The rapid advancement of cloud-native Application technology and the massive boom of SaaS application usage have been some of the biggest trends in recent times. Most of the businesses in the market are gradually transitioning from on-premises infrastructure to cloud-based platforms and enabling their application to harness the limitless potential of cloud technology.
However, as cloud-native applications exploded, so did the number of threats. Cloud-native application security arrived as a game changer as it revolutionized how organizations write code, build applications, and deploy and secure sensitive data.
Application security is basically a practice that enables an organization to protect its application from vulnerability and ensure the integrity, availability, and confidentiality of the application and data. The primary goal is to implement security measures to secure SDLC and mitigate attacks, coding errors, and design flaws.
Process, technology, and people serve as the three primary pillars of application security, and every pillar depends on the other. Even though organizations are trying to replace people with automation, it brings out a fundamental question: what if automation and technology become a threat to the cloud-native application?
Now, you must be speculating what it is and how to respond to it. Well, to help you understand, we have created this blog that will take you through the evolution of cloud-native application security.
Without further ado, let’s dive in!
Application Security From 2000-2015
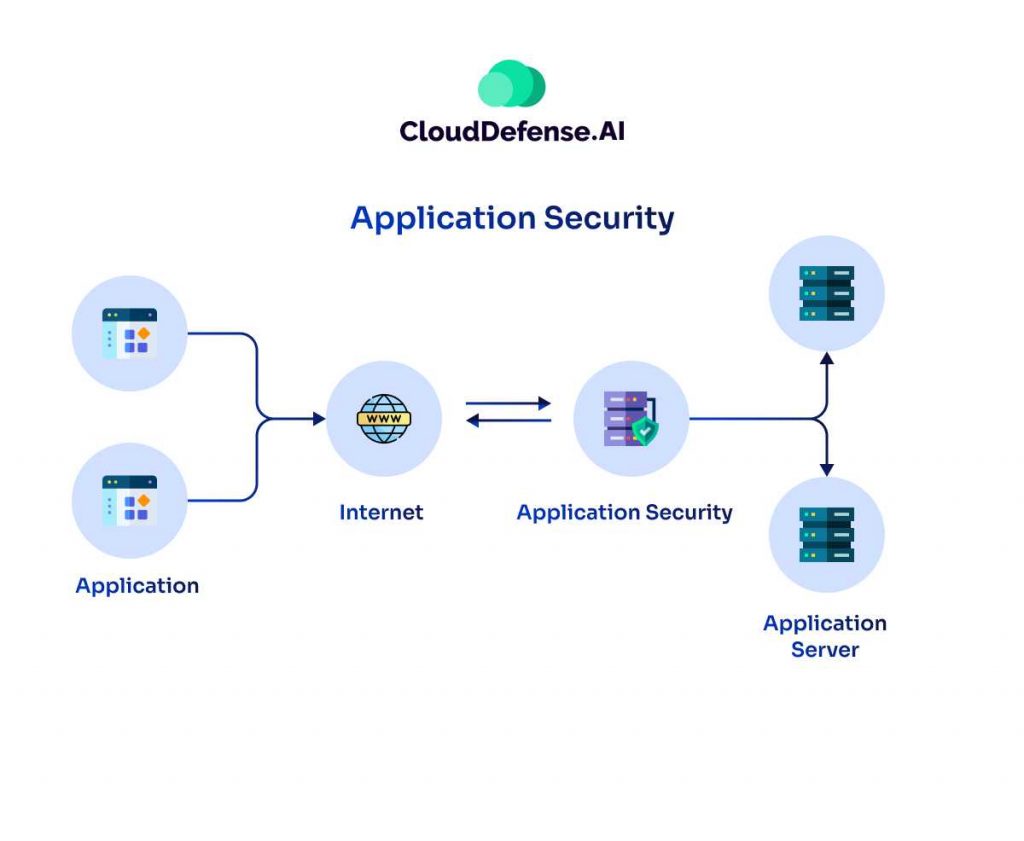
From the year 2000 to 2015, the industry saw a massive shift from desktop applications and started adopting web-based applications. As more technologies and functionalities came into play, web-based applications got more attention from organizations.
However, the massive rise in usage also gave rise to numerous vulnerabilities, and due to this, application security became a serious consideration for everyone.
Cross-site scripting, cross-site request forgery, and SQL injection were some popular vulnerabilities that allowed attackers to exploit them and get inside the application. However, organizations were able to address the rising security concerns with security tools like static application security testing (SAST), interactive application security testing (IAST), and dynamic application security testing (DAST).
With time, these testing tools also got more refined and sophisticated and were able to identify many advanced threats that previous generations couldn’t. As businesses started to understand the importance of application security and more security technology was introduced, AppSec went beyond just being a perimeter-based solution.
It emerged as a comprehensive solution that takes a proactive and holistic approach to the security of applications. The rapid increase in the importance of application security also prompted OWASP to research new vulnerabilities and come up with the top 10 list, which will help organizations strengthen their application security accordingly.
2015 Onward: Secure Deployment in the Cloud Era
The arrival of cloud technology and widespread commercial adoption of the cloud environment brought a considerable transformation to application security. As organizations started migrating their applications to cloud platforms, it changed how AppSec is defined and works.
Before the cloud era, application security was mostly about enforcing security policies that would secure the deployment practice. The application security emphasized securing data transmission, enforcing access control, and safeguarding the servers.
However, the cloud era brought a huge change and expanded the boundaries of AppSec. In this cloud era, AppSec covers different aspects of the application security landscape to ensure comprehensive security. It encompasses secure coding practice, secure design, shift left approach, zero trust policies, threat modeling, incident response, and other aspects of security testing.
The massive change in AppSec came due to the fact cloud computing works on a shared responsibility model. As opposed to traditional infrastructure, where the organization had complete control over the application layer, security and infrastructure.
In modern cloud platforms, the cloud service provider takes care of the infrastructure that cloud users use, while the cloud users have responsibility for the security of their applications and data. The shared responsibility brought a major change in the operations of AppSec and transformed it into a joint effort.
However, shared security responsibility also introduced new attack vectors in the cloud environment and made applications and data vulnerable through misconfigurations and cloud assets.
The addition of new functionalities also brought many added responsibilities as AppSec has to address a wide range of sophisticated and nuanced cloud threats along with traditional vulnerabilities. However, what defines a modern application in today’s cloud environment that helps in addressing modern cloud security threats? Well, we need to properly define modern applications, which will give us the answer.
Defining the Modern Application
To properly address all the modern application threats, we need to define the modern application. However, the definition of application isn’t clear to everyone as not everyone is aware what are the components of an application.
When considering the application lifecycle, many tend to overlook the dependencies that include tools, processes, automation, and people who helped create and move it to the cloud. However, overlooking different components of modern applications, especially the dependencies, won’t allow any organization to take a modern and proactive approach to AppSec.
Modern cloud threats have evolved in many ways, and they are getting advanced from time to time, causing an increase in sophisticated attacks on the software chain. Basically, the way your organization defines its application will reflect on the security posture of the application.
To ensure the optimum security of the application, your organization needs to consider every component of the application, including the third-party dependencies. From codes to the four Cs of cloud security, an organization should cover everything when defining a modern application.
The primary goal of the application security is to stay compliant with the CIA triad and ensure integrity, availability, and confidentiality of the customer data all the time. However, to cope with modern threats, organizations should work towards adding a fifth “C” (continuous integration and continuous delivery pipeline).
CI/CD Pipelines: The Fifth “C” of Cloud-Native Application Security
With time, attackers are getting sophisticated with their attacks on cloud-native applications as they provide direct access to the cloud infrastructure and network. Due to this, modernizing the approach toward AppSec has become a need of the hour. Adding a fifth “C,” which is the CI/CD pipeline, will help strengthen modern AppSec.
As a result, the organization will be able to address threats more diligently. CI/CD pipeline not only helps streamline the application development process but also acts as a medium through which all the proprietary and third-party code passes.
The integration of AppSec into the CI/CD pipeline enables developers to introduce security by utilizing vulnerability scanning tools, automated security testing, and code analysis.
It is the duty of the developer to introduce security at every stage of the development pipeline, as it will enable the team to identify and mitigate vulnerabilities early in the development stage. Most importantly, it brings out the approach where security should be treated as a code, enabling developers to prevent any issue from reaching the deployment stage.
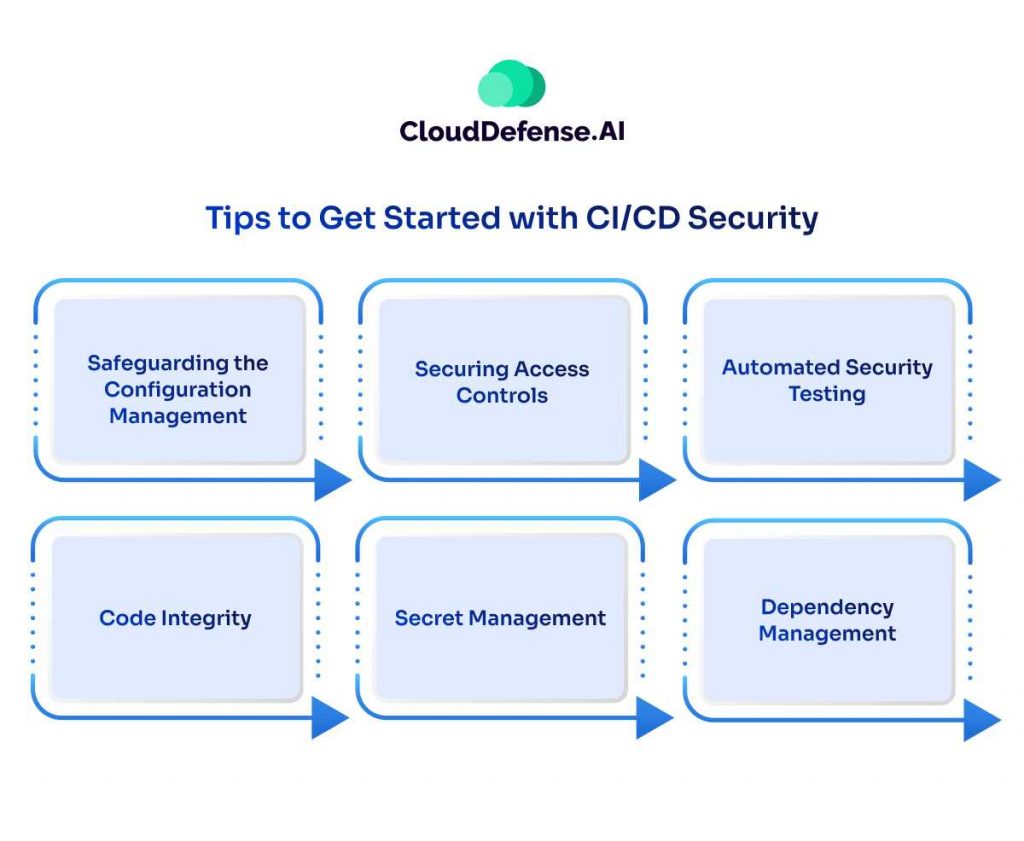
Tips to Get Started with CI/CD Security
CI/CD pipelines have enabled developers to swiftly and efficiently deploy software in the market, but they have also brought security challenges.
So, it has become necessary to implement security into the CI/CD pipeline to ensure the secure delivery of applications. To protect the CI/CD pipeline and ensure it is free from threats, unauthorized vulnerabilities, and other risks, you will have to employ the following best practices:
Safeguarding the Configuration Management
To introduce security into the CI/CD pipeline, you need to enforce secure configuration practices to every component in the pipeline.
It should not only cover the build server but also deployment tools and version control systems to ensure thorough implementation. It is vital to regularly review them and update the configuration to ensure they align with the defined security guidelines and best practices.
Securing Access Controls
You need to deploy the right access control to CI/CD tools along with the infrastructure and repositories. In addition, you also need to implement strong authentication, like multi-factor authentication, to ensure only the authorized and right entities would be able to access the pipeline components.
Automated Security Testing
Another great way to get started with CI/CD security is to integrate automated security testing into pipelines, which include SAST, DAST, vulnerability scanning, and SCA. The automated testing will not only uncover threats in the development stage but also identify numerous vulnerabilities that might allow attackers to exploit the application.
Code Integrity
Codes along with artifacts passess through CI/CD pipeline before reaching the deployed stage so they need to be free from flaws and unauthorized modifications.
The best way to safeguard the codes and artifacts is by enforcing checksum verification, code signing, creating a secured artifact repository, and other methodologies. These methodology will ensure only the validated users have access to the codes and authority to make changes.
Secret Management
Secrets serve as the gateway to applications, so it is important to protect all the secrets and prevent them from getting exposed. The secrets usually include login credentials, encryption keys, API keys, and others that are used in the CI/CD pipeline.
The best way to manage and protect all the secrets is by storing them in secured storage or encrypting them to prevent unauthorized access. Utilizing platforms like CloudDefense.AI can streamline your secret management and help you protect all your secrets in an efficient way.
Dependency Management
Along with the secrets, you also have to secure and manage third-party dependencies that are used for creating applications in the CI/CD pipeline. You need to update the dependencies and patch them on a regular basis to eliminate any risks or vulnerabilities that might enable attackers to impact the supply chain.
Modern AppSec For The Cloud
Modern application security is not only about securing the perimeter, as advancements in the cloud have allowed it to go beyond the traditional definition. Modern AppSec for the cloud now encompasses securing the CI/CD pipeline as it serves as the medium that helps in the development and deployment of codes for an application.
Building an application is a complicated task as it involves a lot of components, and developers have to work together with the operation and security team to ensure a secure application. However, the security of modern applications depends a lot on how you secure the CI/CD pipeline, as all the codes are secure.
When you consider a modern AppSec, it is not only about securing the application but also securely configuring the CI/CD pipeline, which facilitates the development of the app. Ensuring security from the beginning of the application development, especially implementing security measures in the pipeline, will help in ensuring comprehensive application security.
Most importantly, developers have to be responsible for the security of the code that goes through the CI/CD pipeline, which will aid in the process of securing the app. Along with the CI/CD pipeline, you also have to secure the cloud because the security of the application depends upon the security of the underlying infrastructure (cloud).







