The U.S. Securities and Exchange Commission, or the SEC, has set strict cybersecurity disclosure rules for public companies, effective December 18, 2023, in response to the escalating cyber threats.
These regulations mandate the disclosure of material cybersecurity incidents and require a positive stance on cybersecurity risk management. With an alarming 83% of companies experiencing multiple data breaches last year, averaging $9.44 million in costs, these regulations hold a lot of significance for all SEC registrants.
The four-day material breach reporting requirement is a major highlight in the regulations, requiring your company to conduct solid SEC materiality assessments within incident response plans. A quick read of this article will provide an overview of the new SEC cybersecurity rules and what you need to know about the materiality assessment and the disclosure of cyber incidents.
Overview of the New SEC Cybersecurity Rules
On the 26th of July 2023, the SEC made a new rule that requires companies to disclose more information on their cybersecurity infrastructure. This comes from worries about investors not getting enough information due to technological changes. The rule focuses on risks from digital tech, AI, hybrid work, and crypto assets, requiring consistent and timely information.
Unlike previous guidance, the rule imposes strict requirements on
- Disclosing all material cybersecurity incidents. It demanded their disclosure within four business days on Form 8-K, for domestic registrants. For foreign private issuers (FPIs), the disclosure needs to be made on Form 6-K.
- Annual disclosures on Form 10-K involving cybersecurity risk management, management’s role, and board oversight for domestic registrants. For FPIs, the annual disclosures need to be made on Form 20-F.
The materiality standard here follows federal securities laws, focusing on how likely information is important. Companies must objectively assess qualitative and quantitative factors for deciding what’s material, encouraging informed decision-making processes.
The SEC’s new cybersecurity rule requires companies to establish a defined process for assessing cyber incidents involving IT/security, finance, and legal departments. This ensures timely, well-informed decisions and documentation of judgments and rationales. The goal is to make disclosures more consistent for public companies reporting under the Securities Exchange Act of 1934, including foreign private issuers.
Who is affected by the new rules?
The rules impact both domestic registrants and Foreign Private Issuers (FPIs) bound by the reporting obligations of the Exchange Act. Moreover, Business Development Companies (BDCs) falling under the definition in section 2(a)(48) of the Investment Company Act of 1940 are also subject to these rules.
What is materiality assessment according to the SEC?
Materiality assessment as defined by the SEC involves evaluating the significance or importance of a cybersecurity incident or risk in the context of potential impact on an organization. It considers quantitative and qualitative factors in determining if the incident could affect a reasonable investor’s decision or change the total mix of available information, thus deeming them as material.
This assessment is important for complying with regulatory requirements, such as the SEC’s rules, which mandate disclosing material cybersecurity incidents. Analyzing cyber incidents requires you to have an objective and maintain a thoughtful process, often involving input from other stakeholders who are working together.
Preparing for a Materiality Assessment of Cyber Incidents
To meet the requirements set forth by the SEC, a strong materiality assessment framework is essential for organizations to overcome the complexities of various cyber incidents. You need to consider a few things while creating a materiality assessment framework and we have outlined them below for you.
Setting up a Materiality Assessment Policy
Create a set of policies that provide clear principles and procedures to calculate the importance of cyber incidents, establish responsiveness, and manage expectations. Its goal should be to ensure a consistent, effective, and SEC regulations-compliant response from your company’s end. The policy focuses on transparency, prioritizing the protection of shareholder interests.
Understanding the Role of Your Team Members
The framework should assign distinct roles and responsibilities to the materiality assessment team, executive management, and your board of directors in the materiality assessment process. Each group holds specific duties in assessment, decision-making, and reporting, uplifting accountability and efficiency throughout the process.
Materiality Assessment and Incident Disclosure
When judging materiality, you need to identify the type of incidents and relevant qualitative factors for investors. Gather necessary information by having clear objectives, and considering related occurrences. Define a process in your company to collect disclosure information and file accordingly, considering external SEC legal counsel consultation.
Have clear steps for escalating cyber incidents within the company’s ecosystem and create an organized process for drafting and reviewing to meet the four-day reporting timeline when materiality is confirmed.
Setting up a Materiality Assessment Team
To handle potential cyber incidents effectively, form a Materiality Assessment Team for your company. Include members from cybersecurity, legal, compliance, finance, and communications.
You will need to assign roles like a cybersecurity lead for security evaluation, a legal advisor for legal guidance, a compliance officer for regulations, a finance representative for financial assessment, and a communications lead for information management.
Lastly, ensure that you have access to external counsel and law enforcement agencies. This ensures a swift and comprehensive analysis of material incidents, strengthening your company’s materiality assessment process.
Understanding Whether a Cyber Incident Disclosure is Required
To carry out a materiality assessment process in your company carefully, you would need to understand the many intricacies that are involved in the process. Understanding what documents need to be collected, the factors that you need to consider, how to conduct the assessment, and going forward with a comprehensive assessment report are the primary loopholes in the materiality assessment workflow.
Collecting Documents on the Cyber Incident
You will need to ensure your company is systematically documenting and preserving evidence related to cyber incidents. This includes logs, digital forensics, communications, and decision-making records for materiality assessment. It is important to ensure that any documents that you create are tamper-proof so that their credibility is intact when presented to internal and external auditors.
Assessing the Quantitative and Qualitative Effects of Cyber Incidents on the Company
In cyber incident materiality assessment, you must assess the quantitative and qualitative factors involved. Quantitative factors like financial losses and legal liabilities are measured alongside qualitative factors such as reputational damage and partnership impact. This analysis ensures a good understanding of the incident’s importance, guiding effective decision-making for organizations when dealing with them.
Conducting Materiality Assessment
It is your company’s materiality assessment team that will conduct a comprehensive analysis of the many cyber incidents taking place in your organization. Make sure you have a structured approach to determining the materiality of incidents. The approach must include, risk-based assessment, and loss-based assessment, which will help you to quantify immediate and projected losses.
Generating a Materiality Assessment Report and Getting Legal Advice
Next up, the materiality assessment team generates a comprehensive report summarizing incident details, assessment methodology, findings, and recommended actions. Following this, the legal advisor of the company collaborates with external counsel to discuss incident disclosure based on the materiality assessment, ensuring that the process maintains legal privilege and complies with regulatory requirements.
Is an incident disclosure required?
For your company’s incident response, the executive team, with inputs from the Materiality Assessment Team and external counsel, decides whether to withhold or disclose information based on the materiality assessment report by keeping SEC material disclosure requirements in mind. If withholding, the decision is documented with the reason and communicated to the Board.
If disclosing, legal counsel drafts the 8-K disclosure form which is submitted to the SEC. Communication strategies for external reporting, investor, customer, or partner communications are addressed accordingly by the team. Ongoing incident response and mitigation may require further disclosure following a similar assessment and decision-making process.
Detecting and Reporting Cyber Incidents
Implementing advanced detection methods can help protect your company against cyber incidents. Deploy cutting-edge cybersecurity tools like intrusion detection systems, network monitoring, and anomaly detection algorithms. Make sure your company prioritizes employee vigilance and encourages the reporting of suspicious activities through accessible channels, including dedicated hotlines, email addresses, and secure web forms.
When potential incidents arise, conduct a swift preliminary assessment to categorize them by severity, urgency, and potential materiality. Establish clear criteria to flag incidents for materiality assessment, considering factors such as data breach extent, potential financial impact, legal implications, and reputational damage.
Criteria for Materiality Assessment of a Cyber Incident
Criteria for materiality assessment during a cyber incident involve analyzing various factors to determine the impact of the event. By systematically considering the criteria that we have outlined below, your materiality assessment team can provide a thorough understanding of the cyber incident’s significance, guiding appropriate actions for response and disclosure.
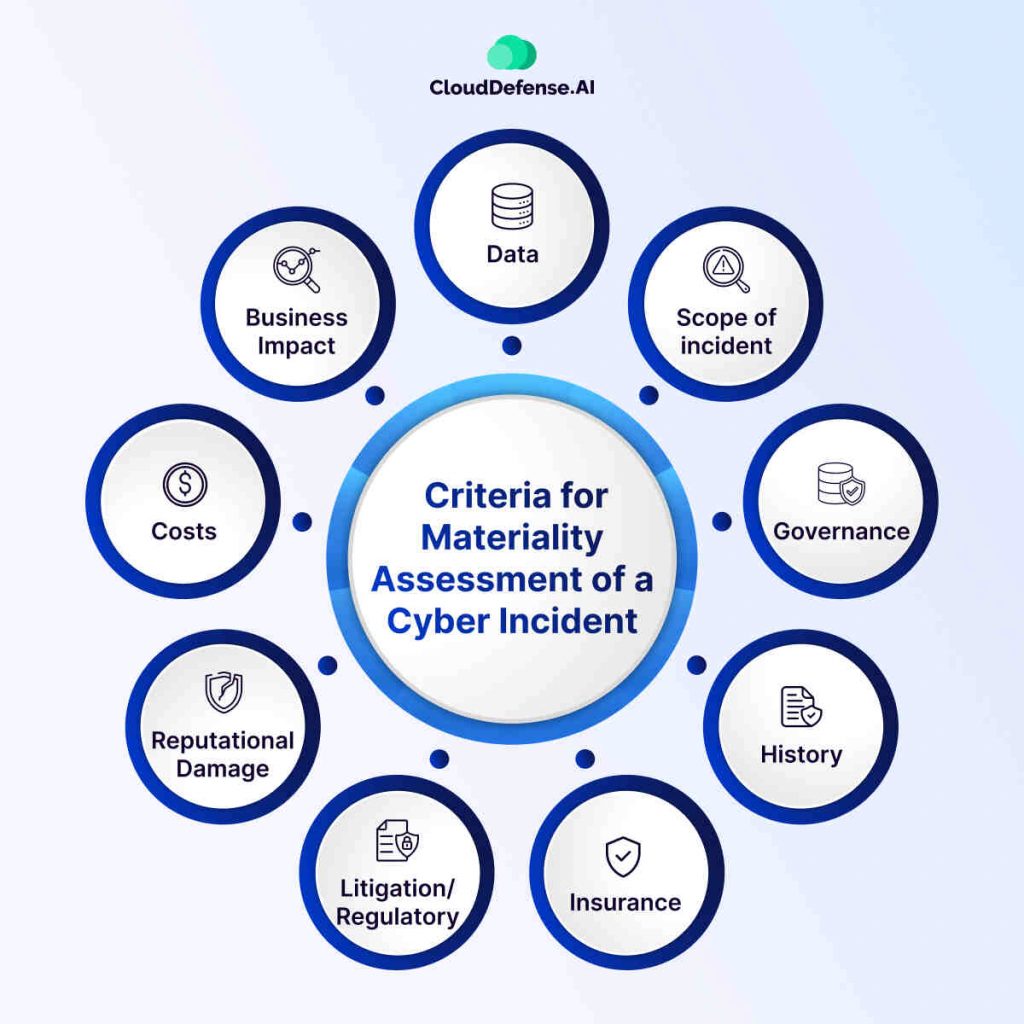
Sensitivity of the Compromised Data
Find out the type and sensitivity of your company’s data that was compromised, whether it is personally identifiable information, financial data, or intellectual property.
Scope and Scale of the Cyber Incident
Calculate the extent of the incident, including the number of affected records, systems, or individuals, to assess the overall impact on your company from the incident. Furthermore, you should consider the direct and indirect financial consequences on the company, including immediate costs, potential regulatory fines, and long-term financial damages.
Operational Disruption Due to the Cyber Incident
Evaluate how the incident disrupts your normal business operations and impacts your company’s productivity, service delivery, or customer experience. Also, investigate whether the incident aligns with or sways away from your company’s business strategy, goals, and objectives.
Reputational Damage to the Company
Consider the potential harm to the company’s reputation, trust, and brand value, both in the short term and the long term.
Calculate the Impact on Stakeholders and Notification Requirements per SEC
Determine the impact on your customers, partners, and other stakeholders, including any potential breach of trust or loss of confidence. You should also consider whether the incident triggers mandatory notification requirements set by the SEC to affected individuals or other stakeholders.
Remediation Costs
Lastly, you must keep in consideration all the costs associated with remediation efforts, including implementing security measures, addressing vulnerabilities, and restoring your company’s affected systems.
Navigating the New SEC Cybersecurity Rules: An Action Guide for CISOs & Security Teams
Now that we have covered the essential aspects of the new SEC cybersecurity rules and materiality assessments, let’s delve into specific actions that IT and security leaders, particularly CISOs, need to take to ensure compliance and effective incident response.
The recently implemented SEC cybersecurity rules raise a crucial question for IT and security professionals: am I doing enough to comply? While understanding the overall impact and requirements is essential, many feel uncertain about their specific responsibilities and actions.
This guide dives into three key areas where IT and security teams can take immediate action to ensure compliance and effectively navigate the new regulations:
1. Align Your Risk Posture with Disclosure Capabilities:
Managing cyber risks isn’t enough under the new rules. You need to confidently articulate how you manage them to the public in financial statements. Conduct a thorough assessment of your cybersecurity program, asking:
- Can it effectively deliver on its mission in line with the SEC’s expectations?
- Do we understand our company’s cyber risk posture comprehensively?
- Are we confident in disclosing our management program accurately?
If any answer is “no” or “unsure,” prioritize improvements. Remember, consistent and comparable disclosures will soon be available to investors, so benchmarking your practices against peers is crucial.
2. Master the Materiality Framework and Data Collection:
Materiality determinations go beyond the sole responsibility of any one individual. It’s a collaborative effort requiring seamless communication and coordination across departments. Here’s how to be prepared:
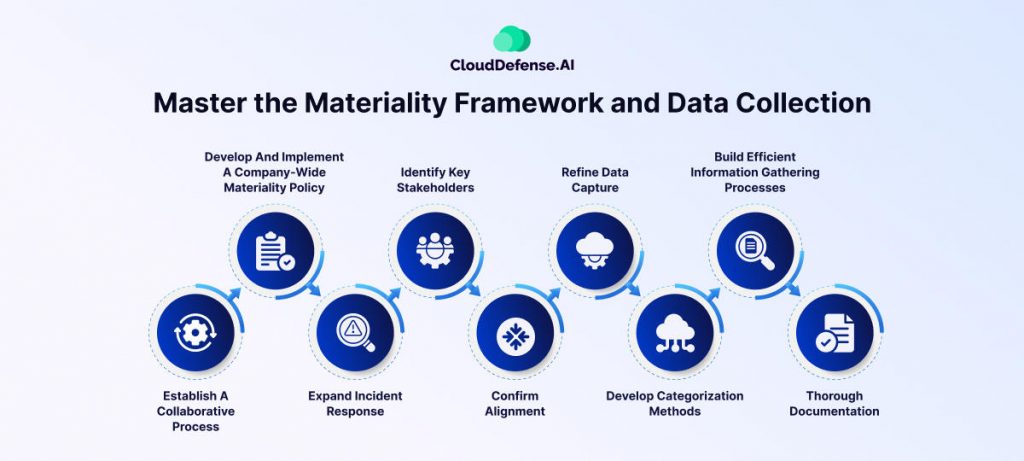
- Establish a collaborative process: Identify individuals involved in materiality determinations and build a clear workflow for communication.
- Develop and implement a company-wide materiality policy: This sets consistent criteria for incident escalation, reporting, and disclosure. This policy should define quantitative and qualitative factors used to assess impact on investors, including financial losses, reputational damage, legal implications, and operational disruption.
- Expand incident response: Track incident attributes and metadata crucial for establishing materiality. Develop a repeatable method for reporting this data routinely.
- Identify key stakeholders: Collaborate with the CFO, general counsel, and others to define a “materiality framework” for consistent incident evaluations.
- Confirm alignment: Ensure everyone involved understands the framework, associated metadata, and organizational thresholds for deeming incidents material (individually or combined).
- Refine data capture: Streamline the process of collecting and maintaining incident metadata within your existing incident response workflow. Create a plan for continuous improvement in metadata tracking.
- Develop categorization methods: Categorize incidents by attributes to assess materiality across multiple events. Identify related occurrences (e.g., same threat actor or shared vulnerability) and escalate them together if necessary.
- Build efficient information gathering processes: Train incident responders on additional requirements and metadata collection procedures.
- Thorough Documentation: With each cyber incident, prepare to document contemporaneously. Use tools and templates that facilitate documenting the materiality assessment. This creates a defensible position if challenged.
3. Strengthen Collaboration with Internal Partners:
Effective communication and collaboration are vital under the new rules. Here are key relationships to nurture:
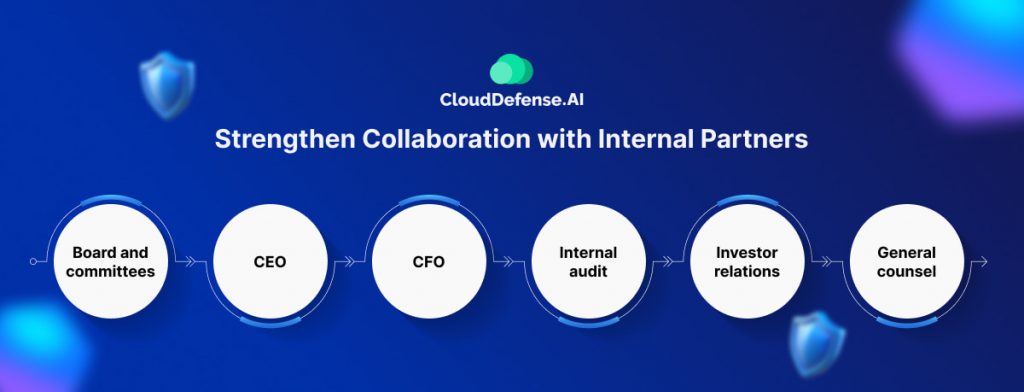
- Board and committees: Present cyber threats and incident data clearly and concisely. They need actionable insights to make informed decisions.
- CEO: Assure them that information and systems are secure and comply with SEC regulations. Provide concise data and confirm program governance adequacy.
- CFO: Partner to produce investor-grade information, especially for material incidents. Help them gain confidence in your program’s ability to assess materiality swiftly.
- Internal audit: Collaborate to understand and assess cyber risks, test mitigation controls, and ensure the company can respond effectively to threats and generate disclosures.
- Investor relations: Work with them to anticipate the market impact of disclosing material incidents and ensure investors receive necessary information.
- General counsel: Partner to comply with legal obligations and minimize liability.
Addressing these areas, CISOs and IT security leaders can confidently navigate the new SEC cybersecurity rules, ensuring compliance, transparency, and effective risk management for their organizations. Remember, this is an ongoing process, so continuous improvement and collaboration are key to long-term success.
FAQ
What is materiality in the SEC cybersecurity rules?
The SEC’s cybersecurity rules define a material incident in the context of cybersecurity as something that a reasonable investor would likely consider important when deciding on investments.
How does the SEC determine materiality?
The standard for assessing materiality by the SEC is on the belief that there is a strong chance that an average investor or other stakeholders would have deemed the information important when deciding to invest or vote.
Why SEC cybersecurity rule is important?
The latest SEC cybersecurity rule enhances risk awareness and mitigation. Firms must tackle third-party risks to comply, understanding the “material” impact of cyber incidents. This prompts boards and management to strengthen supply chain resilience through effective risk management.
Conclusion
The SEC’s proposed rules came through the demands of stakeholders, who complained about the lack of information sharing from the company’s end. With the new SEC rule in place, companies must strengthen their security infrastructure and ensure swift disclosure of material incidents.
Establishing a well-planned materiality assessment framework is essential to adhere to the important SEC cybersecurity rules. This will require determination from your company and a well-structured team. It is high time for companies to align their operations with these regulations to protect shareholder interests and maintain their customer’s trust in them.







