Nowadays, every organization tasked with securing customer data seeks compliance with System and Organization Control 2 as it helps shield sensitive data. It acts as a badge of trust and a security asset for organizations to provide confidence to customers and stakeholders.
As cyberthreats are getting more sophisticated with the advent of modern technology, SOC 2 is enabling organizations to implement robust security measures to safeguard all personal data. However, getting compliant with SOC 2 can be time-consuming, and it not only incurs a lot of resources but also capital.
But you don’t have to worry as SOC 2 compliance software eases up the task as it helps you prepare for the audit quickly, and that is at half of the cost. However, the plethora of software options can overwhelm and make the selection process cumbersome.
That is why we have done the analysis on your behalf and come up with this list of the 10 best SOC 2 compliance software in 2024. To streamline the selection, we have included many associated topics that will give you an in-depth idea about the SOC 2 compliance software.
So, without further ado, let’s dive in!
What is SOC 2 Compliance?
System and Organization Control 2 or SOC 2 is a cybersecurity compliance framework developed by the American Institute of CPAs, which provides guidelines for how an organization should manage their customer data. It is a voluntary compliance designed for service organizations or third-party services to ensure they securely store and process client data.
The SOC 2 compliance is based on five Trust Services Criteria: security, processing integrity, availability, privacy and confidentiality. Unlike other compliance frameworks, SOC 2 compliance is customizable.
It gives you the choice to design controls based on one or more principles of TSC, where security serves as the primary principle and stays compliant with the framework. Each TSC has its own specific requirement, and the organization has to design the internal control to meet those criteria.
An independent auditor performs a SOC 2 audit where it evaluates your security posture related to more than one Trust Services Criteria. The internal reports generated during the initial evaluation help the organizations, business partners and regulators how the organization is managing their data.
What is SOC 2 Compliance Software?
SOC 2 compliance software serves as a platform that helps organizations align their internal controls with the requirement of one or more TSCs and stay compliant with the framework. It is an automation tool that not only defines the internal controls and monitors them but also assists in listing information assets and streamlining compliance processes.
These tools are mainly tasked with protecting customer data from unauthorized access and also processing them in a secured manner. Importantly, it speeds up the SOC 2 audit process by automating most of the repetitive tasks, maintaining documentation, uncovering gaps and remediating all the issues.
A good SOC 2 software also provides security, stakeholders and internal auditors a complete visibility into the security and compliance posture of the organization.
From providing risk assessment, control mapping, and policy management to continuous monitoring, a SOC 2 tool offers numerous features. This software is primarily suitable for organizations that provide SaaS solutions, cloud based services or services that are related to handling customer data.
What to Look For in SOC 2 Compliance Software?
As you begin your search for the right SOC 2 compliance software, you will get confused regarding which tool to select. While your main priority is to evaluate the software’s capability to streamline compliance and audit processes, you should also check its other features. Here are the things that you should check:
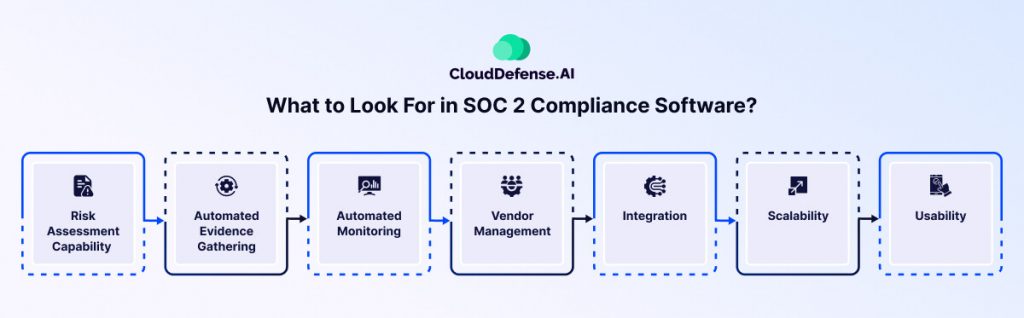
Risk Assessment Capability
Risk assessment is an important aspect that you should take into consideration because it will help uncover security threats that can make sensitive customer information vulnerable to attack.
Automated Evidence Gathering
Automation is a vital requirement for modern tools, especially SOC 2 tools, as it helps gather evidence, which will ultimately streamline and speed up the auditing process. Automating other repetitive tasks will save a lot of resources and help teams focus on other tasks.
Automated Monitoring
The SOC 2 compliance software you choose must come with automated monitoring. It will continuously look for issues and help ensure continuous compliance. Moreover, it will provide a continuous view of your compliance posture and mitigate any issue when it appears.
Vendor Management
Vendors offering various third-party services often serve as one of the primary sources of vulnerability that leads to security issues. The tool should offer scanning capability to help you evaluate the third-party vendor’s security posture and ensure it is free from vulnerability.
Integration
Pick a SOC 2 compliance solution that seamlessly integrates with your existing workflow, cloud service providers, platforms, ticketing solutions, and others. This will help you automate most of the primary compliance tasks and get an insight into the compliance.
Scalability
Scalability of the SOC 2 tool is another feature that you should assess as there are many frameworks whose guidelines and controls overlap with SOC 2. It would be best to opt for a solution that helps you comply with all the necessary frameworks.
Usability
When you are selecting a tool, you would obviously want it to be easy to use and have a simple interface that can be easily navigated. Make sure the interface is well laid out, and your employees won't have to go through a steep learning curve to get used to the tool.
10 Best SOC 2 Compliance Software in 2024
We understand it can be confusing to choose the right tool from the list of best SOC 2 compliance software. So, to simply the process, we have created a comparison table that lets you compare all the listed based on different criteria:
Software | Scalability | Centralized Dashboard | Key Features | Price |
CloudDefense.AI | Available | Available | 1. Faster scanning. 2. Covers complete application. 3. Audit ready report. 4. Risk assessment. | The price is available after booking a demo. |
Sprinto | Available | Available | 1. Real-time continuous monitoring. 2. Automated control mapping. 3. Evidence collection. 4. Incident management. | The price is available after you request a demo. |
Drata | Available | Available | 1. Automated evidence collection. 2. Auditor approved policies. 3. Continuous monitoring. 4. Policy documentation. | The price is available after you request a demo. |
Vanta | Available | Available | 1. Vanta-vetted auditor. 2. Continuous testing. 3. Complete visibility into background checks. 4. Custom controls. | The pricing of the Core package is available after a demo. |
Secureframe | Available | Available | 1. Dedicated audit support. 2. Continuous monitoring. 3. Custom policies. | The price is available after you schedule a demo. |
AuditBoard | Available | Available | 1. Simplified risk assessment. 2. Automated evidence collection. 3. Promote collaboration. 4. Automated issue management. | The price is available after you schedule a demo.
|
Hyperproof | Limited | Available | 1. Inbuilt SOC 2 template. 2. Automated task assignments. 3. Jumpstart. 4. Continuous monitoring. | The price is available after you schedule a demo |
LogicGate | Available | Available | 1. Risk assessment. 2. Cross-team collaboration. 3. Compliance gap identification. 4. Third-party risk intelligence. | The price is available after you schedule a demo |
Thoropass | Limited | Available | 1. Detailed documentation. 2. Auditor-approved integration. 3. Risk register. 4. In-house auditor. | The price is available after talking to the company’s expert. |
OneTrust | Limited | Available | 1. Automatically build a policy list. 2. Inbuilt guidance. 3. Automated risk assessment. | The price is available after you request a demo. |
If you have gone through the comparison table, it is time to get a detailed review of all the top SOC 2 compliance software based on our extensive research.
CloudDefense.AI

CloudDefense.AI 
CloudDefense.AI is undoubtedly your ultimate SOC 2 compliance software that not only helps you with comprehensive compliance management but also keeps you SOC 2 compliance-ready.
It keeps your internal controls aligned with the SOC 2 framework guidelines and keeps your compliance ready. CloudDefense.AI leverages advanced automation and scanning capability that accelerates your SOC 2 certification and ensures you won’t face issues during an audit.
With this tool, you get the chance to mitigate all the threats that, in return, help in enhancing your overall security posture. Once you integrate this tool, you won’t have to look back as it automates most of the process and meets all the guidelines.
Features
Here are some vital features that make CloudDefense.AI as one of the best tools for SOC 2 compliance:
Quick and Extensive Detection
This SOC 2 compliance solution is capable of uncovering macro and micro breaches quickly and delivers better performance than NVD. It can quickly identify breaches and enable security teams to mitigate them before they can cause compliance violations.
Maintaining Continuous Compliance
CloudDefense.AI offers continuous monitoring to ensure continuous compliance with the SOC 2 framework. It also conducts occasional audits that not only help maintain compliance statutes but also ensure internal controls are properly aligned with TSCs. Through continuous monitoring it identifies and mitigates security threats that can hamper the sensitive data.
Real-Time Insights
It provides you with real-time insight into your compliance posture and checklists, enabling your security team to make necessary changes. Moreover these insights come highly helpful for teams for audits and reporting.
Audit Ready Reports
A highlighting feature of CloudDefense.AI is its ability to generate audit-ready reports that are highly useful during yearly SOC 2 audits. Most importantly, it helps you create customizable reports according to the principles of TSCs you adhere to.
Unified Dashboard
It provides you with a single dashboard to help you keep an eye on your internal security controls and also get a holistic view of your security posture.
Pros

CloudDefense.AI, through effective compliance management, keeps your SOC 2 audit ready.

Helps in identifying security breaches quickly and effectively.

Through automated continuous monitoring, it helps in ensuring constant compliance towards SOC 2.

Speeds up the SOC 2 audit process through detailed reporting and documentation.

It automates a lot of compliance tasks to ensure proper use of resources.
Cons

It might not be suitable for a small scale organization with a limited budget.
Don’t just take our word for it. Book a demo and witness firsthand the power and simplicity of CloudDefense.AI.
What Sets Us Apart
CloudDefense.AI is often considered as one of the best SOC 2 compliance software due to its unique set of features, and they are:
Proactive Scanning
This tool makes use of proactive scanning capability that can discover various micro breaches and mitigate them before they make customer data vulnerable.
Critical Update First Approach
One of the defining features of CloudDefense.AI is its critical update first approach where it highlights all the updates along with identified vulnerabilities.
Sprinto

Sprinto
When it comes to choosing the best SOC 2 compliance software, Sprinto appears as a top choice. With its streamlined audit frame and features like automated evidence collection, this compliance automation solution helps you breeze through your compliance journey. The main aim of this software is to not only help you achieve SOC 2 compliance but also maintain it by providing real-time visibility and continuous monitoring.
Pros

It automatically maps all your internal controls to the applicable TSC criteria.

Sprinto gives you granular visibility into your critical data through regular monitoring and provides automated alerts.

It streamlines the audit process by automating setup, follow-up, cataloging, evidence collection and other tasks.

The audit dashboard makes it easy to collaborate with the auditor.
Cons

The cloud-based system is highly resource-intensive.

The service data isn't stored in trial mode.
Drata

Drata
Drata is truly a top-notch SOC 2 compliance software that helps you navigate your SOC 2 journey in a fast and frictionless way. This platform is designed by experienced security experts and auditors to make sure you have no hassle while maintaining compliance. Through automation and continuous monitoring, it not only accelerates the compliance process but also helps you in building trust.
Pros

This tool makes use of automation for evidence collection, asset tracking and access control review to reduce compliance cost.

Drata comes with an inbuilt risk assessment along with auditor-approved policies.

It provides insight into policy enforcement and denied entries.

It provides you with real-time security reports that help your security team respond to issues hampering security posture.

Impressive customer support with experienced compliance experts.
Cons

The add-ons are not covered in the subscription.
Vanta

Vanta
Another top SOC 2 compliance software we like to present is Vanta and it is designed to help SaaS organization achieve and stay compliant. It is a powerful platform that with its experienced auditor helps you accelearthe te SOC 2 process to success. Vanta automates most of the tedious tasks and also helps in staying compliant to framework through continuous monitoring, task tracking, and managing policies.
Pros

Vanta offers a centralized dashboard to provide you with complete visibility into employee status.

Strengthens the security posture through automated access control review.

Helps in ensuring auditor approved internal controls and policies to stay compliant with TSCs.
Cons

It doesn’t offer a wide range of integration options.

You won't have much support for remediating issues.
Secureframe

Secureframe
Trusted by the world’s most renowned audit firms, Secureframe empowers businesses to achieve SOC 2 by automating every step of the process. It provides an all-in-one framework through which you can manage risks, create policies, manage security posture, and train your employees. One of the best aspects of this platform is that it makes onboarding and offboarding employees easy through thorough checks and policy acceptance.
Pros

It offers efficient vendor risk management by continuously reviewing vendors and performing due diligence.

It helps you create your security policies that align with the principles of TSCs you comply with.

Secureframe offers automated evidence collection and continuous monitoring to ensure all the requirements are met.

Offers all the necessary SOC 2 resources.
Cons

It requires a steep learning curve.
AuditBoard

AuditBoard
Another top SOC 2 compliance software that needs your attention is AuditBoard. From managing risk assessment and automating evidence collection to managing compliance issues through automation, AuditBoard serves as a one-stop audit solution for your organization. It brings together internal controls and policies in one place to empower your organization to continuously meet compliance requirements.
Pros

It provides standardized risk assessment templates to dynamically score and rank risks.

Lets you manage roles and permissions according to POLP to rightsize the permission to critical data.

It automates evidence collection by scheduling send requests to stakeholders.

Provides a central location to store audit trails between audits and stakeholders.

The platform is completely user-friendly.
Cons

The performance might decline when this solution has to assess a large volume of customer data.

Integration issue with third-party tools.
Hyperproof

Hyperproof
With Hyperproof, you can not only ease up your SOC 2 certification process but also automate all your compliance tasks to streamline your journey. It helps you achieve SOC 2 compliance by automating evidence collection, leveraging the SOC 2 program template, automating task assignments and visibility into your compliance posture. The powerful integration capability of this platform makes the compliance journey much smoother.
Pros

It provides built-in SOC 2 program templates along with controls and requirements to ease up the journey.

Supplies educational resources and provides training to employees to speed up the compliance process.

It comes with an intuitive dashboard that provides visibility into your compliance posture.
Cons

Some automated tasks have some limitations.

You won’t get an array of integration in comparison to competitors.
LogicGate

LogicGate
LogicGate is a popular risk and compliance management solution that helps organizations prepare for SOC 2 compliance and maintain compliance throughout. Through its proprietary Risk Cloud feature, it identifies compliance gaps, eliminates redundant controls, quantifies risk and reduces compliance by integrating third-party intelligence. It provides you with a centralized platform to help you cater to all your compliance needs.
Pros

Provides easy cross team collaboration with reporting, centralized control repository and risk registry.

It puts a strong emphasis on vendor risk management.

It helps you identify all the gaps in your compliance posture by helping you modify the SOC 2 program architecture.

It lets you stay ahead of all the risks: automated workflow, risk intelligence and automated evidence collection.
Cons

You won’t get a lot of customization options.
Thoropass

Thoropass
Transform your complicated SOC 2 compliance process with Thoropass and make it a seamless and predictable journey. This SOC 2 compliance solution consolidates automated evidence collection features, in-house auditor, risk registry, and auditor-approved integration in one platform. Most importantly, through this solution you can not only manage your compliance and security posture but also monitor them continuously.
Pros

It serves as an all-in-one platform through which you get complete visibility into your SOC 2 compliance and security stance.

You get the support of an in-house auditor to ensure there is no compliance gap.

It automatically collects evidence to streamline the SOC 2 audit process.

You get the choice to build a custom roadmap to stay compliant with SOC 2 continuously.
Cons

The platform can be overwhelming for new employees and requires a lot of knowledge.

It is mostly designed to cater to small businesses.
OneTrust

OneTrust
Accelerate your SOC 2 compliance journey with OneTrust and build trust with your customers and stakeholders. It lets you prepare for SOC 2 auditing processing in a seamless manner by streamlining evidence collection, supporting data insight, mapping controls for framework and enforcing pre-built policies. Besides, it also lets you automate risk assessment and integrate your tech stack to extract evidence that will help comply with the controls.
Pros

OneTrust automatically builds a list of policies and controls that align with your organization's requirement for SOC 2 compliance.

It is completely scalable and adapts to the increasing size of the dataset.

The platform offers inbuilt guidance that helps you navigate through various compliance requirements.

It automates your risk assessment, vendor risk assessment and readiness assessment and speeds up the whole process.
Cons

The subscription plans are expensive for small-scale businesses.

The interface can be difficult to handle at the beginning.
Conclusion
Modern organizations are turning to SOC 2 compliance software as it accelerates their SOC 2 compliance journey and helps them to stay compliant throughout. Most of the SOC 2 compliance software comes equipped with automation that not only saves time on manual monitoring and evidence collection but also helps organizations save money.
To help you find the right SOC 2 compliance solution for you, we have compiled a list of top tools that can help you with SOC 2 compliance. All the tools we have researched for you come with a long list of features that streamline up your compliance journey and help you avoid compliance violation fines.







