A honeypot is a cyber trap that is designed to lure cybercriminals into a controlled environment. Much like how Winnie-the-Pooh can’t resist a pot of honey, hackers find it hard to pass up t he greed of a honeypot.
Used by both criminals and cybersecurity professionals, honeypots serve as a tool to attract and study cyber attackers. For cybersecurity teams, honeypots provide valuable insights into the tactics and methods used by hackers, allowing businesses to better understand and defend against sophisticated cyber threats.
Keep reading to learn more about the concept of honeypots, how they work, and the role they play in cybersecurity.
What is a Honeypot?
A honeypot is a security mechanism designed to act as a decoy, luring cyber attackers and detecting, deflecting, and studying hacking attempts. It mimics a high-value target, such as a server or database, appearing vulnerable to entice attackers. By setting up a honeypot, security teams can observe the methods and behaviors of cybercriminals in a controlled environment, gaining valuable insights into potential threats and attack patterns.
Honeypots often use hardened operating systems to minimize real exposure while appearing exploitable to attackers. This strategy not only helps in gathering intelligence on cyber threats but also reduces the risk of false positives, making it a valuable tool for improving overall cybersecurity measures.
How do Honeypots Work?
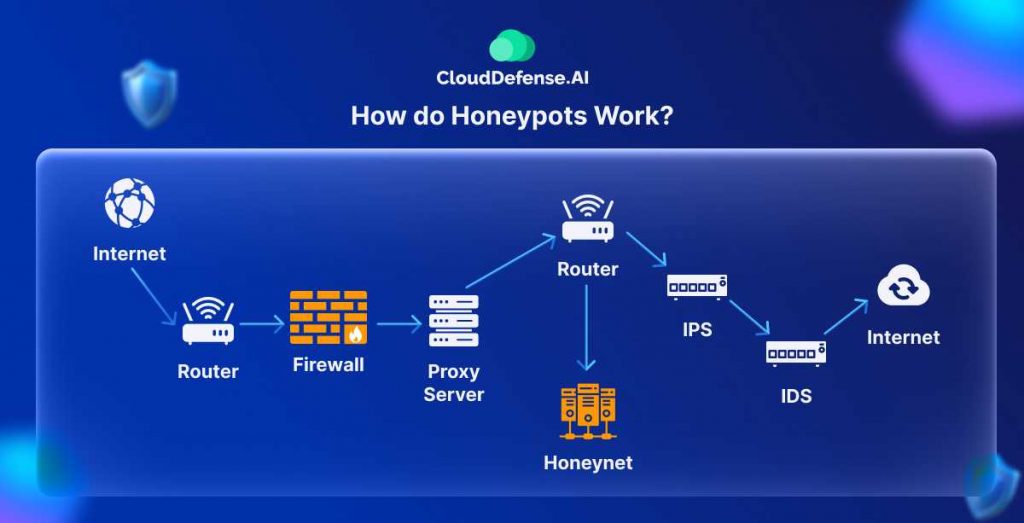
A honeypot works by mimicking a real computer system complete with applications and data to deceive cybercriminals into thinking it’s a legitimate target. These systems are designed to appear vulnerable, often by including deliberate security weaknesses such as open ports, weak passwords, and other exploitable features.
For example, a honeypot might simulate a company’s customer billing system, enticing attackers seeking to steal credit card information. Once attackers engage with the honeypot, their activities are closely monitored, allowing security teams to track their behavior and gather valuable insights.
Honeypots are typically placed in strategic locations such as a demilitarized zone on the network, which keeps them isolated from the main production network while still appearing to be part of it. This placement allows security professionals to monitor attackers from a safe distance, minimizing the risk to the actual network.
Some honeypots are positioned outside the external firewall to detect attempts to breach the internal network. Regardless of their placement, honeypots are isolated to ensure they do not pose a risk to the production environment.
Types of Honeypot Deployments
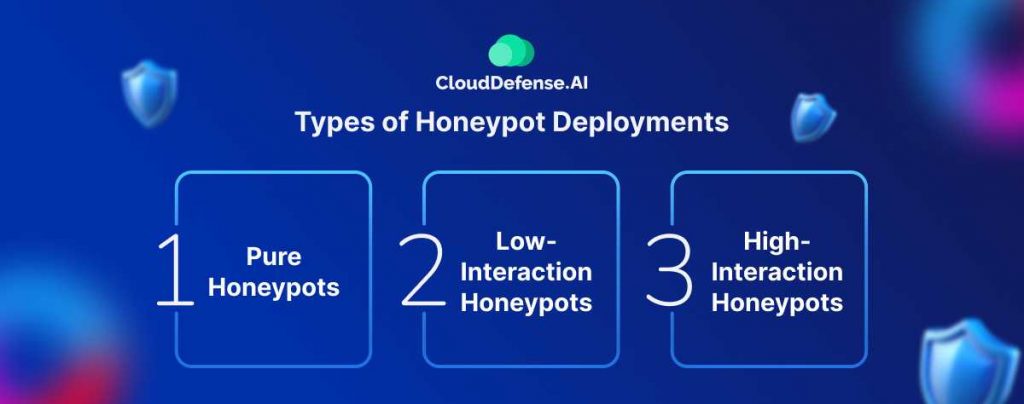
Honeypots are categorized into three types based on the level of interaction and the extent of malicious activity they allow:
1. Pure Honeypots
These are complete production systems designed to monitor attacks via bug taps on the link connecting the honeypot to the network. They are relatively unsophisticated, capturing a broad range of attack data without active interaction or complexity.
2. Low-Interaction Honeypots
These honeypots mimic services and systems that typically attract cybercriminals. They are designed to gather data from widespread, automated attacks like those from botnets and worms. Low-interaction honeypots provide a means to collect data from unsophisticated, blind attacks, offering insights with minimal maintenance and risk.
3. High-Interaction Honeypots
These are elaborate setups that replicate real production environments, allowing cybercriminals to engage in a wide range of activities. High-interaction honeypots do not limit the actions of attackers, thereby offering extensive insights into their behavior and methods. However, they require significant maintenance, expertise, and additional technologies such as virtual machines to ensure the real system remains secure.
Honeynet: A Network of Honeypots
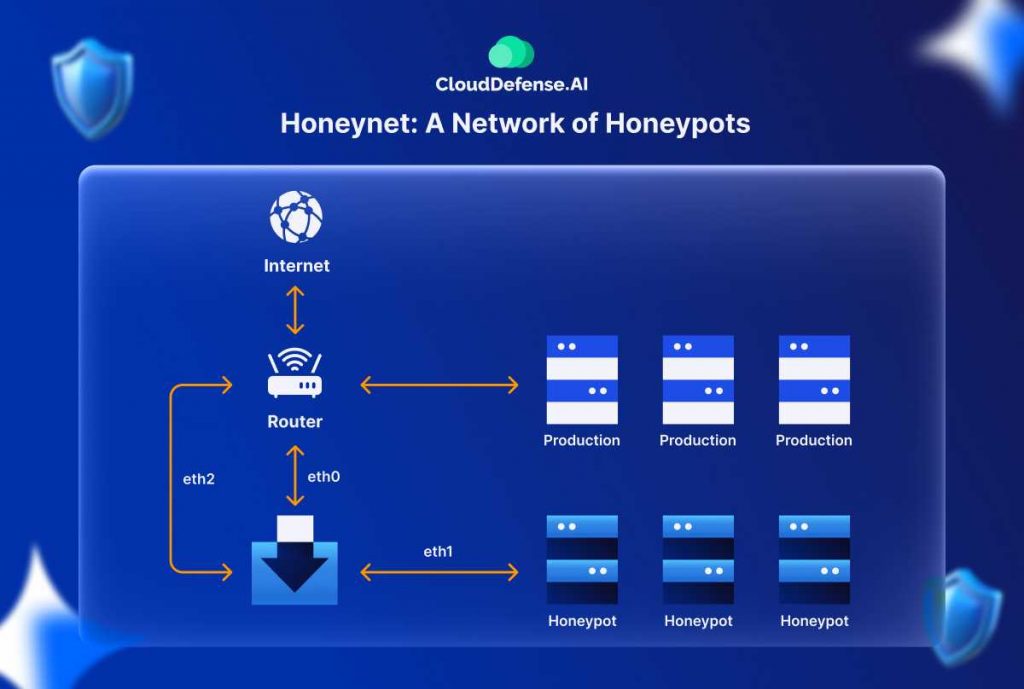
A honeynet is a sophisticated network of multiple honeypots designed to attract, monitor, and analyze cyber attackers. By simulating a realistic network environment, a honeynet helps organizations track an attacker’s movements and interactions with different network points, offering valuable insights into their tactics and strategies. The central component, known as the honeywall, directs attackers toward the honeypots, where their activities can be closely monitored and controlled.
Honeynets create a convincing illusion of a breached network, making them more effective in deceiving attackers. This setup not only tracks individual intrusions but also observes how attackers move across the network, enhancing the overall security posture.
Deception technology often accompanies honeynets, integrating advanced security tools like next-generation firewalls and intrusion detection systems. These technologies automate responses to threats in real-time, providing a robust defense mechanism against cyberattacks and significantly improving an organization’s cybersecurity resilience.
Spam Trap: An Email Honeypot
Spam traps, also known as email honeypots, are essential tools for Internet Service Providers (ISPs) to manage and minimize spam. These are fake email addresses designed to attract and identify spammers. Since legitimate emails are unlikely to be sent to these addresses, any email received is flagged as spam, enabling ISPs to block spammers and enhance inbox safety.
Example
There are several types of spam traps. Username typos, such as “jhon@cloutdefense.ai” instead of “john@clouddefense.ai,” catch errors and divert these emails to spam folders. Expired email accounts and abandoned domain names are also used as spam traps by providers. Purchased email lists, often filled with invalid addresses, are another source, flagging unauthorized senders as spammers and leading to blacklisting.
Backdraws
However, spam traps have limitations. They can generate backscatter (incorrect automated bounce messages) and inadvertently taint legitimate email addresses that interact with them. Once exposed, spammers might exploit these traps by sending legitimate content, reducing their effectiveness. Moreover, well-meaning individuals might mistakenly email these addresses.
Accidentally hitting a spam trap can harm an organization’s reputation and email deliverability. ISPs may block or blacklist the sender’s IP address, and anti-spam databases could filter out future emails, severely impacting communication efforts. Despite their challenges, spam traps are invaluable for identifying spammers and protecting email systems.
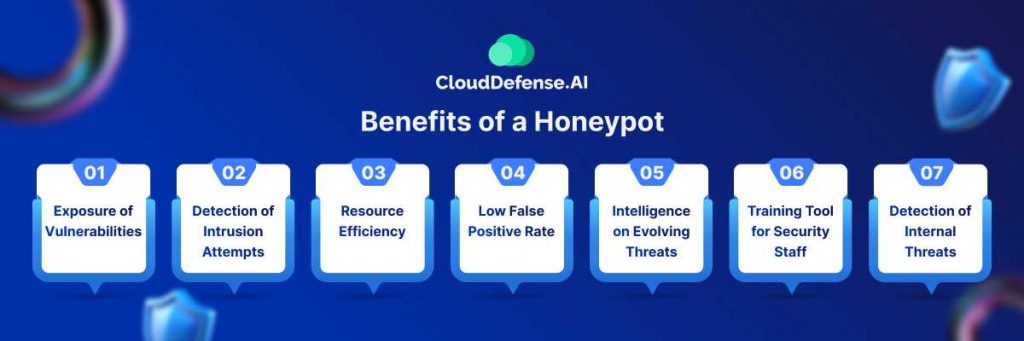
Benefits of a Honeypot
Honeypots offer a good number of benefits to companies looking to boost their cybersecurity methods. Here are a few of them mentioned below:
1. Exposure of Vulnerabilities
Honeypots are effective in exposing vulnerabilities in major systems, such as IoT devices. By simulating a real system, they provide insights into how attackers operate and what weaknesses they exploit. This information is crucial for suggesting improvements in security measures, ensuring that similar vulnerabilities in actual systems are addressed and mitigated.
2. Detection of Intrusion Attempts
One of the key advantages of honeypots is their ability to detect intrusion attempts. Since honeypots are not meant to receive legitimate traffic, any activity logged is likely a probe or intrusion attempt. This clear distinction makes it much easier to identify and analyze attack patterns, such as recurring IP addresses or specific methods used by attackers, without the interference of legitimate traffic, which can obscure such tell-tale signs in a real system.
3. Resource Efficiency
Honeypots are resource-efficient tools. They require minimal hardware, often set up using old or repurposed computers. Additionally, many ready-made honeypot software solutions are available from online repositories, which reduces the amount of in-house effort needed to deploy them. This makes honeypots an accessible option for organizations looking to enhance their cybersecurity without significant investment in new resources.
4. Low False Positive Rate
Compared to traditional intrusion-detection systems (IDS), honeypots produce a significantly lower false positive rate. Since honeypots are designed to attract malicious traffic, any interaction with them is likely to be a genuine threat. This clarity helps prioritize security efforts and reduces the noise generated by false alerts. Moreover, the data collected from honeypots can refine IDS configurations, further enhancing the accuracy of security alerts.
5. Intelligence on Evolving Threats
Honeypots provide valuable intelligence on evolving threats. They collect information on attack vectors, exploits, and malware used by attackers. This continuous stream of data helps security teams stay ahead of emerging threats and adjust their defenses accordingly. In the case of email traps, honeypots can also provide insights into spamming and phishing techniques, enabling organizations to bolster their defenses against these common threats.
6. Training Tool for Security Staff
Honeypots serve as excellent training tools for security staff. They offer a controlled and safe environment to study attacker behavior and understand different types of threats. By focusing exclusively on the simulated threats within the honeypot, security personnel can gain a deeper understanding of cyber attacks without the distraction of real network traffic. This hands-on experience is invaluable for preparing staff to handle real-world security incidents.
7. Detection of Internal Threats
Honeypots are not just effective against external threats; they are also useful for detecting internal threats. They can reveal vulnerabilities in permissions and highlight insider activities that may go unnoticed by perimeter defenses and firewalls. For instance, a honeypot can detect an employee attempting to steal sensitive information, providing early warning and enabling swift action to prevent data breaches.
Honeypot Limitations
While honeypots are valuable tools for gaining insights into cyber threats and attacker behavior, their limitations must be carefully managed.
1. Limited Data Collection
One of the primary limitations of honeypots is that they only gather data during an active attack. If no attempts are made to access the honeypot, there is no information to analyze. This dependency on attack activity means that honeypots might not provide continuous or comprehensive insights into potential threats, especially during periods of inactivity.
2. Isolated Network Limitations
Honeypots are designed to capture malicious traffic by isolating it from the main network. However, this isolation can be a double-edged sword. If attackers suspect that a network is a honeypot, they will avoid it, resulting in no valuable data being collected. This selective targeting can limit the effectiveness of honeypots, as sophisticated attackers may bypass them entirely, leaving security teams without critical information.
3. Distinguishability
Experienced hackers can often distinguish honeypots from legitimate production systems using system fingerprinting techniques. Honeypots, despite their design to mimic real systems, may exhibit subtle differences that alert savvy attackers to their true nature. This capability to differentiate can render honeypots less effective, as attackers may alter their behavior or avoid interaction altogether once they identify the honeypot.
4. Risk to Production Systems
While honeypots are generally isolated from real networks, they still require some form of connection for administrators to collect data and manage the honeypot. This connection, albeit indirect, can pose a risk to production systems. High-interaction honeypots, which are designed to provide a more realistic environment and allow attackers to gain root access, are particularly risky. These sophisticated honeypots aim to attract and engage attackers deeply, but if not managed properly, they could inadvertently provide a pathway for attackers to reach actual network resources, thereby compromising security.
Conclusion
Honeypots are powerful cybersecurity tools designed to lure and study cyber attackers. By simulating vulnerable systems, they provide invaluable insights into attacker behaviors and emerging threats.
While they have limitations, such as potentially being identifiable and only collecting data during attacks, their benefits in improving security defenses and training security teams are significant.
Implementing honeypots can enhance an organization’s overall cybersecurity infrastructure, making them an essential component of modern defense strategies.







