Kubernetes Security Posture Management (KSPM)
Kubernetes Security Posture Management (KSPM)
Effortlessly identify & remediate misconfigurations in your K8S clusters. Your All-in-One Solution for Automated Risk Detection, Prioritization, and Remediation in Cloud-Native Environments.
Cloud Security Risk Assessment
Find out which misconfigurations are lurking in your cloud
Kubernetes Security Posture Management (KSPM)
See Beyond the Veil: Your Ultimate K8S Cluster Security Companion
Unveil, Secure, and Thrive! Empower your Kubernetes security with our top-tier KSPM Solution. Safeguard your clusters like never before, addressing unique risks and ensuring compliance effortlessly.
Automated Cluster Scans
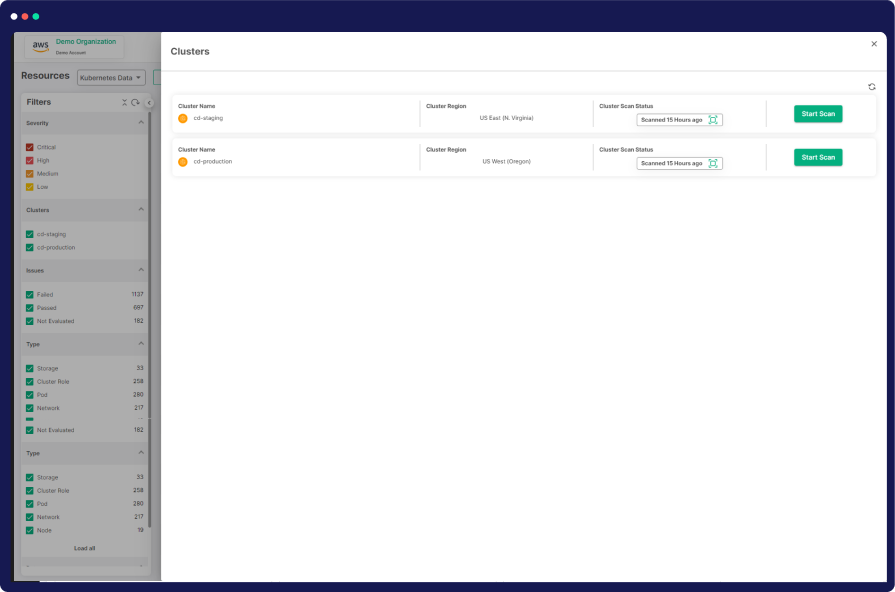
Effortlessly automate security scans across your Kubernetes clusters. KSPM takes the complexity out of monitoring, ensuring your clusters remain secure without manual intervention.
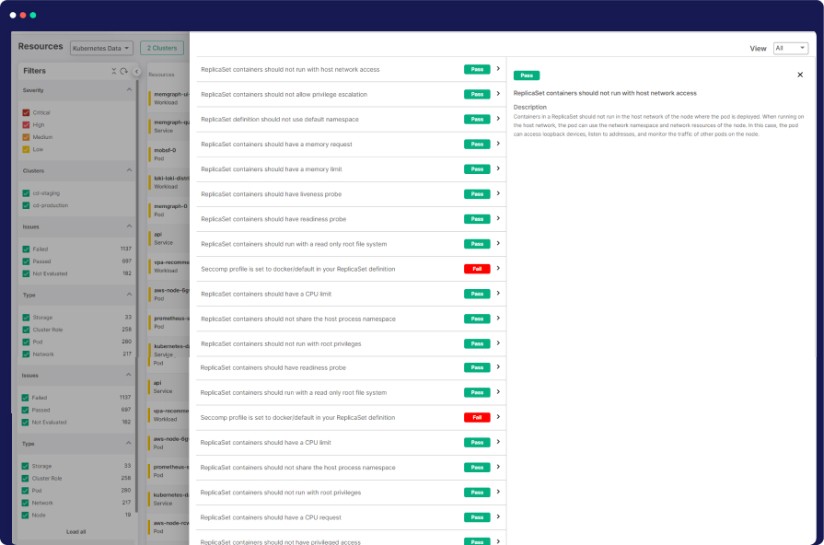
Kubernetes Misconfiguration Detection
Instantly identify and rectify Kubernetes misconfigurations with KSPM. Our tool provides real-time alerts, helping you proactively address potential security vulnerabilities before they become threats.
Custom Security Policies
Tailor your security strategy with ease by defining custom security policies. KSPM empowers you to set and enforce rules specific to your organization’s needs, ensuring comprehensive protection for your Kubernetes environments.
Our Comprehensive Approach to Kubernetes Security Posture Management (KSPM)
Comprehensive Cloud Asset Management Suite
Comprehensive Cloud Inventory
Effortlessly manages all resources - workloads, identities, data, network, and Kubernetes clusters - across AWS, Azure, and GCP.
Continuous Resource Discovery
Our platform continuously identifies and updates resources, ensuring real-time visibility.
Intuitive Visualization
Visualize your cloud assets in a meaningful, multi-dimensional context for better insights.
Smart Search and Query Tools
Easily investigate configurations, permissions, and relationships within your cloud environment.
Seamless Kubernetes Integration
Ingest Kubernetes inventory data via cloud and Kubernetes APIs and agentless scanning of nodes and containers for complete control.
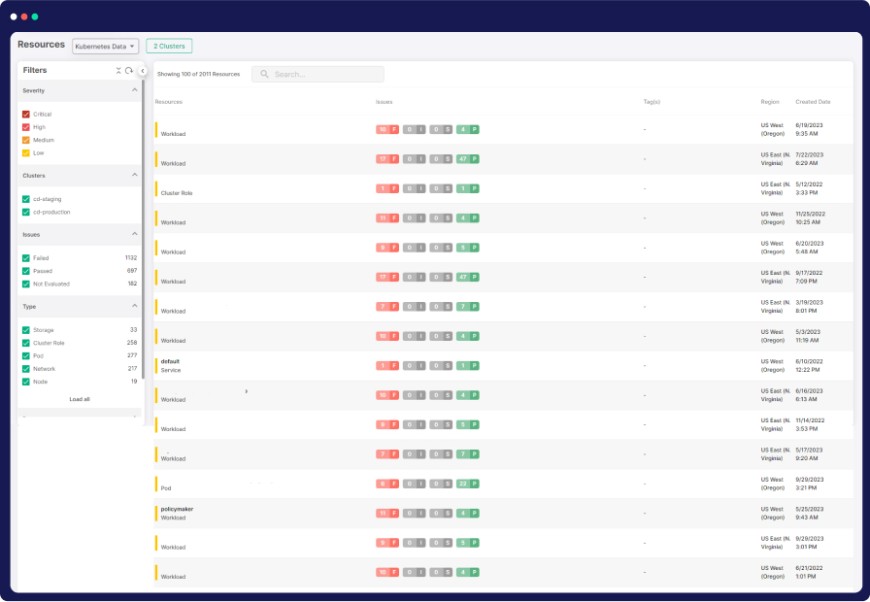
In-Depth Kubernetes Risk Assessment
Full-Stack Risk Assessment
Elevate Kubernetes security with holistic risk analysis, prioritizing vulnerabilities that may impact sensitive resources.
Compliance Enforcement
Ensure Kubernetes clusters adhere to CIS and hardening guide benchmarks for regulatory compliance.
Container Vulnerability Detection
Identify and address container vulnerabilities within Kubernetes clusters using integrated image scanning.
Misconfiguration Detection
Detect misconfigurations in Kubernetes manifests by leveraging integrated Infrastructure as Code scanning.
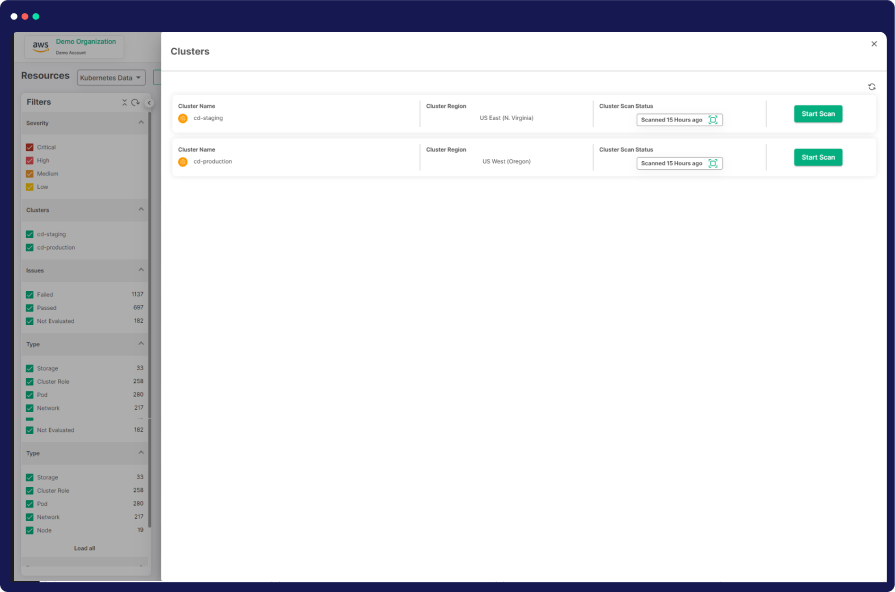
Agile Risk Mitigation Solutions
CloudDefense.AI offers thorough remediation solutions, swiftly addressing misconfigurations, policy breaches, and risky privileges. Streamline risk reduction with automated mitigation, optimized policies, and enhanced RBAC security for Kubernetes roles.
Automated Remediation
Effortlessly fix misconfigurations, policy violations, and risky privileges in your multi cloud setup, bolstering security and compliance.
Swift Mitigation
Accelerate risk reduction through user-friendly wizards, preconfigured policies, and quick fixes in Terraform and CloudFormation.
Kubernetes RBAC Security
Safeguard internal Kubernetes roles, cluster roles, and identities to fortify your containerized environments.
Real-Time Threat Analysis
Stay one step ahead with continuous monitoring and immediate response to evolving security threats.
Hassle-free Compliance and Reporting
CloudDefense.AI empowers your organization with automated compliance and security solutions. Simplify audits, identify violations, and generate comprehensive reports across a range of industry standards and custom frameworks.
Automated Compliance
Ensure alignment with diverse industry frameworks, including GDPR, CIS, NIST, and PCI-DSS, supplemented by custom checks.
Comprehensive Reporting
Easily produce in-depth reports for internal compliance, external audits, and daily security tasks, encompassing asset inventory, network configurations, and more.
Real-time Monitoring
Gain proactive insights into your environment's compliance status and security posture, allowing immediate action and risk mitigation.