The internet thrives on efficiency, constantly seeking ways to deliver content faster along with smooth browsing experiences. One such format, WebP, offered advantages over traditional options like JPEG and PNG.
However, a recent vulnerability discovered in the software library responsible for processing WebP images, LibWebP, sent shockwaves through the cybersecurity landscape. This critical vulnerability, actively exploited in the wild, posed a significant threat to users and organizations alike.
In this particular article we discuss the technical aspects of the LibWebP vulnerability, explores its potential consequences, and outlines the steps taken to address this security breach.
Understanding LibWebP and its Importance
Before diving into the specifics of the vulnerability, it’s crucial to understand the role of LibWebP and the significance of the WebP format it supports.
WebP: A Lighter Way to Deliver Images
Developed by Google, WebP is an image format designed to offer superior compression compared to traditional formats like JPEG and PNG. This translates to smaller file sizes without sacrificing image quality, leading to several benefits:
- Faster Loading Times: Smaller files take less time to download, resulting in quicker page load times and a smoother browsing experience.
- Reduced Bandwidth Consumption: Smaller file sizes translate to less data usage, which is beneficial for users with limited data plans and website owners concerned about bandwidth costs.
- Improved Search Engine Optimization (SEO): Faster loading times can positively influence search engine rankings, impacting website visibility.
LibWebP: The Engine Behind WebP Adoption
LibWebP is a crucial component of the WebP ecosystem. It’s a software library that provides the tools and functionalities for:
- Encoding: Converting images from other formats (like JPEG or PNG) to WebP.
- Decoding: Processing and displaying WebP images on web browsers and other applications.
- Animation: Enabling the creation and playback of animations using the WebP format.
The widespread adoption of WebP by major browsers and image editing software is largely due to the capabilities and functionalities offered by LibWebP. By understanding its role, we can appreciate the potential impact of vulnerabilities within this library.
LibWebP Vulnerability: What it is and Potential Security Risks
In September 2023, a seemingly harmless image format, WebP, harbored a hidden danger. Researchers at the University of Toronto’s Citizen Lab and Apple’s Security Engineering and Architecture (SEAR) team discovered a critical vulnerability, later designated CVE-2023-4863, within the software library responsible for processing WebP images, LibWebP.
This vulnerability named “heap buffer overflow” stemmed from improper memory management during the decoding process. LibWebP allocates a specific amount of memory in the heap (a dynamic memory pool) to store incoming image data. The vulnerability arose when a malicious actor crafted a WebP image containing crafted data exceeding the allocated memory buffer.
Here’s a breakdown of the vulnerability and its potential consequences:
This overflow resulted in the image data spilling over into adjacent memory locations on the heap. These adjacent locations could contain critical program instructions or data structures. Overwriting these locations could lead to two main consequences:
- Code Execution: If the overflow data contained malicious code (e.g., shellcode), it could overwrite legitimate code stored in adjacent memory. When the program execution flow reached the overwritten section, the malicious code would be executed instead, potentially granting the attacker unauthorized access to the system.
- Denial-of-Service (DoS): Even without malicious code, the overflow could disrupt the program’s functionality. Overwriting critical data structures or program instructions could lead to program crashes or unexpected behavior, effectively rendering the application or system inoperable.
Potential Security Risks:
The critical nature of the LibWebP vulnerability stemmed from its exploitability and widespread usage:
- Zero-Click Exploit: The vulnerability was particularly dangerous because it was exploitable without any user interaction. A specially crafted WebP image, embedded in a website, email, or other online content, could trigger the exploit when processed by a vulnerable system. This made it a zero-click exploit, significantly increasing the attack surface and potential impact.
- Widespread Use: LibWebP is integrated into various software, including web browsers, image editing tools, and content management systems. This extensive reach meant a large number of systems and users were potentially exposed.
It results in some of the potential attacks like:
- Malicious Adverts: Attackers could embed malicious WebP images in online advertisements, targeting users browsing vulnerable websites.
- Phishing Emails: Malicious actors could include a crafted WebP image in a phishing email, compromising the recipient’s system upon opening the email.
- Watering Hole Attacks: Attackers could compromise websites frequented by specific targets and inject malicious WebP images to exploit their systems.
These are just a few examples, and the potential attack vectors were vast due to the exploitability and reach of the vulnerability.
Does it have any impact on Data Security?
The LibWebP vulnerability posed a significant threat to data security due to the potential for remote code execution (RCE). If successfully exploited, an attacker could gain unauthorized access to a user’s device or server. This access could be used to steal sensitive data like login credentials, financial information, or personal documents. Attackers could also install malware that remains hidden, allowing for long-term data exfiltration or manipulation.
The vulnerability’s widespread presence in browsers and image-processing software meant a successful attack could compromise a user’s data across various platforms. For instance, a compromised system could be used to steal login credentials used for online banking or email accounts. Malicious code could also be designed to scrape sensitive data displayed on a user’s screen, such as credit card details entered during an online purchase.
In essence, the LibWebP vulnerability created a backdoor for attackers to bypass security measures and access a user’s data directly. The potential consequences ranged from identity theft and financial loss to compromised business operations and data breaches.
How to Identify Affected Assets?
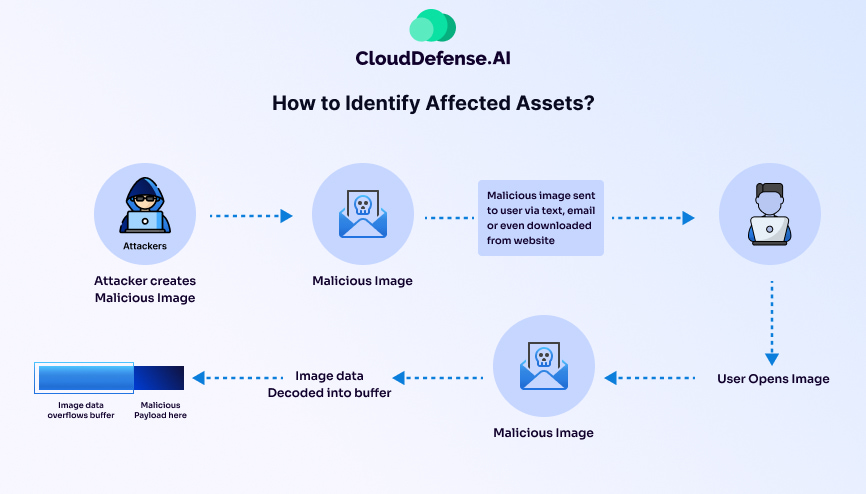
While the LibWebP vulnerability posed a significant threat, the good news is that there are ways to identify and mitigate the risks associated with it.
Here’s how CloudDefense’s Cloud Native Application Protection Platform (CNAPP) framework can be leveraged to find assets vulnerable to the LibWebP flaw:
- Workload Discovery and Inventory: CNAPP utilizes various techniques to discover all workloads within an organization’s cloud environment. This includes identifying virtual machines, containers, serverless functions, and other cloud-based resources.
- Vulnerability Scanning: CNAPP integrates with vulnerability scanning tools to scan discovered workloads for known security vulnerabilities. These scanners can leverage pre-defined vulnerability databases or threat feeds to identify potential security weaknesses, including the LibWebP vulnerability (CVE-2023-4863).
- Dependency Mapping: CNAPP can map dependencies between different components within a workload. This includes identifying libraries and software versions used by each workload. This dependency mapping is crucial for identifying workloads that rely on vulnerable versions of LibWebP.
Remediation:
Once CNAPP identifies affected workloads, organizations can leverage the platform’s remediation capabilities or integrate it with other security tools to:
- Patch Management: Automate the patching process to update vulnerable versions of LibWebP to the latest secure version.
- Isolation or Disabling: Isolate or disable affected workloads if patching is not immediately feasible to mitigate the risk of exploitation.
- Prioritization: CNAPP can help prioritize remediation efforts based on the criticality of the affected workloads and the potential risk associated with the vulnerability.
Proactive Protection: Addressing Emerging Vulnerabilities and Safeguarding Your Systems
While the LibWebP vulnerability (CVE-2023-4863) hasn’t yet become widespread, proactive measures are essential to safeguard yourself. The most immediate action is to update your web browsers to the latest version, as these updates often contain patches specifically addressing the vulnerability.
However, securing your system requires a more comprehensive approach. Beyond web browsers, the true challenge lies in identifying all potential avenues of exposure within your applications.
Here’s where a comprehensive vulnerability management solution like CloudDefense.AI comes in. AI can be invaluable. CloudDefense. AI offers an exclusive vulnerability management solution that goes beyond basic scanning. It leverages advanced threat intelligence and machine learning to proactively identify and prioritize vulnerabilities like the LibWebP flaw across your entire IT infrastructure, including web browsers, applications, and operating systems.
Are you curious about how it works? Book a free demo with us and see how our comprehensive vulnerability management solution can help you stay ahead of evolving threats and safeguard your data.







