What Is Spyware?
Spyware is a type of malicious software installed on a device without the user’s knowledge or consent.
It covertly collects sensitive information, such as browsing habits, financial details, and login credentials, and transmits it to third parties like advertisers, data firms, or cybercriminals.
Acting as a digital spy, spyware poses a serious threat to privacy and security, enabling unauthorized access, identity theft, and financial fraud. Its stealthy nature makes detection difficult, increasing the risk of exploitation and data breaches.
What Does Spyware Do?
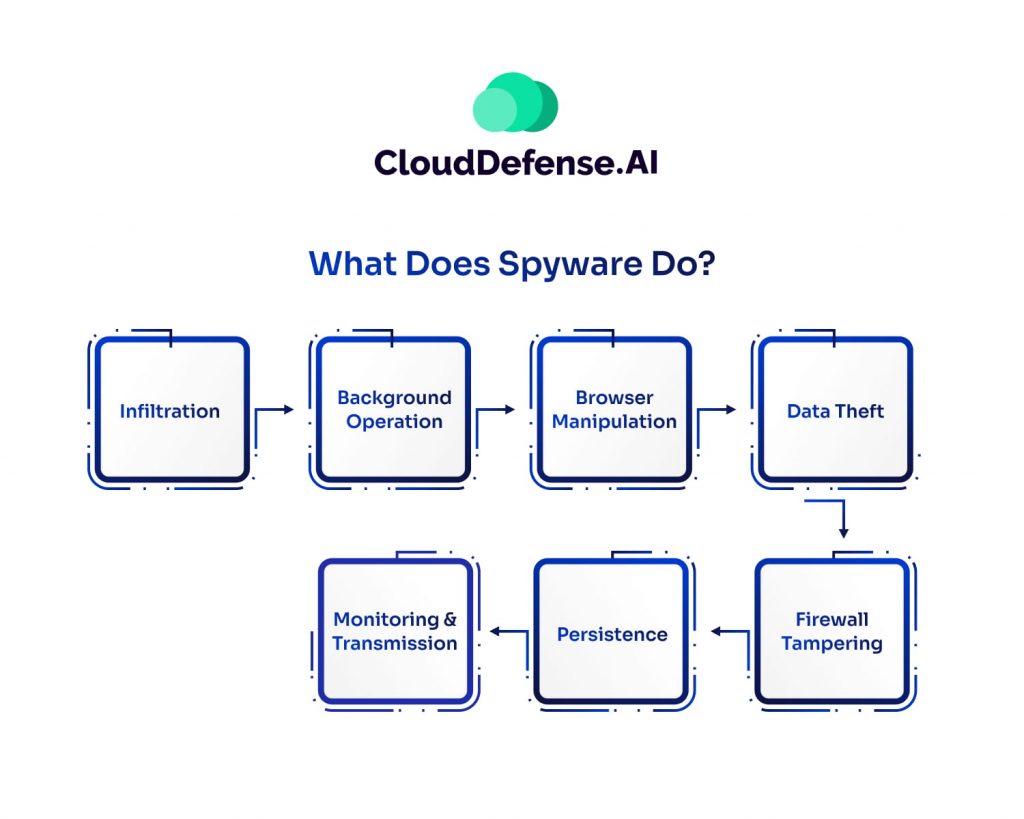
Spyware is a silent predator, infiltrating devices and operating in the background to steal sensitive information and manipulate system settings. It poses a serious threat to privacy, security, and device performance. Here’s a breakdown of how spyware operates and why it’s so dangerous:
Infiltration: Sneaking into Your Device
Spyware gains access to your system through deceptive methods like:
- Bundled software installations
- Malicious email attachments
- Fake updates and downloads
- Infected websites and ads
Most users don’t even realize when spyware has infiltrated their device—it installs itself silently, often without requiring any action from the victim.
Running in the Background: Draining Resources
Once installed, spyware operates discreetly in the background, consuming system memory and processor power. It can cause:
- Slower device performance
- Unresponsive web browsers
- Endless pop-ups and intrusive ads
Over time, these issues degrade user experience and make everyday tasks frustratingly slow.
Browser Manipulation: Controlling Your Online Experience
Spyware can take control of your browser by:
- Changing your homepage
- Redirecting searches to malicious sites
- Injecting unwanted ads into webpages
- Altering search results to promote unsafe websites
This manipulation can mislead users into entering sensitive data on fraudulent sites, putting their personal information at risk.
Data Theft: Stealing Sensitive Information
One of the most dangerous functions of spyware is its ability to steal personal data, including:
- Browsing history and online habits
- Login credentials (usernames and passwords)
- Credit card and banking information
- Email addresses and private messages
It often achieves this through keyloggers, screen captures, and form grabbers, exposing victims to identity theft and financial fraud.
Firewall Tampering: Weakening Your Security
Advanced spyware can manipulate firewall settings and security software, making it easier for additional malware to infect the device. This weakens the system’s defenses, leaving users vulnerable to even more cyber threats.
Persistence: Resisting Removal
Spyware is notoriously difficult to remove because it:
- Alters system settings to prevent detection
- Embeds itself deep in the operating system
- Modifies the Windows registry
- Blocks antivirus programs from running
Even if a user attempts to uninstall it, spyware often reinstalls itself or leaves behind traces that allow it to re-emerge.
Monitoring & Data Transmission: Exploiting Stolen Information
Spyware continuously tracks user activity, capturing everything from login credentials to banking details. This stolen data is then:
- Sold on the dark web
- Used for financial fraud and identity theft
- Exploited for targeted phishing attacks
Spyware poses more than just a nuisance; it directly threatens your privacy, security, and financial stability. The ramifications can be serious, ranging from identity theft to compromised banking information.
Through a systematic process of infiltration, monitoring, and transmission, spyware poses a significant threat to user privacy and security. It can lead to identity theft, financial fraud, and compromised system integrity, highlighting the importance of strong cybersecurity measures.
Types of Spyware
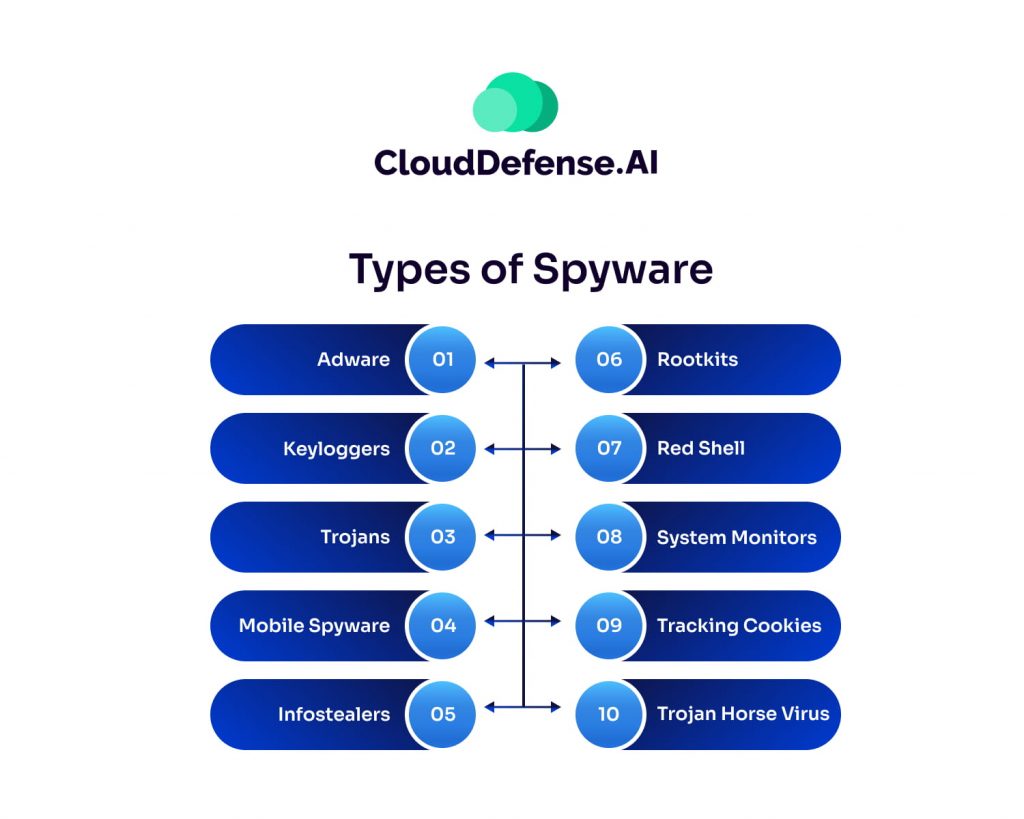
Spyware comes in various forms, each designed to monitor, collect, and exploit user data secretly. Some types focus on tracking online activity, while others steal sensitive information like passwords and financial details. Understanding the different types of spyware can help you recognize potential threats and take preventive measures. Below are the most common types of spyware and how they operate.
| Type of Spyware | Description |
| Adware | Bundled with free software, tracks user activity, sells data to advertisers, or displays intrusive ads. |
| Keyloggers | Records keystrokes to capture sensitive data like passwords and credit card details. |
| Trojans | Disguised as legitimate software to trick users into installing malicious programs that steal or delete data. |
| Mobile Spyware | Transmitted via text messages, can access a device’s camera, microphone, and location without user interaction. |
| Infostealers | Scans devices for specific data, including instant messaging conversations, to be sold or exploited. |
| Rootkits | Exploit system vulnerabilities for deep access, often remaining undetected and enabling further attacks. |
| Red Shell | Tracks online activity by installing alongside PC games, primarily for marketing purposes. |
| System Monitors | Captures user activity, including emails, websites visited, and keystrokes, for malicious purposes. |
| Tracking Cookies | Used by websites to monitor and record user browsing habits. |
| Trojan Horse Virus | Delivers spyware programs to devices, facilitating data theft and other malicious activities. |
How Spyware Infects Your Systems?
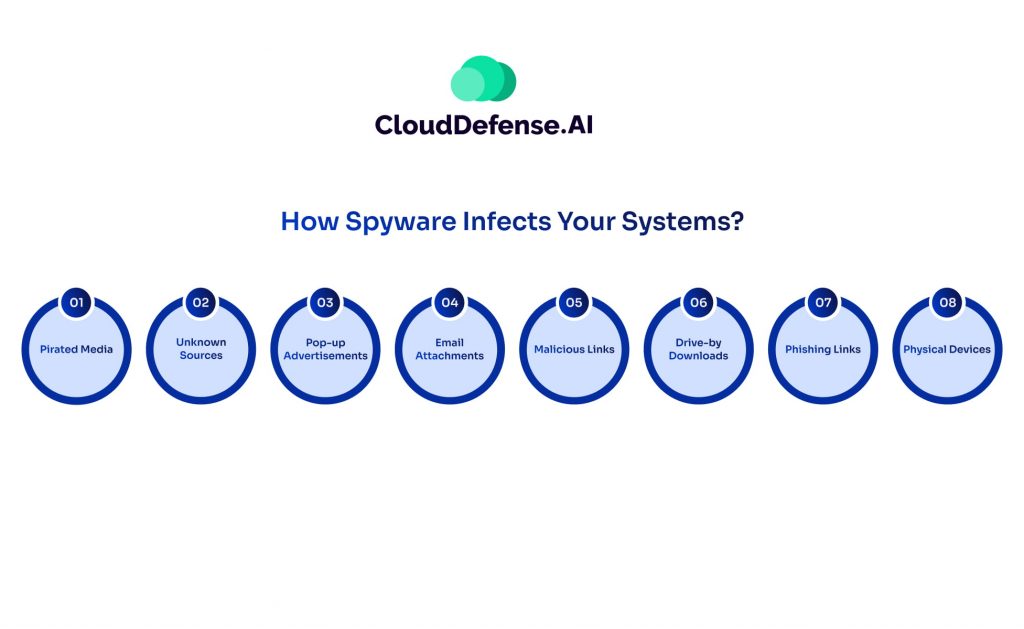
Spyware can infiltrate your devices through various deceptive tactics, often without your knowledge. Whether you use a personal computer, Mac, iOS, or Android device, spyware can find its way in through multiple infection methods. Understanding these entry points is crucial for preventing an attack.
Pirated Media: Hidden Threats in Illegal Downloads
Downloading pirated content—such as movies, games, music, and software—poses a major risk. Cybercriminals often bundle spyware within these files, exploiting users who unknowingly install malicious software along with the desired content.
Untrusted Sources: Risky Downloads
Acquiring apps, software, or files from unknown or unverified sources significantly increases the chances of spyware infection. Many third-party app stores and shady websites host applications embedded with malicious code designed to steal user data.
Pop-up Advertisements: Deceptive Clickbait
Clicking on pop-up ads, especially those offering free prizes, software updates, or discounts, can trigger a spyware download. Some ads contain malicious scripts that execute automatically, installing spyware in the background without requiring user interaction.
Email Attachments: Hidden Malware in Messages
Attackers frequently embed spyware in email attachments. Opening an attachment from an unknown sender can execute malicious code, allowing spyware to install itself silently on your system. Even seemingly harmless file formats, like PDFs or Word documents, can contain hidden exploits.
Malicious Links: The Trap of Fake URLs
Cybercriminals use misleading links in emails, messages, and ads to trick users into visiting infected websites. Once clicked, these links may download spyware directly onto the device or redirect users to phishing sites designed to steal personal information.
Drive-by Downloads: Automatic Infection Without Interaction
Some spyware infections occur simply by visiting a compromised website or viewing an infected email. This technique, known as drive-by downloads, allows spyware to install itself without requiring users to click or download anything. Even reputable websites can be compromised and unknowingly distribute spyware to unsuspecting visitors.
Phishing Links: Social Engineering Attacks
Phishing attacks use deceptive emails, fake login pages, or fraudulent websites to trick users into entering sensitive information. Often, these phishing sites also install spyware, allowing attackers to monitor user activity, steal passwords, and gain unauthorized access.
Infected USB Drives and External Devices
Spyware can spread through physical devices like infected USB drives, external hard drives, or memory cards. When plugged into a computer or mobile device, these infected drives execute malicious code, installing spyware automatically. This method is commonly used in targeted attacks against businesses and individuals.
Spyware infections can happen in an instant, often without any noticeable signs. Awareness of these infection methods is the first step in protecting your system from unwanted surveillance and data theft. Let’s find out how to identify spyware in your system.
How to tell if you have Spyware?
Spyware operates silently, making it difficult to detect until it has already compromised your system. However, by paying close attention to unusual behavior on your device, you can identify potential infections early. Here are the key warning signs that spyware may be lurking on your system:
Sluggish Performance and System Lag
One of the earliest signs of spyware infection is a noticeable drop in performance. If your device suddenly becomes slow, freezes frequently, or takes longer to respond, it could be due to spyware consuming system resources in the background.
Unexpected Pop-ups and Intrusive Ads
Spyware often works alongside adware, leading to a surge in unwanted pop-up ads, banners, or redirects. If you’re bombarded with advertisements—even when you’re not browsing—this could indicate spyware is active.
Unwanted Toolbars, Extensions, or Homepage Changes
If you notice unfamiliar toolbars, extensions, or changes to your homepage and search engine settings that you didn’t authorize, spyware may have modified your browser settings. These unauthorized changes can also lead to fake search results or redirects to malicious sites.
Excessive Battery Drain and Overheating
Spyware constantly runs in the background, tracking your activity and transmitting data. This extra processing load can drain your battery faster than usual and even cause overheating, especially on mobile devices.
Difficulty Accessing Secure Websites
If your login attempts on secure sites (such as banking or email accounts) fail the first time but work on a second attempt, spyware could be intercepting your credentials. This could indicate a keylogger or other data-harvesting spyware at work.
Unexplained Data Usage and High Network Activity
Spyware frequently transmits stolen data to third-party servers. If you notice a sudden spike in data usage or your internet connection seems unusually slow, spyware may be sending information without your knowledge.
Disabled or Non-Functional Security Software
If your antivirus software stops working, refuses to update, or won’t scan for threats, spyware may have disabled it to prevent detection. Some advanced spyware can even block access to security websites.
Browser Anomalies and Search Redirects
Persistent pop-ups, unwanted search engine changes, and automatic redirections to unfamiliar websites are strong indicators of spyware interference. If your browser behaves erratically, spyware could be manipulating your online activity.
Unusual Error Messages and System Alerts
Random Windows or system error messages, especially when performing simple tasks, can signal spyware corruption. Spyware may modify system files or cause conflicts that result in frequent crashes and warning messages.
Spyware Removal
Spyware removal is essential to protect your computer or device from the detrimental effects of malicious software. Here’s a guide on how to effectively remove spyware.
- Use Spyware Detection and Removal Software: Employ specialized spyware detection and removal programs or antivirus software with malware detection capabilities. These tools scan your system for spyware and other malicious programs, helping you identify and eliminate threats.
- Task Manager or Activity Monitor: On Windows computers, Task Manager allows you to identify suspicious programs consuming system resources. Similarly, on Apple systems, the Activity Monitor provides insights into running programs. However, some spyware may disguise themselves as system files, making manual detection challenging.
- Prevent Reinstatement: Spyware often has mechanisms to reinstall itself if your device is connected to the internet during removal attempts. To prevent this, consider unrooting or un-jailbreaking your phone to incapacitate the spyware. For iPhones, performing an iOS update can revert the device to an un-jailbroken state.
- Safe Mode or Airplane Mode: On Android phones, removing spyware is best done in safe mode or airplane mode to halt spyware activity and prevent network connections that may reinstall the spyware.
- Factory Reset: As a last resort, perform a factory reset on your iPhone or Android phone to eradicate spyware completely. Remember to back up your data before resetting and restore it afterward using Google or iTunes/iCloud.
- Use Reputable Removal Software: Utilize reputable malware and spyware removal software, such as Lavasoft’s Ad-Aware, Microsoft’s Windows Defender, Webroot’s SpySweeper, or Spybot Search and Destroy. Ensure the software comes from a trustworthy source like Kaspersky to avoid inadvertently installing more spyware.
- Multiple Scans and Cleanup: Perform multiple scans after removal to ensure all remnants of spyware are eradicated. Additionally, clean your internet cache to eliminate any lingering traces of the spyware.
- Enhanced Security Measures: After removing spyware, strengthen your device’s security by regularly running antivirus scans, updating software, and using strong, unique passwords for all accounts. Consider investing in comprehensive security solutions like CloudDefense.AI for complete protection.
Spyware Protection
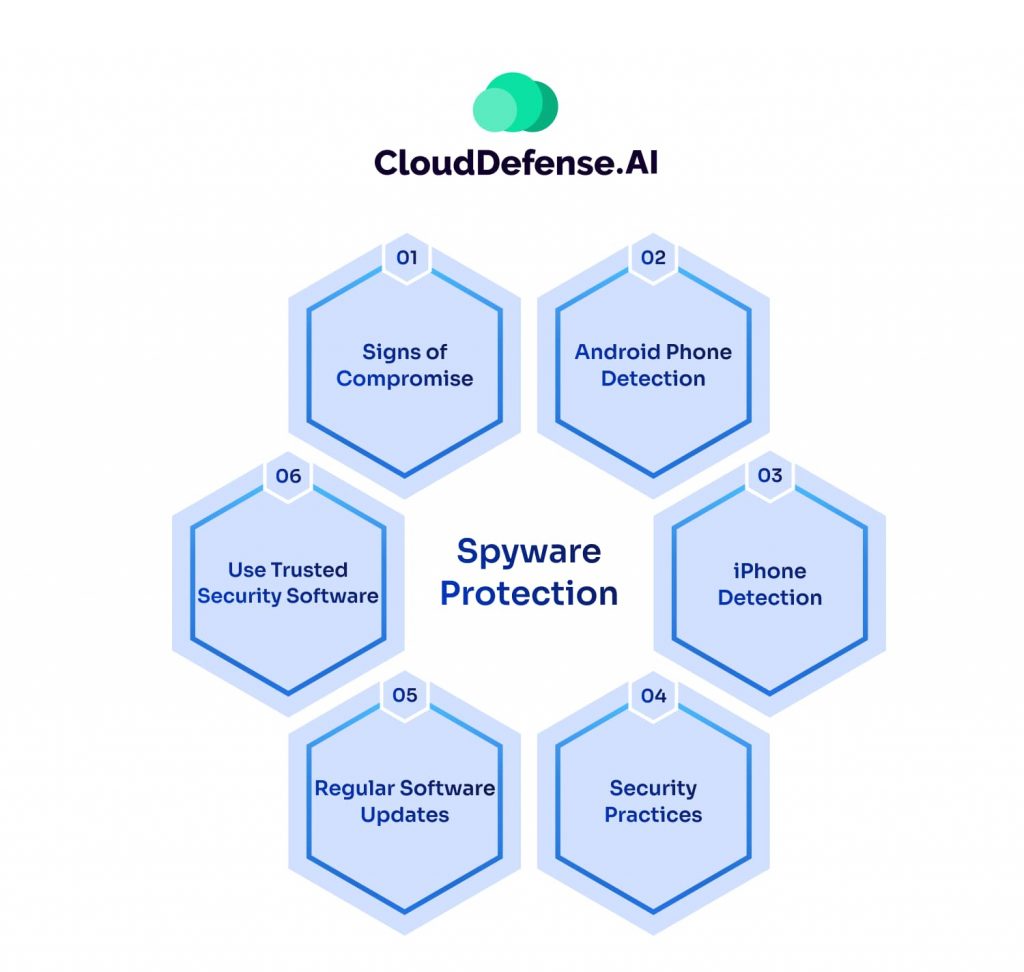
Spyware poses a serious threat to your privacy and security, often operating undetected while collecting sensitive data. Protecting your devices from spyware requires proactive security measures. Here’s how you can protect your systems effectively.
1. Strengthen Device Security
- Limit App Installations: Only download apps from official sources like the Google Play Store or Apple App Store to avoid malicious software.
- Disable Unknown Sources: On Android devices, ensure the option to install apps from unknown sources is turned off in your settings.
- Avoid Jailbreaking: Jailbroken iPhones are more vulnerable to spyware. If you see apps like Cydia installed and you didn’t jailbreak your device, your security may be compromised.
2. Be Cautious Online
- Ignore Suspicious Pop-ups: Never click on pop-up ads or install software prompted by unexpected pop-ups.
- Avoid Malicious Links: Don’t click on links in emails, messages, or websites unless they are from a trusted source.
- Be Wary of Free Software: Many free downloads contain spyware. Only install software from reputable developers.
3. Keep Software Updated
- Regularly Update Your OS and Apps: Updates fix security vulnerabilities that spyware exploits. Enable automatic updates whenever possible.
- Keep Security Software Up-to-Date: Ensure your antivirus and anti-spyware tools receive the latest threat definitions.
4. Use Trusted Security Software
- Install Reliable Anti-Spyware Software: Use trusted security programs to scan, detect, and remove spyware.
- Enable Real-Time Protection: Many security tools offer real-time scanning to block spyware before it infects your device.
- Run Regular Scans: Schedule full-system scans frequently to catch spyware that may have slipped through.
5. Secure Your Network & Accounts
- Use a VPN: A Virtual Private Network encrypts your internet connection, making it harder for spyware to track your activity.
- Enable Two-Factor Authentication (2FA): Protect your accounts with an extra security layer, reducing the risk of stolen credentials.
- Monitor Data Usage: Unexplained spikes in data usage could indicate spyware transmitting your information.
Conclusion
Spyware poses a serious threat, targeting critical data and systems of all sorts of companies and individuals. In the face of such a threat, It’s important to prevent attacks by staying updated with strong cybersecurity measures. In case of an attack, swift action is key. Victims need to recognize signs, conduct thorough scans, and remove spyware as soon as possible. With vigilance and preparedness, organizations can defend against the damaging effects of spyware.







