Definition — What is Cloud Risk Management?
Cloud risk management is the strategic process of identifying, analyzing, and mitigating potential risks in cloud computing environments. With organizations increasingly adopting cloud services, managing risks such as data breaches, system outages, and compliance failures is critical to maintaining security and operational efficiency.
At its core, cloud risk management focuses on:
- Assessing cloud vulnerabilities to understand potential threats.
- Implementing proactive security measures like encryption and zero-trust policies.
- Regularly monitoring cloud infrastructure for anomalies and misconfigurations.
With businesses increasingly relying on cloud services, the stakes are high. If done right, cloud risk management reduces exposure to threats, protects sensitive data, and ensures uninterrupted operations.
The focus should always be on proactive measures—like continuous monitoring and encryption—to stay ahead of potential risks.
Why is it Important to Focus on Cloud Risk Management?
As organizations move critical workloads to the cloud, the risks grow in scale and complexity. Ignoring them could lead to devastating consequences, both operationally and financially.
Here’s why it demands your focus:
1. Cloud breaches are increasing at an alarming rate.
In 2023, 45% of data breaches were tied to cloud systems, with each incident costing businesses an average of $5.1 million. These aren’t small-scale threats—they directly hit operational integrity and trust.
2. Regulatory fines are climbing fast.
Non-compliance penalties exceeded $1.2 billion globally last year. Regulatory frameworks like GDPR and HIPAA have zero tolerance for errors, making cloud risk management crucial for businesses operating in regulated sectors.
3. Downtime is expensive—really expensive.
The average downtime costs $300,000 per hour for mid-to-large enterprises. Without strong risk mitigation strategies, cloud outages can cripple operations and erode customer confidence.
What Happens Without cloud Risk Management?
- Data breaches and leaks: Sensitive customer or internal data gets exposed, leading to legal and financial repercussions.
- Compliance failures: Missing a single regulation can result in fines, legal battles, and operational restrictions.
- Operational disruptions: Cloud outages aren’t rare—they happen. And when they do, businesses lose revenue and trust.
Why Act Now?
Cloud technology is advancing faster than most businesses can adapt. Waiting to act until after a breach or compliance failure isn’t a strategy—it’s negligence. Focusing on cloud risk management now means:
- Identifying risks early and addressing them head-on.
- Building resilience against future threats.
- Staying compliant and operational, no matter how the cloud landscape evolves.
What’s the Difference Between Cloud and On-Prem Risk Management?
The way risks are managed in cloud environments versus on-premises systems is fundamentally different because the infrastructure, control models, and vulnerabilities vary.
Cloud Risk Management focuses on shared responsibilities. The cloud provider handles the infrastructure, while businesses are responsible for securing data, configurations, and access. It demands constant monitoring, compliance with evolving regulations, and mitigating risks that stem from third-party dependencies.
On-Prem Risk Management is entirely within the organization’s control. Teams manage physical infrastructure, data storage, and network security. While this provides direct oversight, it also requires more resources and expertise.
Cloud Vs On-Prem Risk Management: Key Differences
| Aspect | Cloud Risk Management | On-Prem Risk Management |
| Control | Shared responsibility between provider and business. | Full control by the organization. |
| Infrastructure | Managed by cloud provider. | Requires in-house setup and maintenance. |
| Scalability | Highly scalable; on-demand resources. | Limited by physical hardware capacity. |
| Security Focus | Securing data, configurations, and API integrations. | Protecting physical servers, networks, and endpoints. |
| Compliance | Must comply with global and provider-specific regulations. | Requires internal compliance management. |
| Cost | Pay-as-you-go model. | High upfront costs for hardware and maintenance. |
| Downtime Risks | Dependent on cloud provider SLAs. | Downtime depends on in-house redundancy and resources. |
Cloud Risk Management Process
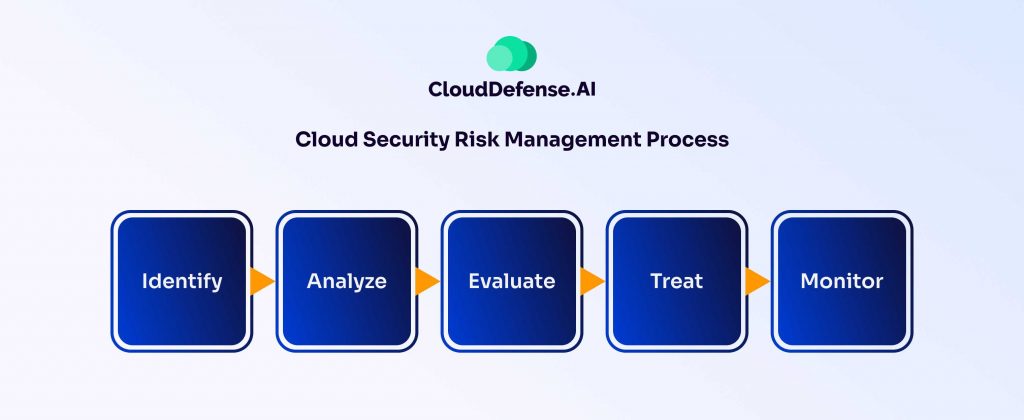
Managing cloud security risks isn’t a theoretical exercise. It’s about identifying vulnerabilities and taking concrete steps to fix them. Here’s how the process works:
Step 1. Identifying Assets
- The first step is simple: know what you’re protecting. Identify the cloud resources that are critical for your business—this includes data, applications, and infrastructure.
- Why it’s crucial: If you don’t know what’s important, you can’t protect it. Focus on assets that would impact business continuity if compromised.
Step 2. Identifying Potential Threats
- Next, understand what threats are out there. Look at the landscape of attacks and see how they map to your critical assets.
- How to approach it: Use threat modeling and track real-time data about vulnerabilities being exploited in the wild. It’s key to stay updated on active threats.
- Why it matters: Without a complete view of the threat landscape, it’s easy to miss something that could cause major damage.
Step 3. Evaluating Risks
- Now, not all risks are equal. Assess the severity of each threat.
- How to prioritize: Evaluate the potential impact on your business and the likelihood of each risk. Add context about how each threat would evolve and the resources needed to address it.
- Actionable insight: Focus on the highest-priority risks that could cause the most disruption.
Step 4. Treating Risks
- Fixing what’s broken comes last, but it’s critical. This means implementing fixes for vulnerabilities, updating IAM policies, and putting security controls in place.
- Patch vulnerabilities identified in step 2.
- Enforce strict IAM policies to ensure only authorized users have access to critical assets.
- Enhance security controls, tighten firewall rules, and set up continuous monitoring.
- Why this is essential: Remediation is what prevents a breach. Acting quickly and decisively keeps your cloud infrastructure secure.
Step 5: Monitoring and Reviewing
- Once risks are treated, continuous monitoring ensures that new vulnerabilities don’t slip through the cracks. Regularly review your cloud security posture to adapt to evolving threats.
- Why it’s necessary: Threats evolve, and security must too. Ongoing monitoring ensures that your cloud remains secure and compliant.
Cloud Risk Management Best Practices
To keep your cloud environment safe, you need to be smart and proactive. It’s about building a solid plan, staying ahead, and making sure you’re always one step ahead of threats. Here are the best practices that work:
1. Develop a Comprehensive Cloud Risk Management Strategy
The first thing you have to do is lay out a clear strategy. You can’t just guess what’s important. Identify every cloud resource you have. Know exactly what needs protection. Then, you perform threat modeling and vulnerability scanning to understand the full scope of what you’re dealing with.
- Prioritize risk: Once you have all the data, you need to rank the risks based on their potential impact. Don’t waste time on small risks that don’t matter. Focus on the big ones.
- Strengthen your systems: Build strong security systems. Implement strict IAM policies. Access should be controlled—only the right people should have access to the right resources.
You can’t afford to be reactive here. This is something you keep doing, again and again, to stay ahead of the game.
2. Use Configuration Management Tools
Misconfigurations are a major threat. If you’re managing things manually, you’re asking for trouble. Invest in configuration management tools. They take care of the details, ensuring your resources are correctly configured and aligned with industry standards. These tools help keep things running smoothly and save you from mistakes that could lead to vulnerabilities.
3. Set Up Your Compliance Frameworks
Compliance is a must, plain and simple. You need to track compliance with various regulatory standards and frameworks. Cloud security solutions that offer built-in compliance capabilities are key. You can use them to track and monitor your compliance status in real-time.
- Choose your frameworks: Pick the right compliance frameworks for your business. Whether it’s GDPR, HIPAA, or SOC 2, you need to ensure you’re always in compliance.
- Automate monitoring: These tools can handle a lot of the work for you. They track your status automatically, saving time and reducing human error.
Compliance isn’t optional anymore—it’s a critical part of your security posture.
4. Leverage Continuous Monitoring and Incident Response
You need to be monitoring your cloud environment 24/7. That’s just reality. A solid monitoring solution keeps an eye on everything. Get a Cloud-Native Application Protection Platform (CNAPP) with CSPM, CWPP, vulnerability management, and CIEM. These tools give you an overview of your entire cloud environment, tracking resources for potential threats.
Pair that with a Security Information and Event Management (SIEM) solution. This system will analyze log data and alert you to suspicious activities, so you can act fast.
5. Encrypt Data in Transit and at Rest
Data is valuable, and you can’t afford to leave it exposed. Encrypt everything—at rest and in transit. Do it from the beginning, not as an afterthought. This protects data during every step of the process.
In addition, always enforce the principle of least privilege. Only give people the minimum access they need to get their job done. It’s simple but effective. Protecting your data this way is non-negotiable. If you’re not doing it, you’re taking a huge risk.
6. Adopt a Zero-Trust Architecture
Zero trust means exactly that—no trust, anywhere. You can’t afford to trust any system, inside or outside your network. Every access request must be verified. Every time. This isn’t negotiable. Identity, location, and the sensitivity of what’s being accessed are all important factors.
If you put these practices in place, you’re not just reacting to threats—you’re proactively stopping them. Each of these steps is essential for building a solid, secure cloud environment. Keep monitoring, keep improving, and you’ll stay ahead of the risks.
Benefits of Cloud Risk Management
Cloud computing environments have a lot of potential if a proper cloud risk management plan is carried out. An efficient risk management plan can help an organization to materialize its goals faster and more productively. Check out some of the benefits associated with cloud risk management.
Predict Potential Risks:
Risk management frameworks help effectively identify any possible risks associated with your company. This helps to keep future risks at bay and mitigate them easily, as your system is already prepared.
Increase Business Growth:
A proper risk management plan always keeps your system prepared. When a threat hits your system, your cloud risk management framework helps to mitigate it on time and ensure that your system functions efficiently. With no disruptions of services, you can concentrate on boosting your business.
Documentation:
Documentation is an integral part of a risk management process. By having everything on paper, you can analyze your company’s processes. This helps you to improve a sector if needed.
Better Use Of Resources:
Having risk management plans also helps you to strategize how to use your resources. This saves time and money, which can be invested elsewhere for a more efficient infrastructure.
How CloudDefense.AI helps in Cloud Risk Management?
Detecting Misconfigurations
CloudDefense.AI constantly scans your cloud environment to identify misconfigurations and security issues. It’s about catching problems early, before they become big risks. By doing this, the tool helps maintain a secure and efficient cloud infrastructure. The earlier the detection, the quicker you can address and fix any issues.
Managing Access
CloudDefense.AI’s CIEM solution gives you tight control over who can access what in your cloud. Permissions are continuously adjusted to ensure only the right people have access to sensitive data. This reduces the risk of unauthorized access and makes your cloud infrastructure more secure.
Securing Your Data with DSPM
Data security is critical. CloudDefense.AI’s DSPM tool tracks where your data is, who can access it, and ensures it’s encrypted. It keeps an eye on your data, looking for vulnerabilities or signs of exposure. The goal is to make sure your data stays protected, minimizing any chance of unauthorized access.
Customized Compliance
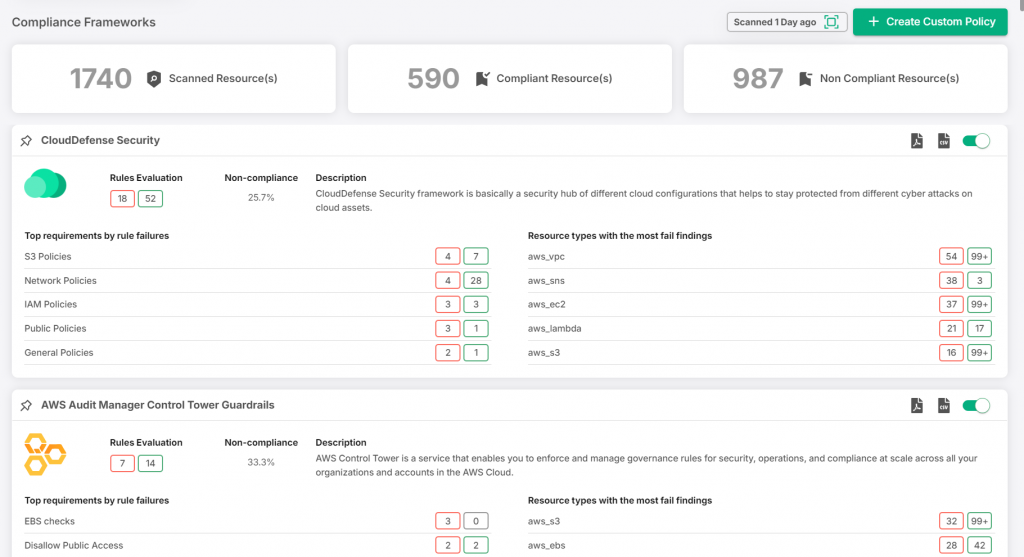
Compliance can be complex. CloudDefense.AI simplifies it by automating the tracking and monitoring of your compliance status. With customizable frameworks for industry standards like GDPR or HIPAA, the tool ensures your cloud setup is aligned with regulations—without needing to manually monitor it all the time.
See Your Cloud from a Hacker’s Perspective
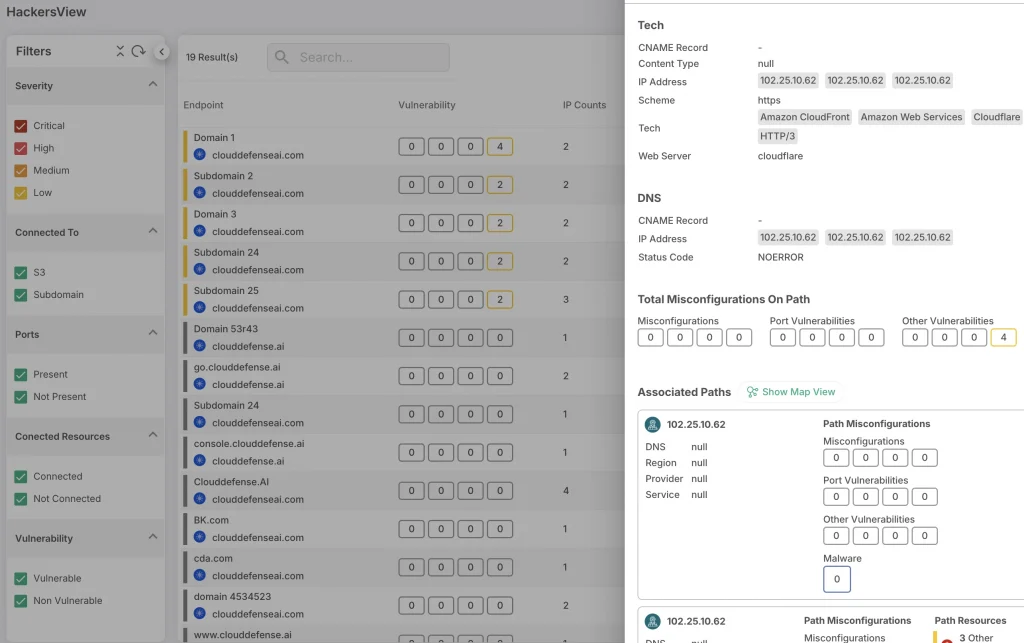
CloudDefense.AI’s Hacker’s View™ shows you your cloud from an attacker’s perspective. It simulates potential attacks to identify vulnerabilities that could be exploited. By doing this, it helps you see where your system could fail under attack and lets you fix those weak points.
Prioritizing and Addressing Risks
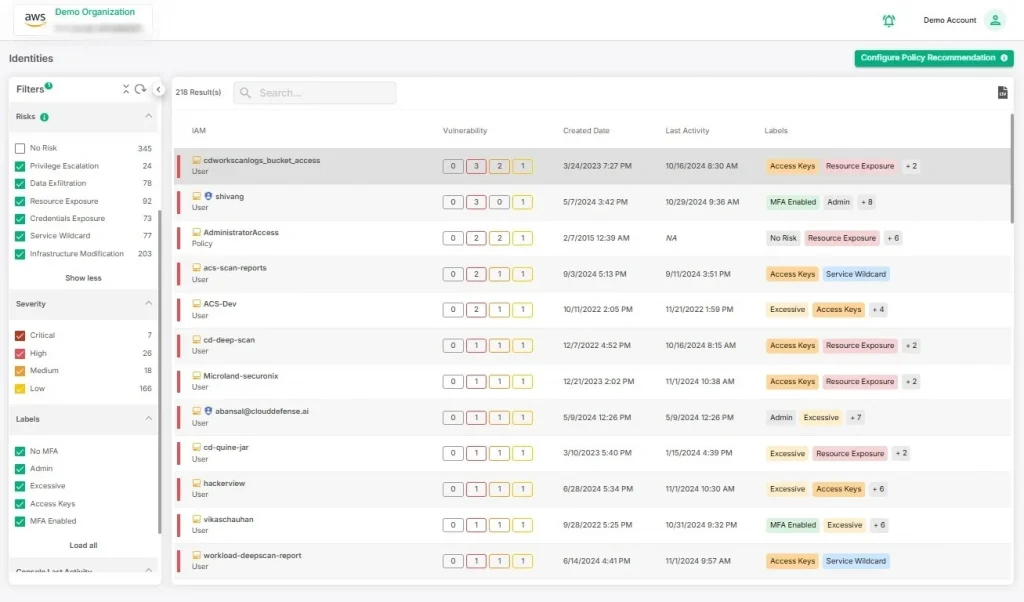
CloudDefense.AI helps you focus on the most critical risks first. It analyzes vulnerabilities and helps you prioritize based on potential impact. Instead of trying to tackle everything at once, it makes it clear where to direct resources for the best outcome.
FAQ
How do we mitigate the risk of cloud computing?
We can adopt a few different strategies to mitigate cloud computing risks effectively. This may include setting up robust user authentication methods, encryption of data being transferred or stored, regularly monitoring and assessing the security measures, using multi-factor authentication, and being compliant with security regulations.
Will cloud risk management be automated?
Security teams worldwide are moving to automate their cloud risk management plan to mitigate threats faster and in real-time. This also helps to constantly scan and monitor threats, giving you more time to patch your system. Many third-party vendors, such as CloudDefense.AI, are trusted to provide automated security solutions.
What are the common security challenges in cloud risk management?
Some common risks and challenges of cloud computing in risk management include account hijacking, data breaches, insider threats, insecure APIs, and improper access authentication measures.
Are there industry-specific best practices for cloud risk management?
Compliance standards such as PCI, ISO, HIPAA, and GDPR help you understand the industry-specific best practices you need to follow to create your cloud risk management policy.
Conclusion
Cloud Computing is no longer a trend but a reality as more companies adopt its powerful capabilities. However, a proper cloud risk management plan must be created to address any security challenges associated with this powerful technology. Make sure that your system has that survival instinct to constantly adapt and evolve according to the threats to its system. Get the required feedback from all the parties involved to craft the best possible risk management plan for your organization.







