lot of companies and organizations, costing billions in damages.
What is a Virus?
A virus is a type of malware that attaches itself to a legitimate file or program. Once you open or run that file, the virus activates and can spread to other files or devices. It can:
- Corrupt data
- Slow down your system
- Destroy important files.
Viruses are usually spread through things like email attachments, downloads, or infected websites. Remember those chain emails from the 90s that said “Forward this to 10 friends or else”? Computer viruses work kind of like that — they spread by copying themselves!
They rely on users to open or execute the file, making it important to be cautious with what you download and click on. The impact can be significant, especially if it spreads across a network, affecting multiple devices or systems.
Types of Viruses
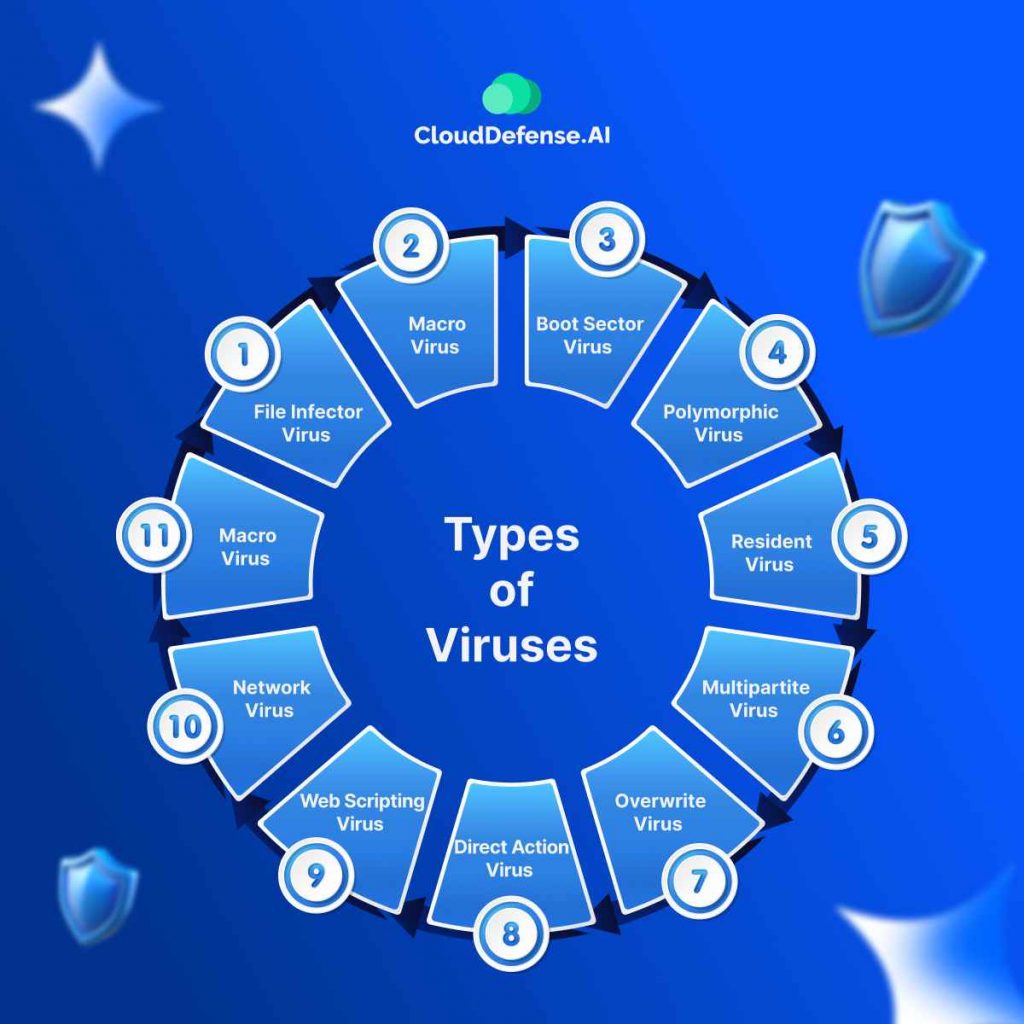
Viruses come in different types, each with its own way of spreading and causing harm. Here’s a breakdown:
- Macro Viruses – These are designed to exploit macro languages in applications like Microsoft Office. They spread primarily through email attachments and shared documents.
- File Infector Viruses – These attach to executable files. When you run the infected file, the virus spreads to other files on your system.
- Macro Viruses – Target macros in applications like Microsoft Word or Excel. They spread when you open an infected document or file.
- Boot Sector Viruses – Infect the boot sector of your computer. When your system starts, the virus activates and can damage the system.
- Polymorphic Viruses – Change their code to avoid detection by antivirus programs, making them more difficult to identify and remove.
- Metamorphic Viruses – Like polymorphic viruses, these change their entire code every time they replicate, making them harder to detect.
- Resident Viruses – These embed themselves in your system’s memory. They can spread without needing an infected file to activate.
- Multipartite Viruses – These can infect both files and the boot sector, using multiple methods to spread within a system.
- Overwrite Viruses – These destroy the content of infected files by overwriting them with malicious code. Once infected, the original file can’t be recovered.
- Direct Action Viruses – These activate immediately when the infected file is executed. They carry out their payload and then typically delete themselves or lay dormant until triggered again.
- Web Scripting Viruses – These exploit vulnerabilities in web browsers. They run malicious scripts directly from compromised websites and can infect a system without downloading a file.
- Network Viruses – These spread across networks, moving between connected devices by exploiting security flaws in network protocols or weakly secured devices.
Virus Examples
- ILoveYou Virus: A famous virus that spread through email attachments in 2000. This virus wiped out files and caused widespread damage by replicating and sending itself to contacts in the infected device’s address book.
- Sasser: A virus that targeted Microsoft Windows systems. Sasser spread rapidly through vulnerabilities in the operating system, causing system crashes and slowing down networks.
- Storm Worm: A virus that infected millions of computers in 2007. It spread through malicious email attachments and created a botnet used for spam and other attacks.
The Difference Between Malware and a Virus
As we thoroughly discussed malware and virus in the previous sections, let’s get straight to the differences part. If you think malware and virus are the same thing, you’re not alone. It’s a common misconception. But the difference is critical in understanding how each one impacts your system and how you defend against them.
Here is the important thing to remember: “All viruses are malware, but not all malware is a virus.”
Malware is the broad term that refers to any software or code designed to harm or exploit your system. It’s a category.
- This includes viruses, ransomware, worms, spyware, and more.
- The key takeaway: Malware is the “umbrella” term.
Virus, on the other hand, is a specific type of malware. It’s like saying all cats are animals, but not all animals are cats.
- A virus is a malicious program that attaches itself to a legitimate file or program and spreads when that file is executed.
- A virus requires a host file to function, and it usually needs user interaction to spread (such as opening a file or running a program).
Key Differences Between Malware and a Virus
To make the distinction clearer, let’s break it down into key aspects:
- Scope of Threat: Malware is a category, while a virus is a specific type of malware. It’s like saying malware is the general threat, and the virus is a specific method within that threat.
- Spread Mechanism: A virus relies on user actions—opening files, running programs—to spread. Malware, on the other hand, can spread through various channels: email attachments, networks, downloads, or even vulnerabilities in software.
- Impact on the System: A virus usually disrupts or corrupts files, making your system unstable. Malware is more varied: it can steal data, lock files (ransomware), spy on your activities, or even control your system remotely (like a botnet).
- Detection and Prevention: Viruses are relatively easier to detect because they often have a predictable spread. Malware is more complex. For example, ransomware locks your files, while spyware tracks your behavior without you even noticing.
So, Why Does It Matter?
Knowing the difference matters because it affects how you protect your system. The methods for stopping malware versus a virus are not always the same.
For instance, if you’re dealing with a virus, keeping your files clean and scanning for malicious attachments can help. But for malware, you need a broader approach—things like patching vulnerabilities, monitoring network traffic, and using a multi-layered defense.
Comparison Table
| Feature | Malware | Virus |
| Definition | Any malicious software designed to harm or exploit a system | A specific type of malware that infects files and spreads |
| Type | Includes viruses, worms, ransomware, spyware, etc. | Only viruses that attach to files and programs |
| Spread Mechanism | Can spread through emails, downloads, networks, software flaws | Spreads through infected files or programs executed by the user |
| Impact | Can steal data, lock files, spy, or damage systems | Primarily corrupts or deletes files |
| Detection | Harder to detect because of the variety of types | Easier to detect via infected files or programs |
| Prevention | Requires multiple approaches (patching, monitoring, etc.) | Focus on avoiding infected files or running unknown programs |
Protection Against Malware and Viruses
Staying safe from malware and viruses doesn’t have to be complicated — but it does take a bit of awareness and some smart habits. Here’s how you can protect yourself:
- Keep your software updated – Outdated apps and operating systems are easy targets for malware and viruses. Regular updates patch those security holes.
- Use trusted antivirus and anti-malware tools – These programs can catch threats before they have a chance to do any damage.
- Think before you click – Suspicious email attachments, weird pop-ups, or sketchy downloads? Avoid them like the plague.
- Stick to legit sources – Whether it’s apps, files, or software, always download from official websites or app stores.
- Back up your data – Even with the best protection, things can go wrong. Having backups ensures you don’t lose everything if malware does sneak in.
- Use strong, unique passwords – Some malware is designed to steal passwords. Using different, complex passwords for each account can limit the damage.
Bottom line — a mix of good tools, common sense, and staying alert is your best defense against malware and viruses.
Wrapping Up!
At the end of the day, knowing the difference between malware vs viruses actually helps you protect your stuff. Malware covers all kinds of bad software, and viruses are just one type under that big umbrella. Simple as that.
And, you don’t need to be a cybersecurity pro to stay safe. A little basic awareness — like avoiding weird downloads, keeping your software updated, and using solid antivirus tools — goes a long way. And now that you know what’s what, you’re already way ahead of most people.







